In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encrypti ...more
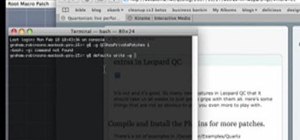
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
The producers of FX's animated series Archer have devised a plan to introduce augmented reality hijinks into its eighth and penultimate season with a new app for iOS and Android devices. The Archer, P.I. app allows fans to sleuth alongside the alcoholic playboy spy-turned-pri ...more
Just as expected, Apple pushed out iOS 14.3 to the masses on Monday, Dec. 14, which coincided with the pumped-up release of Fitness+, Apple's subscription workout service for Apple Watch users. It also came one day before the new AirPods Max hit buyers, and the iPhone needs iO ...more
Apple has their regular iPhone 11, then two higher-end "Pro" models. Samsung went the other way — they have the Galaxy S20 and S20+, then there's the S20 Ultra. But one thing these smartphone lines do have in common is the base model flagship. How do they compare? Where the i ...more
We've been predicting the rush of augmented reality wearable makers from China for a couple of years, and now it looks like it's in full swing, with one of the most promising entrants coming from startup Pacific Future. The China-based company was on the CES show floor this w ...more
A year after making a splash at the annual Consumer Electronics Show in Las Vegas with Amazon Alexa integration, smartglasses maker Vuzix is bringing a notable weather app to its Blade smartglasses for the 2019 edition of the conference. Vuzix has announced that its Blade dev ...more
As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T. In addition to the investment, AT&T will serve as the exclusive wireless distribution partner for the consu ...more
When the Nintendo 3DS XL came out, I traded in my regular sized Nintendo 3DS for one — but I ended up hating it. The XL just felt big and unwieldy, and because the screens were larger (with the same resolution), it ended up looking blurrier than the regular 3DS. This, to a les ...more
Google and Samsung are the biggest players in the Android world. Despite a rocky launch, Google's Pixel 2 XL became one of the premier Android devices of 2017, headlined by fast performance and a pure version of Android. Still, many users prefer Samsung's offerings, and their ...more
The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week. The premise should be familiar to anyone who has followed augmented reality over the past year, and likely old hat to those who t ...more
Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended. It was an average-at-best device sold at an artificially high price to arouse consumer interest ...more
If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can us ...more
Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians acro ...more
While the adoption of Apple's newest mobile operating system, iOS 8, was smoother than its predecessor, there were still a lot of bugs and features that needed ironed out. There were lost cellular signals, missing Camera Rolls, a confusing iCloud Drive, and no functioning Appl ...more
Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by comput ...more
Update (Fall 2020): Samsung's version of Android 11 is already in its testing phases! One UI 3.0 is expected to hit recent flagship Galaxy devices towards the end of this year, so check out the new list of features: New Version: All the New Features & Changes in Samsung's One ...more
Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming. After much thought — and ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more
When it's all said and done, it doesn't really matter who did it first — the more important question is who did it best. Still, it's nice to know who's really responsible for groundbreaking innovations in the smartphone space. I always try to stay neutral and objective, but w ...more
UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Bel ...more
Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari. The iPhone's default web browser has cool new features like ...more
Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associa ...more
In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential v ...more
Last year, many were caught off guard when Google released a midrange Pixel device. It was quickly crowned the best value-buy phone on the market, as it brought most of the camera tech people loved in the flagship Pixel for almost half the cost. Google's 2020 entry in this ser ...more
5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they act ...more
With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy ...more
Despite making great phones for years, Sony continues to struggle to penetrate the US market. Sales volume has fallen year after year, with 2019 limited to only 5 million units sold globally. To help alleviate this drop, last year, Sony released the Xperia 5, the return to com ...more
As one of the leading makers of processors for smartphones, Qualcomm further bolstered its place in the market with the announcement of the Snapdragon 865 earlier this week. On Thursday, the company took yet another step towards the future of augmented reality headsets and sm ...more
Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers. Meanwhile, Magic Leap, YouTube ...more
If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?" Many of the top names in the industry from the 2018 edition remain the same, but their positions have shuffled. The p ...more
Samsung decided to shake things up this year. In the past, the Galaxy Note series was one large phone. This year, it's two phones: the Galaxy Note 10 and Note 10+. So for the first time in a long time, we can compare the latest standard iPhone, the 11 Pro, to a Galaxy Note dev ...more
For the first time in a while, the battle between Samsung and Apple is really interesting. Unlike previous years where the choice for smaller hands was limited to the Galaxy S series, this year, there's an option for Galaxy Note users. Both sides of the aisle have their best o ...more
Every fall, we can expect a few things: leaves changing colors, cooler temperatures, and Samsung and Apple releasing new phones that fanboys and fangirls will argue about until the following year. This year, Samsung is mixing it up, releasing two phones in the Galaxy Note seri ...more
Amazon Prime Day is nearly here, but that doesn't mean the deals are a mystery. Sure, most of Amazon's best sales and discounts won't be announced until Prime Day itself, but we already know some awesome smartphone deals thanks to a handful of early sneak-peeks. If these prev ...more
During Huawei's P30 smartphone launch event on Tuesday, the China-based company unveiled a surprise addition to its line-up: smartglasses. The device is launching in partnership with South Korean fashion eyewear company Gentle Monster. Don't Miss: Snap Rolling Out New Specta ...more
Despite Huawei's ongoing battle with the US government, the Chinese company has continued to release phones in the US under its Honor brand. The Honor X series has been consistently released for several years, offering midrange specs at ridiculously low pricing, and the Honor ...more
With this year's iPhones, Apple built upon the success of the iPhone X in a somewhat iterative manner. All three phones borrow from the 2017 flagship's design, which many praised as being the best in years. They also tried to help those of us who don't have more than a grand t ...more
Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of sk ...more
In 2018, Motorola is no longer the same brand that introduced the world to the Motorola Droid. The once iconic company is now part of the "Others" group, scrambling for fifth place. The newly-announced Moto Z3 perfectly embodies their current state with competitive specs ... i ...more
While Sony as a company is well-known in the United States, it smartphones are not. For years, Sony has stuck with a boxy design with sharp edges and large bezels — however, they're finally getting with the trends. As a result, the Xperia XZ2 Premium offers a rare combo: A sup ...more
We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privac ...more
The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that wi ...more
Huawei's sub-brand, Honor, just announced a pair of new smartphones to help close out the year. We knew the midrange Honor 7X was on its way, but what came as a surprise was the announcement of the Honor View 10 and its impending release in the US. Thanks to Honor, US customer ...more
There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take c ...more
Russian phone customizer Caviar — you might have heard of the blinged-out iPhone 6s Pokemon GO phone they released a few months back — is taking on international relations with their newest product. To commemorate the G20 summit currently ongoing in Hamburg, Germany, Caviar i ...more
Anticipation is building for the release of the Essential Phone. Andy Rubin's newest creation is expected to be loaded with features like a rear fingerprint reader, attachable 360-degree camera, and an edge-to-edge display. However, a news release from Sprint has just revealed ...more
After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device. La ...more
At an event in Mountain View, CA, and watched by fans via live stream on YouTube, Google announced a slew of new products today. Over the last few weeks, there was no shortage of rumors and leaks about what might be unveiled, but now the secrets are out. As expected, Google h ...more
With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile bankin ...more
After months of speculation and sifting through rumors, Samsung finally unveiled its Galaxy S7 and S7 edge flagships, and they're pretty much what we had been anticipating. But just because there weren't any major surprises doesn't mean that it's not still exciting. Let's have ...more
Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targe ...more
The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't st ...more
Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes ...more
For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and ...more
When the specs for Google's Nexus 4 came out, most critics were more than thrilled. A very fast processor, lots of RAM, a big display with very high resolution, and an 8MP camera made it the media darling of the smartphone world. It climbed the ranks of the best smartphones av ...more
There's nothing like buying an awesome new gadget, but it leaves you with one problem (besides an empty wallet)—what do you do with the ones you already have? There are plenty of ways to put your old gadgets to use, but if you'd rather get rid of them, you may as well get some ...more
Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long ...more
When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular p ...more