If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization. That means you've probably rooted and unlocked the bootloader on your HTC One to upgrade to the Google Play Edition ROM or CyanogenMo ...more
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance. After browsing it is ...more
While there's still no set date, Jelly Bean 4.3 is rumored to be released on the Samsung Galaxy S4 and other TouchWiz devices within the next couple of weeks (or months), presumably sometime after the upcoming Samsung Unpacked event. One of the improvements that Android 4.3 b ...more
"What's the point of having a Nexus 7 for drawing if all of the drawing apps suck?" That's what my girlfriend said after buying her new Nexus 7 tablet. She draws a lot and was hoping to hone her doodling skills on it, but she's right—most of the drawing apps available on Googl ...more
Snapchat users upload a whopping 150 million pictures a day—which are deleted as just quick as they're sent. However, none of these images are coming from Android tablet users. If you try downloading Snapchat from Google Play on your Nexus 7 or other Android tablet, you'll get ...more
Snapchat's self-destructing nature is the perfect way to send funny and potentially embarrassing photos and videos (something Anthony Weiner wishes he knew about). That's why there are currently 150 million Snapchats sent each day. While it may be used for fun, many fail to re ...more
The first thing I do when I get a new phone is ditch the USB cable. At least, when it comes to data transfer. My brand new HTC One came with a USB cord that feels sturdy, but like any other cable, it will eventually fall apart from overuse. It will probably still charge just f ...more
The new Samsung Galaxy S4 has something no other phone has ever had before—weather sensors. Older devices like the Galaxy Nexus, S3, Note, and Note 2 do have a atmospheric pressure sensor, aka a barometer. However, they do not have a thermometer or hygrometer like the GS4 does ...more
Here's a quick and easy video tutorial on how to root any Qualcomm-based U.S. or Canadian Galaxy S4 Android smartphone. Windows, Mac, and Linux Tutorial included. Video: . Video: . Video: . Step 1. Go to Settings->More->About device then hit “Build Number” about 5-10 times u ...more
Rooting, bootloaders, custom ROMs, CyanogenMod, ClockworkMod... it's all pretty confusing, isn't it? You're not the only one having trouble with this. Many users in the Nexus 7 SoftModder forum have been scratching their heads at these many terms. First, let's cover the terms ...more
Advancements to Android's open source OS come in the form of ROMs and mods, available all over the web for anyone to find. Installing any of these modifications tends to wipe your phone clean, causing you to lose all of the precious data on your device. Remember when you used ...more
Google's newest Android system update should be arriving on Tuesday, November 13th, with the release of the Google Nexus 4 smartphone, and Nexus 7 and 10 tablets. All will come preloaded with the new Android 4.2 Jelly Bean OS, but what about the rest of you (especially those w ...more
Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent ve ...more
With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Mi ...more
UPDATE: A patch to fix the exploit has been released. Download it here. A new vulnerability in Java 7 has been added to the BlackHole exploit kit and Metasploit that allows malicious software to be installed on Windows, Mac OS X, and Linux computers. So far, it has only been ...more
If you've got more than one computer, it can be a huge pain to switch form one to the other. Between files, settings and apps, it can take a while to transfer everything—and if you're running different operating systems, it's even worse. Image by Onion A new feature on Window ...more
If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you' ...more
Beta software can be exciting because you get to experience cool new features before most other people. But it can have unwanted consequences such as bugs, UI glitches, and horrible battery life that'll make you wish you never installed it. If that sounds like you with iOS 16 ...more
The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar ...more
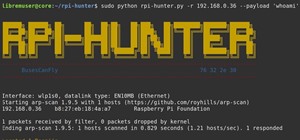
With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network. After exploiting a system, penetration tester's and hackers will ofte ...more
Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history v ...more
Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools a ...more
Recording phone calls has always been tricky due to legal, ethical, and technical considerations. With iOS 18.1, Apple brings your iPhone a native call recording feature that simplifies this process while addressing privacy concerns. There are a few things to know about call ...more
When you need a file on your Mac as soon as possible, you usually have to get your MacBook or hop on your iMac, Mac mini, Mac Pro, or Mac Studio. But that's too much work if you're in bed, lying on the couch, or outside in the fresh air. Why even bother when you can access tha ...more
In the past, Apple never really put much work into its Contacts app for iPhone, making the tool much less useful than its Mac and iCloud counterparts. But now the Contacts app for iOS is a force to be reckoned with. Packed with new features (some hidden), it's finally good eno ...more
If you haven't been using Spotlight Search on your iPhone, we've got ten reasons for you to start. Apple's made some significant improvements to the search interface available on the Home Screen and Lock Screen, and it's more useful than ever. The new features and updates for ...more
If you use the Apple TV Remote found in your iPhone's Control Center, there's a hidden surprise you'll like on iOS 16 and later — one that lets you use the remote without ever having to open Control Center. You can use the Apple TV Remote to control media playback on your App ...more
Apple's Contacts app just got its biggest update ever. Since the first iPhone in 2008, there have only been minor upgrades here and there to how you manage and interact with contacts. That changes with iOS 16. The last major feature Contacts received was emergency contacts th ...more
Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release. ...more
One of the more exciting augmented reality announcements Apple made during its WWDC keynote on Monday came in the form of Object Capture, a new 3D scanning feature coming to macOS Monterey. That cry you just heard in the distance came from the chorus of companies who have pub ...more
One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again. The combatants? Unreal Engine maker Epic Games versus the Chinese startup known as Nreal (aka Shenzhen Tairuo, formerly known as Hangzhou Tair ...more
As the U.S. inches closer to herd immunity and reopening after the pandemic, it may become necessary to keep your COVID-19 vaccination cards on you at all times to gain access to places and events that are prone to spreading the coronavirus. You probably won't want to lose you ...more
If Pandora is your primary music app on your iPhone, you know it can be frustrating to use with Siri. The digital assistant always wants to use Apple Music instead, so you need to specify that you want to play through Pandora with almost every request. That's now a thing of th ...more
One of iCloud Photo's biggest perks is its ability to store large video files taken with your iPhone, so you can fill up your iPhone's storage with other items. That said, when you play back those videos, you may not be watching the footage in its original quality. Instead, th ...more
A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangib ...more
Whether you're using your iPhone to add graphics to a document, edit a photo, or sketch an idea, color plays a vital role in making your work look great. Apple's iOS 14 update introduces a system-wide color picker that lets you pick the exact color you want, save it to your fa ...more
A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later. We're going to explore how it works by creating a single line that downloads and runs potentially infinite ...more
It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for ...more
There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture hands ...more
The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-ch ...more
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones ...more
Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries. And while those films hav ...more
The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right n ...more
Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks. Sparta, authored ...more
Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file. The vulnerability was discovered by Filippo Cav ...more
A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hash ...more
For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to ...more
The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. T ...more
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, b ...more
It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept. In bot ...more
MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the com ...more
Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP wit ...more
Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPa ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer. This part is more involved, but the first ...more
To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the f ...more
PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we ...more
In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between ...more
In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal eff ...more