Not all Kickstarters are created equal. Some take forever to get their products to supporters, and when the product does arrive (usually much later than promised) it's often very rough around the edges. I'm here today to report that the exact opposite is the case with the Loo ...more
Every now and then, an iOS secret surfaces that makes me wonder, "How am I just learning about this?" I remember the first time I found out how to delete numbers in the Calculator app, and when I discovered you could bulk-move apps around the Home screen. Now, there's another ...more
Ever since China's Nreal unveiled its Light smartglasses at CES two years ago, an army of look-alikes have emerged from the Asian nation. We can also count Rokid among the companies blazing a different trail with Rokid Glass and Rokid Vision, each owning a distinctive look. ...more
Apple has four iPhone models for the remaining months of 2020, but the most impressive ones are the iPhone 12 Pro and iPhone 12 Pro Max. While the iPhone 12 and iPhone 12 mini are great smartphones, the "Pro" models offer more advanced features, especially for photographers an ...more
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which ...more
For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list. There are a lot of tools out there for creating fake access po ...more
From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run AD ...more
When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy f ...more
On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive- ...more
Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty ...more
If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been comp ...more
Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, ...more
By now, you've probably been inundated with enough Baby Yoda memes to last you a lifetime. But if you don't have the new Disney Plus streaming service on your TV, you're probably wondering where all this is coming from. Well, lucky for you, just in time for the holiday season, ...more
The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac co ...more
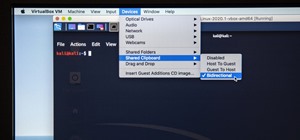
While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of ...more
The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-ch ...more
The Pixel 4 is one of the most talked-about phones of 2019, and it has many things going for it, especially in the world of rooting and modding. Just as with previous Pixel generations, unlocking the bootloader is the gateway to realizing your device's true potential. It can m ...more
Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might b ...more
It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner. We asked our tech-obsessed writers and editors to give us the lowdown on their must-have accessories when they splurge on a ...more
Lover it or hate it, Android 10 is a big improvement over Android 9 Pie. Based on previous versions, most flagships released in the last two years will get Android 10, but the question is when. So while you wait for those cool new gestures, how about I show you an app that giv ...more
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need roo ...more
Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking. But a new dynamic takes the notion of interaction with virtual content into a new real ...more
The OnePlus 7 Pro is truly the best phone that the company has ever created to date — it's even one of the hottest phones around regardless of OEM. It offers an awesome display with minimal bezels, a smooth 90-hertz refresh rate, a pop-up selfie camera, and the best triple cam ...more
With the new navigation gestures in Android 10, you reclaim a lot of screen real estate that used to be occupied by the back, home, and recent apps buttons. But there's still a small bar on the bottom edge of the screen, and in most apps, it still sits atop a black background. ...more
The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or ne ...more
EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit ...more
When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a wh ...more
When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general p ...more
Editing photos can be tedious, especially if you are using a similar theme for all of your photos. It takes time to select every tool, play with the bars, and find an adjustment that you're happy with. Luckily, there's a faster way. Adobe Lightroom for Android and iPhone allow ...more
While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission. This week, China-based Nreal made the potential mass adoption of its N ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
Picture this: You finally get that awesome angle, the perfect selfie. You can't wait to post it on your Instagram, except there's one problem — it looks a little flat and the colors just seem off. Maybe it's the lights? Or maybe your new smartphone camera isn't as good as you ...more
Imagine this: you have your finger poised to take the perfect picture — a once in a lifetime opportunity, like a solar eclipse — and you are suddenly caught off guard by a buzz, then "ding!" You look down at your phone to find your perfect pic ruined by distortion from the vib ...more
In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future. Traditional mobile apps on smartphones continued to maintain user attentio ...more
The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant b ...more
Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone ar ...more
No matter how good a display is, the idea of perfect color calibration is subjective — some prefer warmer more saturated colors, while others prefer the calmer cooler side of the color spectrum. It is almost impossible to create a single color calibration that everyone can agr ...more
In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls. In this tutorial, you'll learn how to make your augmented ...more
Your iPhone comes packed with a long list of excellent text tones to choose from. Bamboo anyone? Of course, for some of us, stock sounds from 2013 don't cut it anymore. We want customizability, something that's found more on Android than iOS. However, you can add your very own ...more
Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all o ...more
It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that yo ...more
Despite a very vocal distaste for Bixby, Samsung continues to push their voice assistant on customers. For many, the button is not only a waste, but placed perfectly for accidental presses. While it appears Samsung has no intention of giving up on Bixby, with the help of an ex ...more
The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true? On Wednesday morning, as Next Real ...more
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satis ...more
With Tasty dominating Facebook videos and online cooking flourishing, it can be cumbersome to keep track of all your recipes. Someone might send you something, and storing it in an app like Pocket is like jamming all your school papers in one folder — it just isn't practical. ...more
It's no secret that Android has a messaging problem. iPhone users can turn to iMessage as a one-stop shop for all their messaging needs — features like read receipts and the ability to text from a computer have been standard with Apple products for quite some time. Android has ...more
During E3, many major game developers announced plans to bring console and PC franchises to mobile. These titles are designed for more serious gamers with competition in mind. All of this points to a shift in mobile hardware priorities — soon, gamers will need gaming phones ju ...more
With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks. A real PDF is required for the attack to work. Files ov ...more
There are more ways to finding your missing iPhone than using Apple's own "Find My iPhone" tool in iCloud. If you just need help tracking down your iPhone in your home or at a friend's house, Find My iPhone isn't necessarily the most convenient thing to do when you've got thes ...more
I love my iPhone, but it would be a lie to say there aren't some Android features I wish would find their way to iOS. While iOS has plenty of its own advantages, Android has pulled ahead in many other areas. With iOS 12 coming later this year, we're hoping Apple takes a hint f ...more
Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer. This part is more involved, but the first ...more
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonl ...more
Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update t ...more
In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between ...more
Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecur ...more
Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL. Those who follow the game more closely realize that, despite their prom ...more
On the surface, iOS 10.2 might look the same as iOS 10.3, but there's one big difference between the two versions: iOS 10.2 can now be jailbroken! Jailbreaking your iPhone means gaining access to thousands of tweaks and mods which greatly enhance the iOS experience, so this is ...more
Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
What makes YouTube such a special platform is that anyone and everyone can upload their own content. Big players upload their videos to the same site that the little guy does. But what if you're a little guy who has never uploaded a video before? Or, what if you're a regular ...more