Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such f ...more
Unlike on Android, you can't easily hide your iPhone apps. Sure, you can nestle them away in folders labeled "junk," but they're supposed to be omni-present somewhere on your home screen. That is, until one day they're just ... gone. The fact that some of your apps disappeared ...more
For all that money spent on a new Watch, Apple could've given us more than just a charger and its case. I mean, the case is nice and all, but what realistic use is there for it? In all honesty, it'll probably find its way onto a shelf high above in the closet—but it doesn't ha ...more
Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, ...more
Even if you're new to Android phones, chances are you've heard of the power of Android's customization, and that applies to the Samsung Galaxy Note 20 series as well. Your brand new Galaxy Note 20 or Note 20 Ultra's operating system is capable of modification beyond what's ava ...more
The art of taking secret photos is one that requires keen awareness and skill. Not only do you need to ensure that your subject remains oblivious, but you also need to make sure that no one near you notices what you're attempting to do. It's great when you buddy is acting a fo ...more
All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Lea ...more
The Nexus 6 uses an Ambient Display notification system that was heavily inspired by the Active Display feature on the Moto X. Essentially, the device shows a black-and-white version of the lock screen whenever you receive a new notification or pick the phone up. This is all m ...more
Home screen widgets might not be a new concept in the Android world, but for iPhones, they're downright revolutionary. A new iOS 14 feature allows you to place small, medium, and large-sized widgets of your favorite apps on the home screen, to see important information without ...more
One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on ...more
Unbeknownst to you, hundreds of retailers, shopping malls, coffee shops, and airports track and log your movements. Using sensors installed by retail analytics companies, businesses sniff out your smartphone's MAC address, a unique fixed identifier to your device, whenever you ...more
We may all have a Nexus 7 tablet, but we don't all want to have the exact same look and feel, which is why we softMod for a more personalized vibe. There are hundreds of cool mods you can perform on your Nexus 7, whether stock or rooted, but one of my favorites in Android 4.4 ...more
With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working ...more
The "Hidden" album on your iPhone has always had one problem — it was never truly hidden. Since iOS 10, when the feature was introduced in the Photos app, any image or video that you conceal in the private folder could be seen by anyone with access to your unlocked device. Fin ...more
The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this ine ...more
Bees are the key to pollination and healthy vegetation, and wasps may help by assisting in pest control, but despite their benefits in the world, they're still a real pain in the ass if they're in your face. This would probably warrant an expression stronger than "pain in the ...more
A year after making a splash at the annual Consumer Electronics Show in Las Vegas with Amazon Alexa integration, smartglasses maker Vuzix is bringing a notable weather app to its Blade smartglasses for the 2019 edition of the conference. Vuzix has announced that its Blade dev ...more
The Nexus 6 came with a hidden kernel module that allowed for double-tap-to-wake functionality, essentially letting you turn your screen on just by tapping it. A simple root app allowed us to activate this feature, which meant we were always two quick taps away from waking our ...more
The guitar is a double-edged sword. I've played all my life, and though I love the act of guitar playing, there are quite a few people I could live with never hearing play again—ever. Paradoxically, it seems that the less dexterous and committed to practicing are the more lik ...more
While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups a ...more
The OnePlus 7 Pro is truly the best phone that the company has ever created to date — it's even one of the hottest phones around regardless of OEM. It offers an awesome display with minimal bezels, a smooth 90-hertz refresh rate, a pop-up selfie camera, and the best triple cam ...more
After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair. To address the apparent new interest in company's Amazon Alexa-equipped Blade smartglasses, the company has ...more
This week, saw two companies leaning on AR to prop up their financial futures. On one hand, Apple made quite a bit of AR-related news ahead of its quarterly earnings report next week. On the other hand, Vuzix launched a pre-order program for its Blade smartglasses and closed ...more
When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings. Why? Well, for once, we finally had a smartphone, or in this case, a pair of sma ...more
I think everyone with an iPhone should be making every purchase they can with Apple Pay. I also think everyone who uses Apple Pay should open the Wallet app ahead of time, instead of simply tapping their iPhone to the card reader. But there's a much faster way to open Wallet t ...more
The UK has officially exited the European Union, completing the long and tumultuous Brexit story and putting the storied nation once again on its own on the international stage. And while some are wondering what the future holds for the EU-less UK, the country is kicking off ...more
Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools li ...more
First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements Kali (or ...more
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we c ...more
If we're being honest, very few people go on Tinder to fall in love with someone's personality. Oftentimes, the only reason they'll look at your bio is to make sure there are no red flags. Knowing this, Tinder's latest redesign isn't that surprising, and it probably won't eve ...more
A lot of people hate chopping onions, and understandably so. Their shape and layers make them difficult to handle if you don't have much practice, and even if you know exactly what you're doing, it's a task that usually ends in tears. Like most other vegetables, there's a met ...more
The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilit ...more
Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a ...more
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they' ...more
There's something missing on your brand new Samsung Galaxy S4, and if you're a softModder like me, you know exactly what it is already. If you don't know, keep reading, because you should—anyone who wants a better Android experience should. The Developer Options The hidden " ...more
Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting ...more
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser. Steganography is the art of hiding secret messages comprised of text, code, au ...more
Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. ...more
ESP8266-based microcontrollers can be used to create exciting and legal Wi-Fi hacking games to test your or your friends' Wi-Fi hacking skills. When you first start learning how to hack Wi-Fi, it can be tempting to use your powers on Wi-Fi networks you don't have permission t ...more
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby devi ...more
While using end-to-end encryption may be enough security for most of your messages in Telegram, you can go a step beyond this by sending messages that disappear after an allotted amount of time. This prevents you from having to manually delete the message at a later time, so y ...more
Native screen recording, one of the hottest features that Apple included in iOS 11 and later, is easily started from the optional Control Center toggle on your iPhone. From there, you can stop recording from the same place or from the red status bar or bubble. It's a very conv ...more
Apple just pushed out the iOS 10.3 update to everyone on March 27, so if you haven't installed it yet, make sure to do so by going to Settings -> General -> Software Update. Trust us, you'll want to. iOS 10.3 is a fairly major update, and will succeed iOS 10.2.1 on your iPad, ...more
Apple has a new way to tidy up your favorite bookmarks in Safari, making them easier to access than ever before. This new feature saves space, allowing you to quickly see more of your favorites at the same time. While you can quickly access any of your iCloud-synced favorite ...more
In the past, Apple never really put much work into its Contacts app for iPhone, making the tool much less useful than its Mac and iCloud counterparts. But now the Contacts app for iOS is a force to be reckoned with. Packed with new features (some hidden), it's finally good eno ...more
This recipe almost exactly replicates Heston Blumenthal's famous English recipe. Even if you can't find a candied orange, this tutorial shows you how to make one yourself. You will need, apart from the candied orange, a grated carrot, a grated green apple, three eggs, mixed dr ...more
Apple took great strides to enhance Accessibility features on iOS 7 for low-vision users, adding button shapes, dark colors, bold keyboard text, and more. With iOS 8, Apple looks to continue their run at making life easier for the optically impaired. Zoom, the built-in magnif ...more
I often read ebooks on my iPhone while I walk, but being glued to my screen is a good way to get run over or cursed at. To save my physical and social hide, I use this trick to get my iPhone to read ebooks and articles out loud, turning my whole text library into de facto audi ...more
If you're someone who shares a lot of tweets outside of Twitter, you know the struggle. Twitter's share button, like YouTube's, is proprietary, which means you need to wade through Twitter's own sharing options to find your iPhone's regular Share sheet instead. However, there' ...more
Kylo Ren, conflicted villain of the new Star Wars trilogy, will surely be a major presence again this Halloween, with The Last Jedi fast approaching. His costume, all black and layered, complete with dark-side helmet and crossguard lightsaber, seems quite perfect for Oct. 31 — ...more
There's only a few week left until costumes and candy take over the streets, which means they'll be more and more seven-letter words in the Scrabble Bingo of the Days that relate to the Fall season, horror movies, and of course… Halloween. Below you'll find bingo words relevan ...more
Apple likes hiding things in its software, including secret apps, hidden iMessage effects, status bar customization, nameless icons, and red screen mode, but some of its best Easter eggs are right in front of you on the Home Screen. Some of Apple's app icons on iOS 17, iPadOS ...more
Vegetables are perhaps the most important part of our diets, but often times they're an absolute pain to prepare. Cleaning every fleck of dirt off of dozens of leafy greens takes ages, and eliminating the more fibrous parts of certain veggies can be extremely tedious. But whe ...more
One of the standout features of the OnePlus 7 Pro is the 90 Hz display. A higher refresh rate means smoother gameplay for all your favorite games, which is precisely what you'd want out of your gaming experience. However, not all games play nicely with these higher refresh rat ...more
There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space. The story is about a king that loved chess and the sage that he challenged. To motivate ...more
Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints. In all of these places, I've found a consistent annoyance—I wa ...more
Smartphone videos get better and better each year. Seven or eight years ago, who would have thought iPhone and Android phones could support 4K video recording. Some phones can even shoot slow-motion at 960 fps. But no matter the resolution or frame rate, a phone's rolling shut ...more
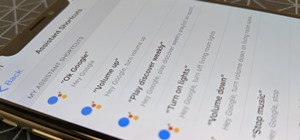
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quir ...more
One of the hardest, most intimidating parts of making your own Steampunk guns from scratch is the wooden stock of the gun. To be fair, it's probably the hardest part. It requires the most artistry, and is the easiest to mess up. So, I'm going to give you a guide to making you ...more
Introduction In this article you will find instructions to replace a broken LCD screen of a LG KF600 phone. To execute these steps a new replacement LCD should be bought beforehand. Stores that sell replacement KF600 LCD screen can be found on the Internet. These instructions ...more