For some odd reason, the Netflix app likes to disable the Nexus Player's built-in screensaver. It doesn't use its own, it simply keeps your screen on indefinitely, which of course can lead to screen burn-in. This is not just an Android TV issue, as the Netflix app does the sam ...more
Keyless entry remotes are great, but they don't always work how you want them to. One of the most common complaints is that they just don't reach far enough, and there's nothing more annoying when you can't remember where you parked. After all, what's the point of having "remo ...more
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from eve ...more
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to ...more
Mobile augmented reality developer Blippar's mission is to construct a computer vision map the world, with visual recognition of thousands of notable buildings, bridges, castles, holy places. A major step toward that goal has been taken by the company this month with the annou ...more
By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
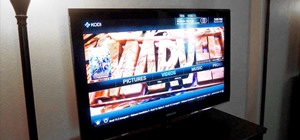
Since the Nexus Player is an Android device at heart, there are already several internet browsers that can be used on the streaming set-top box. Chrome, Firefox, and a few others will run perfectly fine, but the trouble with these is that you need a mouse to use them. If you ...more
When you need a file on your Mac as soon as possible, you usually have to get your MacBook or hop on your iMac, Mac mini, Mac Pro, or Mac Studio. But that's too much work if you're in bed, lying on the couch, or outside in the fresh air. Why even bother when you can access tha ...more
You may not always want to, but there will probably be a time when you'll want to know if an email you send — like a job application or a support request — is opened by the recipient. It's actually easy to implement, and you may be using an email client on your device right no ...more
If you have a PlayStation 5 and an Android phone running Android 12, you can stream and play your PS5 games right from your mobile device using PS Remote Play. While simply pairing your PS5's DualSense wireless controller with your phone will give you the basic controls to pla ...more
With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good cont ...more
Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device. Don't Miss: Turn Your Old Android i ...more
Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expa ...more
There's never been a better time for streaming movies and TV shows on the go. With so many services available, the only limitation to your enjoyment is your phone's accessories. Whether you're buying for yourself or someone else, here are some of the best gifts that improve th ...more
The iOS 12.0 beta earned admiration for its superior performance to last year's controversially buggy iOS 11. That doesn't mean it was free from problems before the stable release went live. During the initial iOS 12.0 beta testing phase, there were plenty of bugs and glitches ...more
While Google Stadia currently needs to be sideloaded on Chromecast with Google TV, there are a handful of games that are compatible with the streaming device and require a gamepad. But you don't need to buy a specific controller just for your Chromecast, you can use one you al ...more
The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until ...more
Matteo Pisani, CTO and co-founder of Remoria VR, has managed to do something the folks over at Google said couldn't be done for at least a couple of years. With a little bit of tinkering, Pisani was able get his Google Daydream VR headset and remote to work on an iOS device. V ...more
You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images ar ...more
This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product. One of the bigges ...more
Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences. As I said back then, today I'll be explaining the other way you may use to redirect execution flow: using a NOP sled, along ...more
If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?" Many of the top names in the industry from the 2018 edition remain the same, but their positions have shuffled. The p ...more
Musical boxes are best known for their kitschy designs and somewhat trivial renditions of musical masterpieces. They tend to frequent the dresser of young girls or elderly woman hanging on to their youth, and for the most part, they remain cutesy and harmless, but when feature ...more
Prius models that are equipped with tilt-slide moon roof have a remote control button on their smart keys for the remote air-conditioning system. Before leaving the vehicle, make sure the headlights are switched off or set to auto. All windows are closed and check the temperat ...more
XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection betwe ...more
General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them. Darco, whose real name is Robert Sun Qu ...more
Learn how to play "Time For Me To Fly" by Jonas Brothers, an acoustic guitar tutorial. Follow along with this demonstration, lyrics here: "Time For Me To Fly" [Verse 1] I've been wasting my time I've been losing my mind I've been running races Still don't know what I've been ...more
In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack. Before we start hacking, let's familiarize ours ...more
This video is a discourse about saltatory conduction in the neurons. According to the author, it begins with the opening of a gate on the membrane of one of the dendrites of a neuron, and positive charge enters through this gate. The positive charge spreads throughout the cell ...more
Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it. I'm sure at one time or another you've heard that hack ...more
No longer do you need to crowd around your tiny smartphone to watch a funny YouTube video with your friends. If you've got a display nearby with a web browser and internet access, you can take control of it with your mobile device for free with the new Clik app. It's simple. ...more
Remote desktop is a tool that can be used to access you computer from another device over a network. You can also connect to a remote desktop on Iphone or Ipod touch. Note that you will need EDGE and 3G for this to work. The files you need to connect are Mocha VNC Lite, and th ...more
You can connect to an SSH server or connect to an FTP server from you windows computer. Open the run dialogue in your windows and type in cmd. Press OK to open the command prompt. Type in ftp command and press enter. This brings up the ftp prompt. Type o to connect to a server ...more
Prepare yourself for more info than you need for winning The Saboteur for the Xbox 360. See everything involving the second mission in the Prologue: Better Days. Sean will flashback to 3 months prior to the opening mission. After the cutscene introduces some new characters, ho ...more
Pull off this easy prank, and – without causing any permanent damage – watch your coworker squirm with frustration. You Will Need * Access to a coworker's computer * A phony desktop graphic * A flash drive Step 1: Create a phony desktop Create a few on your desktop and give t ...more
Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can stea ...more
In this video from iPT2gGeec we learn how to control an iPhone from your computer. You need a jailbroken iPhone to do this and use a program called Veency. Open Cydia. Search for Veency. Install it. That is all you need to do with your iPhone. Now to get it to work on your co ...more
Sputnik was the very first man-made object to be sent into space. Though it was a truly epic accomplishment, all this Soviet sky surfer actually did was transmit a constant beeping noise back to the surface. Your young students can learn about the history of space travel whil ...more
After his fall from Asgard into space, the Asgardian Loki meets the Other, the leader of a warmongering alien race known as the Chitauri. In exchange for retrieving the Tesseract,2 a powerful energy source of unknown potential, the Other promises Loki a Chitauri army with whic ...more
Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more paral ...more
Artist Austin Houldsworth of the UK has come up with a device that drastically speeds up the process of fossilisation. Entitled Two Million & 1AD, Houldsworth is capable of creating a fossil in a few months (which otherwise might require thousands of years). Houldsworth is cur ...more
This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here ...more
Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it. Why Meterprete ...more
Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security profe ...more
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
Little boy gamers don't care about coffee tables. But when a little boy gamer grows up, he's gotta have some kind of furniture. Like a giant NES coffee table with a fully functionally, giant NES controller. So Matt (grown boy gamer) built one: "Opening the lid reveals the sto ...more
In this tutorial, we learn how to map network driers from a remote server. First, go to run on your start menu, then type in the id address or server name for what you want to access and press enter. Now, right click on the folder you want to map and click on map network drive ...more
Hallelujah, a miracle tool has been released to the world. This Windows/Mac tool is called Spirit and it enables you to jailbreak any iPhone, iPod Touch or iPad quite easily. And Gizmodo is all over it, with an in-depth guide on exactly how to do it. Some of you may be hackin ...more
In this video we learn how find out IP addresses of websites and shut down the computers with those IP addresses. To do this click "start", then "run" then type command prompt. In the command prompt type "tracert website" (example tracrt Google.com) then hit enter. Various IP ...more
In this video tutorial, viewers learn how to use Remote Desktop on Windows Vista to connect to another computer over a network connection, specifically Windows XP. You can get access to your Vista applications or data stored on a remote computer from your XP PC. Users will ne ...more
In this Electronics video you will see how to set up the Pocketwizard with a Nikon SB-800 and SB-900. When you use Pocketwizard as a master to trigger the flash, the remote flashes for a working distance of 1600 feet as against 33 feet. First attach a Pocketwizard unit to the ...more
Shannon Smith shows how to upload files using Filezilla in this episode of No Mac, No Cheese. Filezilla is useful in assisting you with putting files onto a web site. Simply type in your web address, user name, and password. Then create a folder and name it appropriately. Adju ...more
Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implem ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and e ...more
Nintendo's Wii Remote came close, but never has a video game peripheral garnered such adoration from the hacker community than the Kinect. Since the release of Microsoft's controller-free gaming device last November, there has literally been thousands of fun and useful projec ...more
1. Involves gate crashing a big awards event or film opening (like what AAF did with their song 'These Days': http://www.youtube.com/watch?v=JNM2tV3PA_8). Pretty much cause a huge disturbance to the proceedings of an event and see how long it takes for the police to shut you d ...more
Stephen Hawking asks: "is time travel possible? Can we open a portal to the past or find a shortcut to the future? Can we ultimately use the laws of nature to become masters of time itself?" The master of the universe writes into Daily Mail, and proposes a "HowTo" for time tr ...more