It's that time of the year, y'all—when the air becomes crisp, the nights grow long, and people crave hearty, warm soups and stews. And of all the season's offerings, my hands-down favorite has to be chili: It's versatile, meaty, and above all else, it's damn easy to make. (Tha ...more
Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker c ...more
The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — s ...more
This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but ...more
As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading. If you are in Android user, then you ...more
If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you ...more
The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks. For one, most apps and games ...more
I have a theory that chocolate chip cookies are the gateway drug to cooking. The recipe is easy, no special equipment is required, and at the end, you get warm, fresh-from-the-oven cookies that are simply irresistible. It's how I got hooked on baking and cooking, and anecdotal ...more
In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents f ...more
Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often ...more
You'd be hard-pressed to find a working Super Nintendo in someone's house nowadays, but back in my adolescence it was gaming heaven. But now there's no reason to have an SNES console at home, because there are so many ways to play those retro games without one. All it takes is ...more
With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static. As someone who sends text message every day on my Samsung Galaxy Note 2, I get overwhelmin ...more
To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the f ...more
If you're feeling stressed, there are many home remedies you could use for relief. Meditation, yoga, acupressure, an ear massage, more sleep, shower soothers, playing video games… the list is endless. But a lot of these methods require a significant amount of time, so what do ...more
Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal. The terminal is a key component of any pentester's setup. We're going to be spending a lot of time wo ...more
Who here binges TV on a regular basis? I know I do. Never before have we had so many options for watching our favorite shows, especially when you consider how easy it is to stream from anywhere on a mobile device. But sometimes, all that choice gets a little overwhelming. What ...more
The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe. When you're connected to a Wi-Fi network, internet speeds are general ...more
One of my favorite things is finding an easy way to make what is normally a complex dish. Case in point: pasta sauce. Usually its depth of flavor is the result of fresh herbs, shallots, tomatoes, seasonings, olive oil, and a touch of dairy being cooked and added in stages. Lon ...more
Are ants invading your living space? Start peeling some raw onions. Or add a sprinkle of black pepper to your floor and countertops. Or make yourself some coffee and sprinkle the leftover coffee grounds in areas where ants have been spotted. Somewhere in your pantry shelf or r ...more
Rooting is usually the first thing on the to-do list whenever one of us softModders gets a new Android device. Unfortunately our efforts are sometimes hindered by certain obstacles; a common one is a locked bootloader. What Is a Bootloader? A bootloader is the lowest level s ...more
For the normal woodworker at home, the table saw, router and lathe are the prime tools used for making fine furniture, but when you hit the outdoors, the backwoodsman's tool of trade is the chainsaw. Mastering furniture-making with a chainsaw is the key to being a great woodwo ...more
You may already know that you can build a functional circuit on a sheet of paper with the graphite from a pencil, but you'd probably never think of using it to fix an electronic device. This same principle can be used to bring back a bricked phone, but can also repair a damage ...more
In this video you will learn how to download a torrent PC game, mount and the burn it. For this you will need a torrent program (to download torrents), daemon tools (to mount the images) and powerISO (to burn it). To get a torrent go on site mentioned in the video or on other ...more
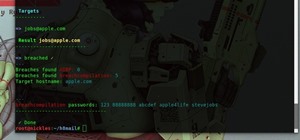
Welcome back, my greenhorn hackers! In recent weeks, the Heartbleed vulnerability of OpenSSL has been dominating the information security headlines. This vulnerability enables an attacker to extract data from the server's memory that may contain authentication credentials, co ...more
Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID ...more
When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch. In the world of Android devices, this doesn't ...more
Google's launchers are some of the most polished home screen apps out there, but they lack the ability to customize. With the old Google Now Launcher, we had Xposed GEL Settings to add options for tweaking the layout, but that project was abandoned when the Pixel Launcher came ...more
The OnePlus One definitely fits the phrase "more bang for your buck," and despite the absence of something like the HTC One M8's Duo Cam or the LG G3's Laser Auto Focus, it still takes a great photo. For normal, everyday pictures, the 13-megapixel camera sensor is great, even ...more
Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client. Although the most valuable information to the hacker ...more
Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with s ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
By eliminating the need for hard keys on phones, manufacturers are able to use that extra space for a larger display, which is clearly evident on the bezel-minimal LG G3. In order to replace the physical home, back, and app switcher keys, we now have stylish soft keys. While ...more
Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial ...more
As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent. ...more
If you recently received your new Galaxy S9 or S9+, you're probably excited to try out all of the features the flagship offers. While many of the features are self-explanatory and easy to access, there are a handful of very useful items that Samsung has buried in the settings ...more
Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The trig ...more
In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied togethe ...more
During initial reviews of the Nexus 6, the "double tap to wake" feature was something originally slated to be present on the device, since Motorola built it and it's been a key feature of the Moto X. However, the feature was scrapped for Ambient Display, which wakes up the scr ...more
In this tutorial, Peter John teaches us how to palm read: Crosses & islands on the main lines. Lines in the hand show how a person makes a change. When there is an island on the hand, this means the person needs to slow down and be careful. This could also mean their work is g ...more
With so many keyboard options available for Android, there's no reason to limit ourselves to the default one, or to just the ones available in the Amazon Appstore. While the Appstore does provide alternatives, such as SwiftKey, it doesn't come close to the selection available ...more
Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of thi ...more
Friendship has always been a staple of Animal Crossing games, and Animal Crossing: Pocket Camp makes no exceptions. Check out this guide if you're interested in how to maximize time with your furry friends. While building friendships has always been at the core of Animal Cros ...more
You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making i ...more
HTC's recent release of a new flagship phone brought tons of fanfare along with it. Dubbed The All New HTC One, the M8 edition of the popular One series phone also marked an update to the HTC Sense UI. Manufacturer skins like Sense can be a bit of a polarizing subject, especia ...more
Back in 2009, largely due to the sheer number of users demanding it, Spotify added an amazing little feature — the ability to disable volume normalization. While the feature is nothing more than a toggle on the visual front, the audible difference is far superior and moons apa ...more
Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset. It would be ha ...more
Everything you need to know about the FarmVille Orchards and how to Master Trees in FarmVille! **Please scroll down and check out my awesome Tree Mastery Chart** Place the orchard! It will take up 4x5 units on your farm. Build it for 10 boards, nails and bricks. Then fill i ...more
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you. Rooting allows you to remove barriers and open Android to a level of unprecedented contro ...more
If you're anything like me, you probably think it's borderline sacrilege to even think about a sandwich or a burger that doesn't have a layer of smooth mayonnaise. But I don't just keep a jar of it in my fridge for lunch—it's also there for practical purposes. I learned this ...more
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look ...more
To really customize your Samsung Galaxy S3, you'll need to be rooted, because most of the coolest mods and hacks require root access. If you haven't rooted yet, you're just barely touching the surface of what your GS3 can do for you. However, if you've never rooted before, it ...more
The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen bur ...more
Making a good crêpe takes practice and commitment. The batter is rich—most recipes incorporate melted butter, whole milk, and several eggs—and the cooking of the crêpe requires good technique. You have to learn to deposit and swirl just the right amount of batter to get the th ...more
You've done it, I've done it, almost everyone who owns a car has done it: they've gone an locked themselves out. Well, this good how-to shows how to get back into your older model car with nothing more than a coat hanger. It will requre some trial and error to get it done, but ...more
If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is wh ...more
Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And t ...more
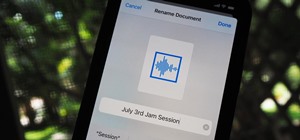
There's a good chance you've never used the Dictation function on your iPhone's keyboard, or even knew that it existed for that matter. That small microphone icon in between the emoji key and the space bar is great if you use dictation, but otherwise, it just gets in the way w ...more
Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack. That's because the database—alm ...more
Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC. After rooting, you can enjoy many of tomorrow's features to ...more