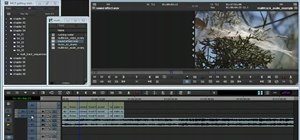
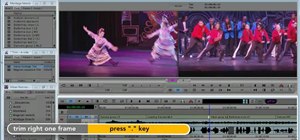
Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn. Generally, when we are trying to hack a target, we want to know as much as possible about the target through reconnais ...more
There are few sounds that actually make me cringe whenever I hear them: silverware scraping on a plate, nails scratching on a chalkboard, and piercing high-frequency tones. While the former two terrors require some physical hardware, sending out high-frequency sounds is as eas ...more
Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensi ...more
Have a load of games you want to play, but don't want to be seen in public playing on your old school Nintendo DS system? Play them on your Samsung Galaxy Note 2! Now, I've already covered how to play N64, GBA, and SNES games on your Galaxy Note 2, so it only makes sense to c ...more
For about a million Americans each year, a joint replacement brings relief from pain and restored mobility. But, 5–10% of those people have to endure another surgery within seven years, and most of those are due to an infection in their new joint. If doctors could treat infect ...more
As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists b ...more
Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, ...more
Heart disease is the leading cause of death of men and women in the US. Over half a million Americans die from it annually. Atherosclerosis — a build up of plaque in the arteries — is a common feature of heart disease and can be caused by smoking, fats and cholesterol in the b ...more
When I booted up my second Sega Forever title, I wasn't sure what to expect. Sonic 1 was fun, but the controls weren't great. Touch screen controls can be excellent when the game is designed for them, but retrofitting a game designed for a physical controller to be played on a ...more
Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe? There are o ...more
There could be a fresh outbreak of the Zika virus in the Americas as the weather heats up and the mosquito population blooms. Last year in February, the disease was declared a "public health emergency of international concern" by the World Health Organization, and the United ...more
The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward. A new study published in Nature Communications, by a group of researchers from the August Pi i Sunyer Biomedical Research Institute, Barcelona Insti ...more
Over 1.2 million people in the US are infected with human immunodeficiency virus (HIV)—and one out of eight of them don't know it. Even after decades of intense research into the virus, there's still no cure for it. One of the big problems is that the virus hides out in certai ...more
Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems ...more
Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like ...more
Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series ...more
Any beer aficionado who's been to Ireland will always talk about how the Guinness there "just tastes different." But save your eye rolls, skeptics: it turns out your favorite lagerhead actually has a valid point. Some people think there's a different formula for Irish vs. Ame ...more
Every year, some overly ambitious neighbor down the street amazes the crowds with his DIY illusion costume. While these costumes certainly require more work than pulling a mask over your head, they do have that wow factor that others lack. These costumes illicit lots of doubl ...more
Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving ...more
Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. ...more
Scary costumes are the only way to go for Halloween, but instead of shelling out upwards of 150 bucks this year for some store-bought outfit, save your cash for things like candy and create your own costume on the cheap. The Tale of Slender Man Remember the Slender Man? The ...more
Whoop, there it is. McDonald's makes its food even faster by partnering with UberEats to bring orders to your doorstep in over 1,000 locations around the country. So watch out Los Angeles, Chicago, Columbus, and Phoenix, because now you have the option to never get up from yo ...more
For those familiar with my old YouTube series, New in the Store, you will be excited to know that I am starting something very similar here on NextReality that's a bit more broad in scope. Have You Seen This? will take a look at HoloLens applications that are new in the Window ...more
I'll bet this scenario will sound familiar to you: you're in the middle of making a spectacular dessert that will knock the socks off of your guests, and you've almost finished gathering all of your ingredients to create your mise en place. The last ingredient listed is powder ...more
Is "Last Resort" Steampunk? Well, no. I mean, how could it be? For those not familiar with this television show, it's about the crew of a nuclear submarine, the USS Colorado, who go rogue after receiving false orders to launch nuclear missiles at Pakistan. They take refuge on ...more
As 2009 comes to a close, the Telegraph presents a compilation of this past year's wackiest inventions. As always, here at WonderHowTo, we are inspired and impressed by ingenuity. The contraptions below range from utter silliness (engagement ring bra) to downright amazing (see ...more
The App Store has been around for almost 14 years now, and during that time, we must have seen over a million games come and go and stay and expand. But only a tiny fraction of those games have become blockbuster sensations because of the mighty App Store's reach on iPhone and ...more
Staying inside during the coronavirus pandemic isn't easy for most of us. As important as it is to keep away from others, it can be challenging to keep to ourselves day after day. That's why mobile game developers are stepping in to help; many are making their games free for a ...more
While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on ...more
Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering att ...more
If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against ...more
An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus. Naturally occurring in animals and the soil, Bacillus anthracis is a rugged bacteria that has a protective outer shell, called a s ...more
Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence ...more
After California college student Luis Ortiz blacked out and was taken to the hospital in 2015, doctors were startled to discover the reason his brain was swelling—a one-centimeter long, wriggling tapeworm living within a ventricle in the middle of his brain. Spoiler alert: If ...more
Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ...more
In Pokémon GO, having an in-depth understanding of your Pokémon's stats and abilities is crucially important to becoming a better player. Not all Pokémon are created equal; as such, it's critical that you look at each of your Pokémon—even duplicates—with a keen eye. Every Pok ...more
In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Wh ...more
As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of ...more
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis. Osteoarthritis commonly occurs after the age of 45. Men who are under the age ...more
The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve? If you missed the opportunity to snag a kiss using the awesome mistletoe trick, then this is your last c ...more
Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills. Linux beginners are often faced with the issue of how to find fi ...more
Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive. End ...more
I've had a handlebar mustache for about five years now, and I've learned a lot over those years about how to grow and care for it. I will now share all of that information with you! Hopefully this will encourage you to grow one for Movember! The first thing I want to address r ...more
A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and ...more
If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed. Spooky Action at a Distance If you need to prove you've got remote ...more
If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them ov ...more
Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we ...more
For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and se ...more
We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of compani ...more
Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while. During my time here, I've seen our community cultivate into the brilliant one ...more
Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from food ...more
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information i ...more
While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free ...more
The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done. As we reported back in September, the c ...more
The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for ...more
Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to in ...more
Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a fe ...more
Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a " ...more
In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hea ...more
The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, ...more