The man was requested to solve a short, basic chemistry exercise. He starts by explaining the meaning of the terms involved in the problem: molecular mass, empirical formula and molecular formula. He also explains the way the are connected, for a better understanding of the wa ...more
If you are fond of going live or watching live videos on Facebook, then you've probably experienced a number of viewers commenting. Sometimes these comments are good. Sometimes ... well, sometimes we could all go without them. If you want to stop a specific viewer from commen ...more
I don't know about you, but I love options. Personally, I think Android's notification system is easy to use — providing access to new notification with a swipe down from the top of the screen. But, as Android users, we like the ability to do things differently whenever we see ...more
Richard Sweeney is an incredible artist whose body of work consists mainly of sculptures made from paper. His art is often related to origami, and much of his work is related to geometrical forms. I personally really love his modular forms in paper. Many of them are based off ...more
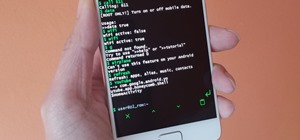
Unlocking "Developer options" on an Android device is useful for many things. You can limit or stop transition animations for a snappier device, enable USB debugging to run fastboot commands, and more. But of course, the first step to making these tweaks is to unlock the hidde ...more
One is the loneliest number there is. Well, unless you clone yourself! This sweet video will show you how to do just that with Apple's iMovie. You'll need iMovie 11, or iMovie 09. This technique is also possible by using other video editing software tools as long as they are c ...more
Beat the sixteenth level of Angry Birds Seasons with three stars! On December 1st, Rovio released their version of an advent calendar—Angry Birds Seasons (aka "Angry Birds Christmas"). Each day leading up to the Christmas holiday, a new level will become available to Angry Bir ...more
The best thing since the creation of bread may just be... sliced bread. Soft bread slices have the perfect absorbent texture for picking up tiny pieces of broken glass, gently cleaning dust off your precious oil paintings, and even safely removing splinters from your finger wh ...more
Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your ...more
Learn how to thrown any number you want by accurately placing the set dice in your hand and rolling with precision. This is a great gambling cheat or trick to pull on an unsuspecting friend. DICES CHEATING
If you're struggling a bit with algebra, check out this video to learn how to isolate a variable. Isolating a variable is a matter of separating and simplifying. Step 1: Bring like terms together Bring like terms together. All equations have two sides. You want to perform t ...more
Now that there's a working jailbreak for every iOS 6.1 device, there are more and more people jailbreaking their iPhones (including me) for better customization. But for those of you who have no desire to jailbreak, you can still do some pretty cool tweaks. One such non-jailb ...more
So how does a card counter keep track of the cards in blackjack? While there are many different systems and variations, counting cards is usually as simple as adding and subtracting the number 1. Subtract one when a high card is dealt and add one when a low card is dealt. The ...more
In this installment from the Unorthodox Hacking series of computer security tutorials, you'll learn a number of methods for hacking Windows shares as well as means of mitigating those hacks. For detailed instructions on Windows shares, and what you can do with them, watch this ...more
In this how-to video, you will learn how to burn game ISO's for the Xbox 360. It is important that it is only legal to back up the games that you already own. You will need the Image Burn program. Open it and click Write Image File to Disk. Next, click browse for file and look ...more
Move over Rubik's Cube, there's a new puzzle in town. The Petaminx. The beautifully designed and custom built Petaminx has almost 1,000 moving parts. Peta- actually means 1,000,000,000,000,000, although that number could refer to the endless number of solutions. Based on And ...more
Sometimes your pattern will instruct you to CAST ON AT THE END OF A ROW. CASTING ON AT THE END OF A ROW is quite easy. Here's how to do it: When you come to the end of the row, turn the work as to purl. Cast on, in the usual way, the number of stitches needed. Purl all the ...more
The discriminate of any equation in any degree plays an important role in determining the roots of that equation. In case of a quadratic equation with a positive discriminate, the roots are real while a 0 discriminate indicates a single real root. A negative discriminant indi ...more
This video is a Microsoft Word 2007 tutorial on working with pictures. To insert a picture in your document, click on Insert and select Picture, then find the picture, select and insert it. To resize the picture without distorting it, click and hold on the corner circles. You ...more
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 9th installment in ...more
If you ever find yourself with a ring that won't come off your swollen fingers, grab some Windex, lubricate the area around your ring below your knuckle, and slowly wiggle your ring around until it slides past your knuckle. No Windex in your home? You can try a number of othe ...more
Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time! Today, Minecraft 1.4.2 was released, and it's a doozy. Versions 1.4 and 1.4.1 were actually skipped entirely, as lots of bug-fixes were patched between th ...more
I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started... Your router is blocking outside traffic from coming inside the network for security reasons (Kind of, like, a firewall level), ...more
Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, a ...more
In this how to video, you will learn how to check your voice mail in Microsoft Office Outlook. Your exchange administrator must enable unified messaging for these messages to appear. First, open the program to set up your voice mail options. Go to options and click the voice m ...more
From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps. With this installment from Internet pedagogical sup ...more
Your S10's notification panel can quickly fill up with alerts about incoming messages, emails, weather reports ... the list goes on and on. If that weren't enough, those notifications are accompanied by badges that pop up as tiny numbered circles overlaid on icons within your ...more
If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against ...more
In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top po ...more
If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while i ...more
Watch this instructional science video to learn how to create hydrogen from water, salt and electricity, for only a few dollars. This is an experiment that produces explosive gases, involves electricity and water and a number of risks so please be careful. Not an experiment to ...more
According to a new study, the majority of smartphone users check their devices 150 times a day. While that number may seem incredibly high at first glance, the influx of notifications and amount of social media apps available reduce the initial shock and make the number seem n ...more
Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in ...more
YouTube has a couple of basic gestures: you can double tap each half of the video to skip forward or back ten seconds, and you can swipe down to minimize the video. But wouldn't it be more useful if there were gestures to control brightness and volume? Well, as with all things ...more
While the preview images for Android's upcoming "L" release just came out yesterday, the new firmware has already been rooted, as is standard with its openness. So if you were feeling reluctant to try Android L because it didn't support existing root methods, then you might wa ...more
There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely s ...more
For people who are having problems with certain parts of geometry, this video will offer you advice on how to find a missing angle on the outside of a triangle when you are provided with the measurements of the other two angles in the triangle. Since the sum of the angles in a ...more
There's a feature that debuted in iOS 7 that lets you to save your credit or debit card information in Safari so that you can auto-fill text boxes when purchasing something online. Unfortunately, you still had to manually fill in your card info the first time, and if you wante ...more
Got a clogged kitchen sink? Before you reach for the plunger, see if you can fix the problem using Alka-Seltzer tablets and white vinegar. Simply drop four Alka-Seltzer tablets down the drain and follow that with 1 cup white vinegar. Let sit for 10 minutes before flushing the ...more
Apple has acknowledged a problem with the sleep/wake key, better known as the power button, on a certain number of iPhone 5's manufactured through March 2013. As a result, the company has announced the iPhone 5 Sleep/Wake Button Replacement Program, which will replace the powe ...more
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 655th installment in their series of digital spreadsheet magic tricks, you'll learn see how to cre ...more
Is your tiny city apartment or super modest house starting to feel a bit too cramped for comfort? While most of us don't have the luxury of hiring an architect to add on more kitchen space, or the money to live in a more spacious apartment, there are a number of simple things ...more
The SATs are a very valuable college entrance test and could determine if you're accepted or denied to your favorite university. So, once you've learned to ace the SATs and have already taken your test, get your scores as soon as they're out! Don't sit in dreaded anticipation— ...more
The past year brought about a number of trends in the smartphone space. More immersive displays, better processors, and portrait mode for cameras come to mind as big steps forward. One of the most polarizing trends that continued in 2017 is the removal of the 3.5 mm headphone ...more
Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to ha ...more
Getting on the phone for customer service can be extremely frustrating. First you've got to find the correct phone number for your region (good luck trying to get customer service from a sales department), then you have to listen to the annoying automated system to navigate yo ...more
Part I Start by casting on the required number of stitches, onto one of the double-point needles. Divide these stitches between three needles by slipping 1/3 of the stitches (beginning with the first stitch you cast on) onto each of the other two needles. Making sure the stitc ...more
The factorial of a number n can be defined as the product of all positive integers that are greater than 0 but less than or equal to n. Almost every scientific calculator has a built in "factorial" function. This makes the really cumbersome process of multiplying each number ...more
If you find yourself switching between Android devices frequently—for instance, your Nexus 6P and a Samsung tablet—you've probably noticed how the button placement can be different. Normally, it's back, then home, then the recent apps button, from left to right. But Samsung de ...more
Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also inclu ...more
If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high- ...more
Follow this quick video demonstration to see how to knit a shaker rib stitch. The shaker rib is also known as the half fisherman, and that's because it's not as bulky as the fisherman rib. During this process, you'll even see how you can knit one below, or k1b. For the 1st ro ...more
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experienc ...more
No, your Apple Watch isn't totally hacker-proof, despite what some have claimed. The basic idea behind its security is that the Watch can detect when it is removed from a wrist, and automatically requires a passcode to be entered if removed (if one is set up, which is a requi ...more
Fractals and stars are two of the most beautiful and complicated-looking classes of geometric objects out there. We're going to explore these objects and how to carve them on a pumpkin. Unlike the last one on carving polyhedral pumpkins, where we used the entire pumpkin to car ...more
This video will show you how to block caller ID on the iPhone 3G. Follow these steps to block caller ID on the iPhone 3G: Go to your settings menu and click on the phone option. Click on the 'show my caller ID option', and turn it ON or OFF. Now your number won't show up if yo ...more
Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attack ...more
It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploi ...more
Figure out the 17th puzzle, entitled "The Bunker", in Assassin's Creed 2. Code wheel puzzle: Here’s a tricky one; your clues are “<” and “2,” and the only advice you’ll get from your handlers is that maybe there’s “something we can count” on the strange symbols. In this case t ...more
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown ...more