The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fi ...more
Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go ...more
If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against ...more
Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, ...more
Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary fl ...more
So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it. To me, the ...more
Monitoring your storage space is always a nuisance, whether you have a desktop, tablet, or smartphone; having enough space for all of your files, music, and videos is a constant battle. One movie file can take upwards of 1GB of memory, and for people who travel a lot, it becom ...more
We've had the pleasure of test driving the ASUS Transformer Book T100T for the last couple of weeks, and for a $400 Windows 8 machine, it's impressive to say the least. Now don't get me wrong, a Surface Pro this is not. But unless you plan on heavily gaming or doing other pro ...more
Hello guys, its been quite a while since my last post. (sorry for the lack of images) Well I guess I'm first up on the review board :P. So first thing to say: I ran USB persistence on Kali 1.10 by creating a persistence partition on my 16 GB drive. As for me, I had to delet ...more
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of i ...more
After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimiz ...more
If you've just upgraded to an HTC One M8, chances are you've got some media files you want transferred over from your computer or previous phone. Even after you've done that, there will be times when you want to transfer content back to your computer for safe keeping. The old ...more
Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial ...more
Android 5.0 "Lollipop" has only existed for a few months, but a leaked version of Samsung's take on the firmware has already been spotted in the wild. This update came straight from Samsung, and brings with it a plethora of new features, including greatly improved performance ...more
There is thousands of motor driver, do you find an easy way to measure the drive current? That is what this motor shield do. The drive chip is L298N. The following steps is how to control two DC motors and how to measure the drive current. With it, you will make your control s ...more
Linux may not be the most popular consumer operating system out there, but what it lacks in consumer app variety, it definitely makes up for in flexibility and security. And if you've ever tinkered with a Linux distro, you know how easy they are to install—most of the time, I ...more
Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an imag ...more
Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of har ...more
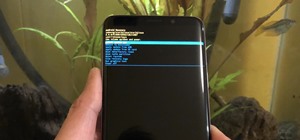
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physi ...more
This is a illuminated pen holder that I made out of a couple recycled hard drives. The LEDs receive power from the standard USB cable connected to a computer. The stand for the penholder is taken from a clip light, and the penholder itself is made from 3 hard disk drive platte ...more
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful. Norway-based Yara International ASA, a self-touted "Tesla of the seas," claims the eletric-powered vessel will be the world's ...more
For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been ...more
With MP3 players all but dead, phones are now the dominant portable music devices. While smartphones have gotten better at this task over the years, they do have some glaring limitations when it comes to music. On the bright side, we can use these limitations to help find the ...more
If you live in the US, it's pretty simple: The Google Pixel 4a is the best phone for rooting and modding in 2020. Its price keeps the risk-reward ratio nice and low, and its unlockable bootloader makes it easy to modify virtually any aspect of Android. But recent updates to A ...more
Converting Movies To Psp Format. Hey again, this is a real quick guide for anyone interested to get a movie onto there PSP without all the fluff i have seen elsewhere. I just watched Africa the Serengeti on my PSP and heres is the lowdown. Movie - approx 40 minutes - dvd Sav ...more
Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the r ...more
No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and eve ...more
Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without hav ...more
If you are among those lucky ones who got a chance to pickup the Yu Yureka from Amazon and looking for a detailed guide on how to root your yureka, then I doubt that there is any better place than this. You might have visited some XDA threads for the same but those are general ...more
One of the lesser known features brought along by the roll-out of Android 4.4 KitKat is the ability to screen record from within the device. This features isn't overtly obvious, nor is its implementation the most streamlined, but if you were ever looking for a way to capture v ...more
Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might b ...more
Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good t ...more
If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and no ...more
In July 2017, LG announced a new smartphone lineup, the Q series. These devices focus on providing some flagship features at a more affordable cost — features such as an 18:9 1080p display. LG's goal here seems to be adding value for the more budget-conscious users, and in 201 ...more
With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world. As th ...more
There are some important new features in the Photos app on iOS 17 and iPadOS 17 that will streamline editing, give your pets more recognition, help you learn about the world you've captured, and even add a bit of fun to your day. There are even a few hidden tricks that may sur ...more
The Pixel 5 is a great value proposition in this era of $1,500 phones. With its reasonable price tag, fully open-sourced software, and unlockable bootloader, it's also an ideal phone for rooting. The process of rooting the Pixel 5 is a tried and true method: Unlock the bootlo ...more
This step-by-step video tutorial shows you how to install CHDK onto your Canon digital camera. CHDK is a firmware enhancement that operates on a number of Canon cameras. CHDK gets loaded into your camera's memory upon bootup (either manually or automatically). It provides add ...more
Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecur ...more
Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn ...more
The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant b ...more
The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practic ...more
If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning e ...more
In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux. With each Pi more powerful and cheaper than the last, the addition of the Pi Zero in 2015 too ...more
If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock ...more
It's somewhat funny that the HTC ThunderBolt smartphone would be released around the same time as Apple's new Thunderbolt technology. Mainly because HTC's smartphone isn't exactly something I would compare to a flash of lightning, which averages around 60,000 miles per second. ...more
Back up your computer data and save your time, money and valuable information using these helpful tips. There are several options to backing up and storing your important data, ranging from tiny keychain USB drives to backing up your files online. This informative and lighthea ...more
In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents f ...more
Many video camera companies are beginning to manufacture tapeless camcorders, which record footage as files on hard disks, solid state drives, or optical disks. It's easy to transfer file-based footage to your Mac using Final Cut Express. Just connect your camcorder to the USB ...more
Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems usel ...more
The first thing anybody really thinks about after watching Rear Window is how much they want their own telephoto lens. These days, they aren't cheap, so how do you go about spying on your neighbors without putting down so much dough? You can simply build one yourself for arou ...more
The first day of Hanukkah is here, the day you start lighting the candles of the menorah. So, why not ditch the wax and light the "lights" this year? (Skip ahead to see the LED menorah) Hanukkah is a Jewish festival that lasts eight days from the 25th day of Kislev, which th ...more
In this Video Games video tutorial you will learn how to fix a PS3 Black Screen of Death. For this you got to put the PS3 into stand by mode. Press down the button located at the top end of the console for 7-10 seconds and listen for 3 beeps. Repeat this step again. Then this ...more
In this Video Games video tutorial you are going to learn how to flash the Benq VAD6038 Xbox 360 DVD drive. This video will show how to do this with the connectivity kit and the jungle flasher. You will need a compatible card for this. VIA 6421a SATA PCI card is probably the b ...more
In this video tutorial, Mike shows how to find a missing file in Windows XP and Vista with three different options. In the first option, open Windows Explorer or My Computer. Then open the recycle bin to check for your missing files. If you don't see your file there, close the ...more
The video is about making a ISO file or a disc.To enable this you must have ISO installed on your system.The video begins by opening the Image burn setup wizard file.Once you have opened it , keep clicking next until you are finished with the installation. Then you have to ins ...more
Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But w ...more
Don't jeopardize your memories. Learn how to preserve your old home movies by digitizing your VHS tapes. You Will Need * A capture card * A computer with movie-making software * A VCR * RCA cables * An external hard drive Step 1: Purchase an external or internal capture card ...more
New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software. There are many different ways to classify viruses, and each of t ...more