Torus knots are beautiful knots formed by wrapping a line around a torus and tying the ends together to form a loop. The resulting knot has a star-like appearance when viewed from above. The 36 examples with the least number of crossings can be seen at the Knot Atlas's page on ...more
Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and ...more
Excitement is building for the official Android Oreo release on the Galaxy Note 8. We detailed a leaked Oreo build for the Galaxy S8 and made a short tutorial on how to install it on your device. Now, there's a newer Oreo build available for the Galaxy Note 8 as well. Both of ...more
Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information. B ...more
A few days ago, CloudOn released their free mobile app that brought Microsoft Office directly to your Apple iPad. The cloud-based service effectively runs Office on their end, allowing you to use apps like Word and PowerPoint to edit your documents, which you would house in Dr ...more
Shortly after we detailed several indicators that the Galaxy S8 Oreo Beta Program would begin rolling out in the month of November, we now have a full changelog for the update. Many users on Reddit already found references to the beta in the Samsung+ and Samsung Members app. ...more
If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?" Many of the top names in the industry from the 2018 edition remain the same, but their positions have shuffled. The p ...more
Earlier last month, I wrote on how to subscribe to Google+ users using PlusFeed. I used it, and then I realized that I wasn't getting my own feed anymore. I discovered that the free service had been disabled due to cost issues, as detailed by the creator +Russell Beattie. The ...more
I got hooked on origami sometime after Math Craft admin Cory Poole posted instructions for creating modular origami, but I had to take a break to finish a quilt I've been working on for a while now. It's my first quilt, and very simple in its construction (straight up squares, ...more
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly ...more
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser. Steganography is the art of hiding secret messages comprised of text, code, au ...more
Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one ma ...more
Confirmation numbers, grocery lists, addresses, and phone numbers are all things we need to quickly jot down on our phones, but the thing is, they're never extremely easy to access later. You have to figure out which app you wrote them in, meaning lots of needless searching an ...more
Need to find the greatest common factor for a set of numbers? Easy as cake. Learn how to find GCFs using the upside-down birthday cake method with this free video lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematic ...more
Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too. Yes, you read that right: avocados are fabulous in desserts, where they can add creamy richness, ...more
Apple's Mail app has always been a stylish yet simple way to check and send emails. Third-party apps up the ante with powerful tools and features to help keep junk and spam mail out of your eyesight. But with iOS 13, you don't need them since Apple gave the Mail app some much- ...more
One of the first orders of business after purchasing a new smartphone is to load up your shiny new toy with phone numbers, email addresses, and general contact information for all the important people in your life. Don't Miss: Android Basics: Get Started with Your New Smartph ...more
How do you show that you love your job? You get "sleeved", like photographer Dabe Alan who has lined his arms with tattoos of all his favorite things in life, with the help of Toledo-based tattoo artist Tony Touch. Every time Dabe visits Toledo, he gets another photography-rel ...more
This video shows us how to draw a spiral staircase in a very simple way. Firstly a horizontal line is drawn and upon that a rectangle is drawn. Then four lines are drawn from the four corners of the rectangle and all this four lines are meeting at the same point on the horizon ...more
If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters. When friends or family come over, it can be really hard to relay the password correctly. Repeating it out loud is usually hit or ...more
Check out this informative video tutorial from Apple on how to create and edit shapes in Keynote '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages. Numb ...more
Toss aside that Sudoku. Take a stab at the new craze to hit the Times: KenKen. New York Times puzzle editor Will Shortz introduces KenKen and gives a brief play-by-play demonstration of this new puzzle craze. In this video, Will Shortz speaks about how he found out about and ...more
Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees. Luckily, tho ...more
Using variables allows your Lego Mindstorms NXT robot to store numbers or text based on input. Learn how to program variables using the NXT programming environment. Program variables in the Lego Mindstorms NXT system. Click through to watch this video on ortop.org
D.I.Y.: Start Your Own Cassette Label! By adam_schragin on Aug 4, 2008 at 10:56am in DIY Let’s say you’ve got the itch to start your own label. You’ve got the typeface all picked out, the clever name ready, and an idea of what sort of music you’d like to showcase. What you d ...more
Check out this informative video tutorial from Apple on how to add citations and equations in Pages '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages. N ...more
Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in th ...more
This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartblee ...more
Here you will find some excellent charts to help you master the Crafting Goods and get signs you can place on your farm! For more in depth information and ideas please see the FarmVille Crafting Building Mastery and Recipe Guide. Tips Use Master Chart when buying your friend ...more
You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ign ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
Check out this informative video tutorial from Apple on how to track changes and add comments in Pages '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages ...more
When it comes to blocking unwanted calls, your Android device comes stocked with a native blocking feature that allows you to reject certain phone numbers. That being said, the native blocking feature on the Samsung Galaxy Note 3 isn't the prettiest or the smartest, with its n ...more
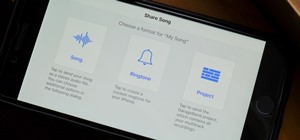
One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download mus ...more
Primarily caused by the bacteria Borrelia burgdorferi, Lyme disease is the most common tickborne disease in the US. By all predictions, 2017 is expected to be a banner tick year in several regions. If you have children, it is important to know what to expect. Ticks can bite a ...more
In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the ...more
Are you here yet? When will you arrive? How long until you get here? How far are you? Hurry up! When you're meeting up with someone or a group of people, you may get flooded with messages like that. Instead of trying to answer them mid-trip, you can send them your status from ...more
How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker. Crackers are malicious computer users who specialize in breaking into things. Whether it be passwords, login ...more
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's Excel ...more
With the advent of text messaging, our communication habits have changed drastically. Social niceties are still there, but we budget our words a little more since they have to be typed out rather than spoken. After all, SMS stands for "Short Message Service," so this is the na ...more
Finding love is tough. Movies like The Notebook and Twilight have ruined the expectations of love and relationships for us guys. Some women's ideal love situation is being kissed by a glittery sparkling vampire. "I know we only met a few seconds ago, but I'm deeply in love wi ...more
You have a lot of choices when it comes to your next smartphone. iPhone, Galaxy, Pixel, G6, V20, and many more all vie for your wallet. Each of these phones are great for different purposes, but what if your main interest is mobile gaming? Which phone will give you the longest ...more
Being able to spell a seven-letter word on the board is one of the most enjoyable things about playing Scrabble. It's even better when those seven letters are all from your rack, giving you a bingo—those 50 bonus points in addition to your regular score. But just because you ...more
One lump or two? That was the age-old question with sugar cubes, which used to be a staple of any tea salon or dignified household this side of Downton Abbey. These days sugar isn't really used in cubes much except in bars and restaurants, and that's a shame. Cubes are a lot l ...more
Set the packaged roast on the kitchen counter. Let the roast warm to room temperature for an hour or more. This helps it to cook evenly. Unwrap and coat the roast with olive or vegetable oil. Rub with the spices of your choice. Crushed garlic is often used with beef. Some ch ...more
Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused ...more
With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these al ...more
Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in any ...more
This is my fourth (and final) installment on SCRABBLE adverts. I'm sure there's a lot I haven't found, but that's for another day. But this post features all of the remaining SCRABBLE advertisements (prints and posters) that haven't already been listed in my previous posts: O ...more
As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface. In recent years, the vernacular for referrin ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a U ...more
If you've recently jailbroken your iPhone 5, there's a likely chance that you're overwhelmed by the huge numbers of themes, add-ons and tweaks littered throughout the Cydia directory. The tweaks, of which there are over 1,000 in Cydia, resolve many issues and inconveniences t ...more
Need to be undercover? Well, make yourself impossible to photograph. Get some infrared LEDs. They're undetectable to the human eye, but that's not the case with cameras. Wire them to the brim of your hat and you've got instant invisibility to any camera -- paparazzi, Big Brot ...more
Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short. Ma ...more
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in par ...more
Introduction So, today and yesterday I was playing with TNT (as we all do at one point or another) and was curious about a few things. From this curiosity, I went onto discover some of the science behind some things you may or may not have known. While I was conducting this ...more
Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPh ...more
This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188 ...more
Download the Software Go to the Antiprism downloads page. Download and install Antiprism 0.20. Run the Programs You need a method of running programs on the command line. In Windows, that could be a DOS box, on other systems a terminal emulator (e.g. xterm). Start this up. ...more
Mobile gaming still isn't on par with video game consoles or PCs, but we've come a long way from Snake. Modern games running on the latest smartphones boast downright impressive graphics—even more so when you consider how compact the system has to be in order to fit in people' ...more