You can't beat Samsung's hardware, but their software still isn't for everyone. That's the thing, though — software can be replaced. So if you're more a fan of Google's vision for Android, but you can't get enough of Samsung's beautiful screens and build quality, you're just 1 ...more
For a built-in app, Notes works pretty well and can stack up against some of the best third-party note-taking tools. Apple continues to update it with each iteration of iOS, adding new features and improving existing ones to make jotting down your daily thoughts a smooth and e ...more
One of Apple's key features for iOS was always its "what you see is what you get" philosophy. Sure, there were small tweaks and complicated workarounds to customize an iPhone, but, for the most part, all iPhones felt similar. These days, however, changing up your iPhone's look ...more
Apple just released the first beta for iOS 14.2 to iPhone software testers today, Monday, Sept. 21. This update brings a new Control Center tile for Shazam music recognition, a redesigned Now Playing Control Center tile, and a new "People Detection" feature in Magnifier. A si ...more
Apple's iOS 14 is here. With it, you'll see over 200 new features and changes hit your iPhone, including home screen widgets, inline replies in Messages, and cycling routes in Maps. Here's how you can get your hands on the brand new update. Apple released iOS 14 to compatible ...more
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll ...more
Are you tired of endless rows and columns of apps on your home screen? Before iOS 14, your only option was to hide apps in folders, uninstall them, or use some sort of elaborate workaround. You could hide a few stock apps easily enough, but that's it. Now, in the latest versio ...more
If you've ever been into custom ROMs, you likely know the Dirty Unicorns name pretty well. It's been synonymous with unique features and awesome tweaks when compared to stock. Recently, Dirty Unicorns has returned again in a big way with some neat features for Android 10. Typ ...more
Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over ...more
Your iPhone's almost out of battery power, there's no wired or wireless charger in sight, and you left your portable power bank at home. You don't want your battery to die, but you still need to use your iPhone. This is when Low Power Mode comes in handy, but you could be wast ...more
The future of TikTok in the U.S. is all but certain. Microsoft, Walmart, or Oracle could save the day by buying the company, TikTok may win its lawsuit, or China's new restrictions could halt everything — but all could fail. Just like Vine before it, TikTok could be on its way ...more
Your iPhone and Mac can speak to each other in many ways, allowing you to start work on one device and seamlessly switch to the other, share clipboards between the two, and pick up phone calls and answer text messages on both. The compatibility is incredible, but there's even ...more
If you spend most of the time on your iPhone shooting photos and taking videos, you'll be happy that Apple has improved a few aspects of its Camera app in iOS 14. Even if you're just a casual photographer or videographer, you'll benefit from the new changes to the default came ...more
While most smartphones these days take great video, the iPhone is the camera to beat. Recent models like the iPhone 12 and 12 Pro shoot in 4K resolution from every camera, and even a budget device like the iPhone SE delivers an excellent 4K image from the rear shooter. That sa ...more
When it comes to washing clothes, the laundry symbols on your tags might as well be hieroglyphics. They're difficult to interpret, easy to forget, and even easier to ignore. But if you don't want to ruin expensive designer clothes, blankets, and other fiber-based materials, yo ...more
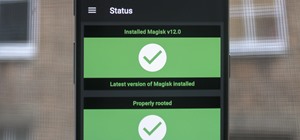
Bootloops are a risk inherent to rooted devices — with great power comes great destroyability, after all. While custom recovery sometimes provides a quick fix when you flash the wrong Magisk module, with TWRP becoming more challenging to implement thanks to Android 10, the sol ...more
Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensur ...more
In iOS 14, your iPhone can have home screen widgets, but you can also keep using widgets in the Today View if that's more comfortable for you. You could actually use both if you wanted. But when it comes to the Today View, the process for adding, removing, and editing widgets ...more
The ability to hide entire pages on your iPhone's home screen is an excellent privacy upgrade packed into iOS 14. That said, it can be a bit of a pain to find and open the hidden apps on those pages in a timely fashion. Luckily, iOS 14 has a solution that makes opening those a ...more
The smartphone market is stagnating. Without hordes of new users rolling in every year, the best way to boost profits nowadays is to poach customers from the competition. That's exactly what Apple appears to be doing with iOS 14. As a longtime Android user, I'm genuinely intr ...more
After teasing the feature in Android 10, Google finally added proper native screen recording to Android 11. But when you start a capture, you'll see a small red indicator in your status bar as long as recording is ongoing, which can really distract from your video. Thankfully, ...more
Facebook Messenger is a messaging app first, but of its more than 1.3 billion monthly users, 32 percent use its video chat feature at least once every month. While it may seem pretty straightforward to video call with family and friends on Messenger, there are many tips and tr ...more
The native timer feature on your iPhone works well enough that you probably haven't even thought about installing a third-party timer. With just a few taps, you can get a countdown for any amount of time up to 24 hours (or one second shy of 24 hours, to be precise). But as fas ...more
As soon as you try recording a video in the Camera app on your iPhone, any music playing on your device comes to a halt. Apple Music. Spotify. Pandora. Tidal. Deezer. No matter what you're listening to, as soon as you switch to "Video" in the Camera app, the music will stop. H ...more
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information i ...more
It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues. First, Google has opened up Meet, its video conferencing services for G-Suite subscribers, as a free service for ...more
Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, ...more
Android 10 added the framework for OS-wide chat bubbles, a feature popularized by Facebook Messenger. The new system allows you to interact with incoming messages as if you were in the app — all without having to leave your current app. In Android 11, this feature is finally a ...more
Software issues occur more frequently on jailbroken iPhones, though, they're usually minor bugs that can be fixed easily with a respring. But if your device freezes up, restarting is the only way to get back to normal, which also means having to re-enable your jailbreak. There ...more
In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top po ...more
Every iPhone Apple currently sells, including the brand new iPhone SE, ships with Portrait mode, injecting DSLR-like depth effects into your Camera app. If that's the shooting mode you use more than any other, it may feel tedious having to switch to "Portrait" from "Photo" eve ...more
There are two main ways to view how much battery is remaining on an iPhone: the battery level icon and battery percentage. Out of the box, the second-generation iPhone SE only shows the battery level icon in its status bar, which only gives you a rough idea of how much juice i ...more
The Home button on an iPhone does a lot. That's not necessarily news for anyone who's ever owned an iPhone with a Home button, but what you might not know is that it's capable of so much beyond the standard everyday functions. So if you have an iPhone 7, 8, or the new SE model ...more
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever i ...more
Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible. Thanks to some Samsung-developed apps ...more
If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android. Th ...more
It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for ...more
Despite Android's flexibility in regards to customization, the options available in stock Android are pretty barebones. It is only with the help of third-party apps that we can entirely transform sections of the UI to our liking. And thanks to a new app, we can modify another ...more
Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with ...more
An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires. Before you keep reading, know that this project is not geared ...more
Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's ...more
Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new ...more
Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long ...more
Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem. ...more
You've just picked up your new Samsung Galaxy S20, S20+, or S20 Ultra — but wait. After you turn it on and restore your data, there a few apps you should install to get the most out of your updated phone. Installing these eight apps right away will help maximize your experienc ...more
The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than ...more
When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a real ...more
In older Android versions, you could flood your status bar with a wall of notification icons. But starting with Android 9, Google made it to where you can only see four icons by default, and it was mostly done to accommodate phones with notches. But Google's only notched phone ...more
It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploi ...more
On Twitter, you can pin one of your tweets or replies to your profile, so it's the first post people see when they visit your page. However, Twitter prevents you from pinning someone else's tweet. You can't even pin something you retweet. There is a clever workaround, though, ...more
If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional ...more
It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well. This is ...more
A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it ...more
Something entirely new for many people is where the future of navigation is headed — gestures. Gesture navigation not only gives you more screen real estate, but it allows for a seamless experience without needing to lift your finger as much. OnePlus knows you want to tap less ...more
Apple said goodbye to iTunes with the release of macOS Catalina, breaking up music, videos, and podcasts into their own respective apps, Music, TV, and Podcasts. But without iTunes, what app's in charge of interfacing with your iPhone? That would be Finder, and you use it to s ...more
In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools t ...more
It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released D ...more
So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone i ...more
We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcu ...more
One of the biggest reasons to go with an iPhone over an Android device is Apple's interconnectivity. iPhones, iPads, and macOS devices are all connected in a way that allows seamless transition between devices. Android lacks such a feature by default, but that isn't the end of ...more