Cooking for the holidays invariably means preparing a lot of food for a lot of people. This includes vegetables like carrots, onions, and squashes. Luckily the Tesco Food Club is here to help. They've got Aiden Byrne showing us the shortcut techniques that restaurants take. Yo ...more
In a recent survey of more than 5000 UK jobseekers by TotalJobs.com, it was found that 60% spend less than two hours working on each application following a job search, all inclusive of the time it takes to write a CV and covering letter, and to prepare for an interview. What ...more
In this article I’m going to talk about specific issues about optimizing your website, making it more clear to Google and other search engines exactly what your website is about. As I've discussed in previous articles this is very important for people when they are searching. ...more
Mike 'The Greek' drops by the Film Lab to deliver his own TED talk. The subject: How to make an Best Picture Oscar-winning film (based on numbers and statistics, which he loves maybe even more than money)
have a blind and deaf person go to a casino and sit down to play table games, have their friend start to help them but then start to cheat them out wth their winnings and see if anyone would catch onto the friend... tell the blind/deaf person the wrong numbers or cards that ca ...more
In this article I am going to take a look at the Google keyword tool, which is one of many keyword tool programs that you can use to find your keywords. What Google Keyword Tool does is pick up different keyword phrases that people commonly search for. It will do it on a glob ...more
This is a game for however many people would like to participate. The game is simple. Everyone plays a hand of poker, whoever has the lowest hand has to make a concoction. The person who loses has to role two dice. Each die and the six numbers on it corresponds to a different ...more
Conservative challenger Rick Santorum announced Tuesday that he is suspending his Republican presidential campaign after a weekend of "prayer and thought," effectively ceding the GOP nomination to front-runner Mitt Romney. Santorum made his announcement after the weekend hosp ...more
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on: Plans for Syria? CNN reports this afternoon th ...more
Voters look to candidates for long-term plan to fix economy - CNN.com. Some political experts say month-to-month jobs numbers don't mean as much to voters as which candidate offers a better economic outlook.
An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere! If you have a PC with a wireless network card, then you must have seen many networks around you. Sadly, most of these networks are sec ...more
Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my b ...more
Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the se ...more
A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vul ...more
Have an old bike combination lock that you can't remember the code for? If it's a simply four-digit cable lock, you can easily figure out the combination with a quick peck-and-go method. Best of all, this technique doesn't require any tools or special know-how, and let's you r ...more
One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend w ...more
School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block ac ...more
If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible. A few months ago, Dallas covered six ways to speed ...more
Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on h ...more
"What is dead may never die." That's easily one of the best lines (and episode title) from HBO's Game of Thrones series. While the saying may ring true for the Ironborn, it's not quite as catchy when it comes to batteries. Lithium-ion batteries power tons of consumer electron ...more
Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) feature ...more
Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, ...more
There's nothing worse than losing your phone—except losing your phone when the ringer is silent. If you're alone, it can be excruciatingly hard to find your lost device even if the ringer is on, considering most of us don't have landlines anymore. So, the next time you find yo ...more
Apple's Wallet app lets you store boarding passes, concert tickets, gym memberships, vaccination cards, movie stubs, rewards cards, insurance info, student IDs, and more in one place on your iPhone, and you just double-click the Home or Side button to access them. Unfortunatel ...more
The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history! Today, there ...more
The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, ...more
There's something missing on your brand new Samsung Galaxy S4, and if you're a softModder like me, you know exactly what it is already. If you don't know, keep reading, because you should—anyone who wants a better Android experience should. The Developer Options The hidden " ...more
INTRODUCTION In this world of Internet era, almost everyone wants to create theirs own web presence by either hosting their own blog, articles, photos, videos, reviews, etc etc . But some people choose their own way and decide to have something bigger! What is it? Its a websi ...more
There's a lot of conflicting information out there when it comes to the best habits for charging a smartphone's battery, so let's clear some of that up right off the bat. Lithium ion batteries (the type used in most modern electronics) start to lose their ability to hold a cha ...more
Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network. There are services out ...more
With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can ...more
Curve stitching is a form of string art where smooth curves are created through the use of straight lines. It is taught in many Junior High and High School art classes. I discovered it when my math students started showing me the geometric art they had created. The process of ...more
To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purch ...more
Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the ...more
Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic. The first a ...more
As iOS 10 makes its worldwide debut, many users are noticing that the promised iMessage effects feature in Messages is not working properly. Instead of seeing the actual effects, messages will come through like normal, but with text describing the effect they were sent with. O ...more
Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long ...more
hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack. ...more
Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords in ...more
Parental involvement is a crucial ingredient in the success of many children. Teachers know the saying all too well that it takes more than a village to raise a child, for one - it takes parental involvement. Thus, it is important for teachers to reach out to parents in that f ...more
In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging ...more
Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software b ...more
The new Samsung Galaxy Tab isn't a cell phone, but that doesn't stop you from making phone calls! With this Android tablet, it's a breeze to make phone calls. Just hit the PHONE icon on the homescreen and dial your number. Press CALL and wait for the connection. You can MUTE t ...more
Learn to access a number of Google Easter eggs with this simple Google hacker's how-to. Best of all, each of these Easter eggs can be found directly from Google search through use of Google's own "I'm Feeling Lucky" tool. The full list of Easter eggs explored in this video is ...more
This might be an old hack for Happy Aquarium, but for some of you it may still work. Most of you will not be able to do this, but it's always worth a shot, right? It's a cheat from 9/29/09 (wow!—retro hack) for which you need Cheat Engine 5.4. Newer versions of Cheat Engine sh ...more
In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's s ...more
While most are still fighting through a somewhat ridiculous invite system, OnePlus is starting to ship out a decent number of their One flagship devices to those who were able to obtain one. We all know that the price is the phone's biggest selling point, but there's still mu ...more
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery tar ...more
If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning e ...more
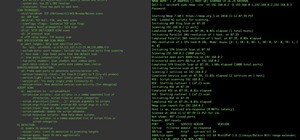
After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems ...more
Call any number you like and have any number show up on that person's caller ID. You can call from any phone in the World! Great for calling someone who does not want to answer the phone, checking up on your boyfriend or girlfriend, or just having fun with practical jokes. Lea ...more
One of the best features on the Galaxy S9 is the ability to quickly apply new themes from the Samsung theme store. A number of the available themes are available at no cost. If you pick the right dark theme, you might even be able to save some battery life over the course of y ...more
SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing ...more
Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of ...more
Want to switch your Blackberry Curve's service? Here might be your chance. In this tutorial, learn how to unlock (or jailbreak) your Blackberry Curve in just a few steps, listed below (from Killer Number X): 1) Go to menu 2) Go to options 3) Go to advanced options 4) Sim card ...more
Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording cap ...more
If you're a user of digital editing software Audacity, you already know you can do a ton of cool things. One of the cooler things you can do is changing a guy's voice to sound like a woman's. This is done with pitch control, or autotune, and will like you modify the voice by a ...more
There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you t ...more
How many of you have or know people who have a smartphone? There's a lot of you, right? Well, depending on how most of you use those smartphones, there could be all kind of sensitive information stored on it, and that doesn't just mean sensitive personal information, but it co ...more
Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you ...more