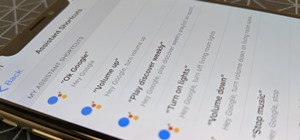
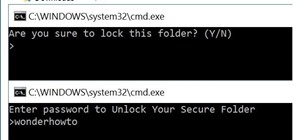
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our moderators and contrib ...more
In this video from AppleGenius0921 he shows us how to connect and set up a Rocport 9CX external hard drive to your Mac. You can connect with 800 or 400 firewire. Take the 800 firewire cord and connect it from the hard drive to the Mac firewire port. Now the Rokport will power ...more
Laptops are almost a necessity in today's society. It doesn't help that a laptop that can actually increase your work productivity will put at least a $1,500 dent in your wallet. I'm sure you have searched around to try to find factory direct deals, or (shiver) even looked at ...more
Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, ev ...more
Digidesign has transitioned all of their plug-in software copy protection from floppy drive based key disks to copy protection authorizations that reside on the iLok technology provide by PACE. The following is some information about iLok technology. The iLok USB Hardware Key ...more
This Weekend Project is the USBattery from MAKE Magazine Volume 16. Conceal a flash drive in a AA battery! This is a way cool USB battery mod or hack project. It makes a cool secret storage space for your spy projects. Wear gloves, safety goggles and a non alkaline battery.
Staying organized with your digital music library can be frustrating, especially when you're downloading songs on different devices. Transferring music files to one central location doesn't have to be hard though, even when you download music on your Android mobile phone. So h ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
In this tutorial, learn how to copy an original Wii game to a USB or an external harddrive without using a computer. This is helpful if you are sharing games with someone else, or if you would like to create a backup of your current Nintendo Wii games. You can also use this pr ...more
This silent video shows you how to install HP printer drivers for Windows XP. Start off by turning on the power on the printer. Do not connect the USB cable to the computer yet, it'll ask you at a later time. Now go to HP's support webpage by typing "www.hp.com/support" on you ...more
You store everything on your computer's hard drive… precious family photos, your favorite music and video files, valuable financial information, and let's not forget about all that porn (just kidding). You can't back up your data when it crashes, so don’t wait another day to p ...more
Video: . Recycle your hard drive into a hidden flash memory device that only you know how to turn on and use in secret. This DIY hack project allows you to recycle your broken hard drives back to life and turn them into something useful. So far, this project has several funct ...more
The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it. Security starts with a fingerprint reader on the side of the 2710p, boosted with an optional Smartcard slot for a true combined physical barrier. The biom ...more
When you buy computer parts, it can be a tough decision where you want to put all of your hard earned dollars into. Not only that, but when you buy a top of the line component, 3 months later (at most), your hardware will likely be outdated. This puts consumers like us in a bi ...more
If you're a certified computer nerd along the lines of NASA scientist Howard from "The Big Bang Theory," then you know how frustrating it can be transferring large amounts of data between an external hard drive or other drive and your main computer, especially when you're in a ...more
Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be comp ...more
BitLocker. What is it? And what can it do for you? Well, it's a handy new feature built-in to Windows 7, and it can help protect all of your data from loss, theft, or hackers. It's the easiest way to make sure your documents and files are safe from the devil's hands. Improved ...more
Windows 7 can be purchased online and downloaded. From the downloaded files you can create a bootable DVD. Three files are downloaded: An executable 64-bit Windows file and two .box files. Move all files to a new folder "w7p" and put the folder on the C drive. You have to down ...more
First buy a cheap rc buggy, then a cheap wireless camera and receiver off ebay. Then buy a usb TV box and plug it into your laptop. Connect receiver to tv box. Tape camera to car. Switch everything on and drive! My other camera has packed up and I can't see anything through th ...more
Designer Brenden Macaluso's Recompute is an eco-conscious desktop PC constructed with sustainable cardboard. Everyone knows you're not supposed to get electronics wet, but seriously, you really better keep this one dry. Via I.D. Magazine: "This working desktop computer featu ...more
Sometimes it's necessary to format your memory card in your mobile phone or digital camera, just like you need to format a hard drive, because of virus problems or slower speeds. This video will show you the steps to formatting (or reformatting) the SD memory card for a cell p ...more
This is a very simple, but very funny prank to play on your friends using Windows. Creating the file Begin creating this prank file by opening up a text document in your word editor program. Once you have opened the text document copy this into the document: do msgbox"wha ...more
The Ubuntu CD does not contain much in terms of software applications. So how can we incorporate other programs that would be made available after booting from a live CD? There is a program called Remastersys. This program creates an .ISO image of the Linux system installed ...more
Just installed a new hard disk on your PC, but Windows was unable to detect it? Download Ubuntu A new hard disk requires that you create a partition table before you can do a format. Download the Ubuntu Desktop CD 10.04LTS 32bit x86 for Intel users. Tips The Live CD won't ...more
Products with dual capabilities make life easier, allowing us to carrying around one less electronic device. The PlayStation Portable does just that. You not only have hours of entertainment with hand-held games but can store music for on the go as well! The PSP, or PlayStati ...more
Get Google Chrome Download and install Google Chrome. Get Rohos Mini Drive Download and install Rohos Mini Drive. Open Rohos Mini Drive Open the Rohos Mini Drive main window and create an encrypted partition by clicking on Setup USB Key link. Tips Without first creating ...more
In this video tutorial, viewers learn how to completely format a hard drive. Begin by downloading the Knoppix Live Boot CD. Then burn the newly download ISO onto a CD as a bootable disc. Use your BIOS to tell your computer to boot from the CD-ROM instead of the hard drive. Wit ...more
In order to put music on your iPod, you will need the following: a CD, a USB, an iPod, and iTunes. Place your CD in the CD drive of your computer. Select "Yes", when it gives you the option to import your music into your iTunes library. You will be able to see it importuning ...more
Compared to Apple's products like the iPhone and iPad, Android phones and tablets are very flexible devices. For instance, you can set a new home screen, replace the lock screen, or even beam files using NFC — but that's just the software side of things, and the flexibility go ...more
The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for ...more
Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice t ...more
If you've got more than one computer, it can be a huge pain to switch form one to the other. Between files, settings and apps, it can take a while to transfer everything—and if you're running different operating systems, it's even worse. Image by Onion A new feature on Window ...more
Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network. There are services out ...more
When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used. Recently, the developers at Team Eurek ...more
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
One of the most common complaints about the Nexus line of devices is that they don't have expandable memory. Phones like the Galaxy S5 and the HTC One M8 have a microSD card slot that allows you to easily add extra storage space for movies, music, and photos. The Nexus 5 has ...more
A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge. The goal in this article is to acquire a target's .plist file which contains the ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a compute ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored compute ...more
Have a PC but hate Windows? Maybe you've just heard a ton about the new Mountain Lion OS X and want to see if it lives up to expectations. Either way, you can install Mountain Lion on your Intel-based PC in a few easy steps. All you need is a copy of the OS X and an 8 GB USB f ...more
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget yo ...more
It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge. Continuing with our situational awareness attacks, we'll be further orie ...more
It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept. In bot ...more
The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there a ...more
Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess. So, I decide ...more
If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out. Let's say there's a router that we need to know the password for, and we have physica ...more
No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly! I hope you had a good Christmas and happy new year! Update1: Added the section "weaponizing your Android" where I talk about apps and fundamental Kali ...more
It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or ...more
Bigger and faster. Two words that are pretty much always wanted no matter what the scenario is. The new PlayStation 4 has been out for only a few hours now and people are already looking for ways to one-up their friends and upgrade their already awesome systems. The PS4 ships ...more
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac u ...more
Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering. One such distribution is Pentoo, a Gentoo-b ...more
The fifth annual Amazon Prime Day is upon us. Starting July 15, Amazon will offer thousands of deals on products across its site, kicking off at 3 a.m. EDT. This year, it will only run for 48 hours, so you have even less time to act. To save you some of that time, we made a li ...more
Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking proces ...more
Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free. But there's been a lot of confusion about which older versions of Windows will be eligible for the free update, and some unce ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
As someone with a pretty nice TV, I've never found the allure in purchasing a projector. While they're certainly smaller and sleeker than a television, and more portable, they can be pricey and produce a less than stellar image. And who really buys a projector anyways? They're ...more
What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system. Understanding the Attack Whi ...more