A Self-Protection Guide 1) You can help protect yourself from violent crimes. Self-protection involves:Avoiding crime * Without a doubt prevention is your best prevention against crime.Knowing what to do in case of an attack* An attack can happen despite your best efforts to p ...more
Want to keep your money and valuables safe while traveling abroad? Play it safe and outsmart thieves by placing your money, passport, jewelry and other expensive things in unexpected places. Sew a secret inner pocket in your pants, or if that's too much work, try cutting open ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing ...more
What happens when a person who has never played a building sandbox game tries it for the first time? Reality happens. The harsh reality of human nature. You would think playing with friends in a creation game would be utopia, but in truth it's more like being stuck with people ...more
Warning If you don't trust that these steps are safe or that they won't work, than have your computer/laptop backed up so you can restore it if necessary. Update all Windows software Everything needs to be up-to-date in Windows 7, so update any software that needs it. Choo ...more
Gunmetal gray is one of the coolest, most biker-chic finishes out there when it comes to jewelry making. If you enjoy working with filigree pieces in your bracelets and necklaces, why not make them less granny fantastic and more urban chic by adding a nickel-free gunmetal fini ...more
It is very important to change the oil on your lawn mower just as important as changing the oil in your car. The oil liberates, cools and cleans the engine. It is best to check your manufacturers information to know how often to change the oil. To change the oil you will need ...more
This video tutorial from ballader1 shows how to remove viruses, trojans, adware, spyware from your computer. To do that you need to download Malwarebytes application from malwarebytes.org. Open your internet browser and enter malwarebytes.org URL address. Make sure you down ...more
The perfect solution to get your movies onto your computer! The Ripit app is simple, and does exactly what it says it does: Ripit! Just put your DVD in your drive, open Ripit, and press the rip button. Ripping your DVDs can be a useful step in organization of your movies and k ...more
This is a video tutorial that is showing its audience how to replace the digitizer screen on a 2nd generation Ipod Touch. The first step is to remove the screen from the Ipod touch. Secondly use a safe pry tool and run it between the backing of the screen and the glass, this w ...more
This tutorial describes the procedure to remove autorun.inf and boot.com virus. This virus is commonly called as resycled/boot.com virus, which could damage the system files and may steal important information from the system.This can be removed by any malware / spyware remove ...more
Through our friends at Azucar Surf we found this lovely surf house for sale. This house is for sale by owner Michael Lawson. This is what he has to say about it: This house is located just on the edge of town, just a stone’s throw from cabanas beach. The property consists of ...more
This is a great video from Andrea Cook. To cook cinnamon rolls start by preheating your oven to 350 degrees. You will need an oven safe pan to cook the cinnamon rolls. To keep them from sticking the video suggests spraying the pan with no stick cooking spray. Then pop open the ...more
The tutorial shows you how to make a professionally looking Google Chrome logo in Photoshop CS4. To start, download the Google Chrome logo, as well as an Earth picture, in a Zip file from Inteltuts. Next, open the logo file in Photoshop CS4, turn the white background layer int ...more
In this video tutorial the instructor shows how to make backup copies of your UMD games. You can rip the ISO's of the UMD games and make copies of them. Open the PSP and go to games and launch the current custom neighborhood model. Go to settings, configuration and then go to ...more
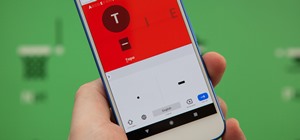
Afraid you're going to forget the password to something important? Well worry no more. Blackberry expert Darci Larocque shows how to keep those passwords in a safe place in the unfortunate event that you manage to forget your passwords like your visa number or your passport nu ...more
In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and m ...more
Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or bro ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Getting up and down in Minecraft can be extremely time consuming without the assistance of fly mods or speed hacks. If you're a pure player looking for a safe and effective way to t ...more
Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch. Be sure to read the rundown of the new 1.8 features and share your thoughts in the 1.8 general im ...more
Gone are the days when you had to carry a clunky DynaTAC to make phone calls, pocket phone book for you contact list, Sony Discman for your tunes, and wallet for you cash and credit cards. Today, all you need is your smartphone. To be specific, Google's Nexus S 4G on Sprint. ...more
Aside from food, oxygen, sunlight and water, there are other necessities that humans arguably need today to survive—clothing, love and shelter among them. Almost everyone wears clothes, needs somebody (or something) to love and a place to call home. And what's the one thing th ...more
You see before you the humble block: This single, unassuming block couldn't possibly hold anything of value, right? That's only what we want thieves to think! With a little bit of magic, this block (or any other basic block) can be turned into a secret chest capable of keepi ...more
Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor. Tor runs your traffi ...more
Mugshots aren't just for criminals anymore. In the world of competitive Scrabble, no one's safe from the lens of photojournalist Roger Cullman. For the last couple years, Cullman has been hitting up the Scrabble circuit with hopes of immortalizing some of the world's best Scra ...more
Now that Google+ is open to everyone, there are a lot of new people who aren't techies trying out the service. When you first sign on, it can be overwhelming. I've decided to round up a bunch of resources to help you get started, and recommend some people for you to follow, if ...more
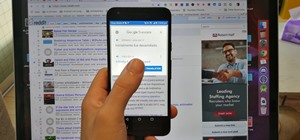
For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide t ...more
Hey, would you like to be as cool as this: You wish! But you could do the next best thing, and that's capturing your earth shattering game play with the Easycap DC60. Originally retailing for forty dollars, you can buy this at Amazon for $8.50. This device will capture video ...more
In this how to video, you will learn how to replace the glass digitizer on your iPhone 3G. First, remove the two screws at the bottom and the SIM card at the top. Once these are removed, use the safe pry tool and run it at the bottom between the bezel and back cover. Slowly re ...more
Curtis Smith of Southwest Yard and Garden show viewers how they can dry fruit from their garden. First, you need to wash your hands before handling your fruit. To wash your hands you want to remove any jewelry, wet your hands, lather your hands and rub them together for 20 sec ...more
The wigwam was a shelter constructed by many Native American peoples in the eastern part of North America. With this video, you will learn how to construct a wigwam of your own using very basic materials. You Will Need • 25-30 green tree saplings • Knife • Cord or rope • B ...more
You can make a rocket at home using these items found around the house. Icing sugar, measuring tape, a PVC pipe, black marker, hammer, flat headed bolt around 18 millimeters wide , mortar and pestle, drill, drill bit size 5 millimeter, potassium nitrate and kitty litter. You ...more
Before you get started exploring a big new city or even just getting reacquainted with the one you live in now, make sure you aren’t putting yourself in any unnecessary danger. Memorize good traveler habits that will keep thieves and scam artist off your back. Don’t let your ...more
Prepare to delve into the world of L4D2 and check out the gameplay for Campaign 1: Dead Center - Streets. Stock up and open the safe house door. You should see a bunch of infected milling about here. Kill them and make your way straight up the hill past the port-o-potties. Tur ...more
Performing magic with simple, everyday objects is cool! And Ryan Oakes is going to show you how to perform an amazing little trick with a quarter. Sometimes we use materials that require adult supervision... like scissors so make sure you have friends and family around wheneve ...more
If you're bound to a wheelchair and living in Orange County, California, then this video is a must-see if you use public transportation. It will show you the steps to boarding an Orange County Transit Authority (OCTA) bus the right way, when in your wheelchair. 1. Arrive at t ...more
Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with ...more
Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information y ...more
The agents of empire do not always arrive with warning. When you are besieged, surrounded, and infiltrated, imagination is often your best weapon against the oppressors. If all you have at hand is some duct tape and a disposable camera, fear not, you have the makings of a powe ...more
Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and r ...more
Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be i ...more
How to Crack Passwords Faster by Putting Your GPU to Work with HashcatSecurity on the internet is always changing. Not too long ago, having a 10 character password meant that you were safe from all forms of hash cracking. Hash cracking is when you take a string of characters t ...more
There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of th ...more
Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at ...more
Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by cha ...more
Downloading images from Google Images search can be a time consuming and DANGEROUS process. On more than one occasion, while trying to save the full size image and being forced to the originating website, I have accidentally come across malicious websites. Because of this, a ...more
The United States is a hierarchical country where the weak ones are at the bottom and the powerful ones are at the top. Garment workers are at the bottom of the list although they are the most important. Without them there would be no fashion industry. They sew and cut the gar ...more
This is prank is a 'bit' complicated to do but if you manage to do it, it will be the best prank ever made for good. I think the best man for this prank should be Bam as his chances not to die during the fall down are the best : - Go to some scene shooting somewhere in the wo ...more
Make sure the bike is properly fit to the child. She should just be able to stand over the top bar of the frame without touching. Install training wheels on the bike. Have the child wear a helmet. When first starting, knee and elbow pads, as well as gloves, are a good idea. ...more
Life stinks. Literally. Daily living leads to lots of lingering smells. Household odors from cooking, kids, pets, bathrooms, and guests can accumulate. Get rid of them with some simple remedies. You Will Need *Baking soda *Essential oil *Cotton balls *Plastic containers *Lem ...more
Feeling unprepared for the next earthquake? In this tutorial, learn what to do and what not to do to survive "the big one". You'll be surprised to learn that hiding in a doorway is a myth! You Will Need: • A safe place • Sturdy shoes • A fire extinguisher • A flashlight ...more
Looking at homes is the fun part. But before you go house hunting, make sure you have your financial ducks in a row. Step 1: Know your rights Buying a home can be a complicated legal process, so begin by familiarizing yourself with your legal rights. Step 2: Shop for a mortg ...more
So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for? And what about your movies? W ...more
Rockets are lots of fun when you are launching them. However, finding them can be an arduous if not maddening task. Fancy space rockets have lots of tracking equipment to make touchdowns as simple as pie. Today, we look at embedding LEDs into your hobby rocket for easy night f ...more
If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly ...more
Taking apart batteries is one of those things that every adult you've ever known has warned you against. Today, we break the taboo and dive into a lithium battery. Lithium has some pretty cool properties—it burns instantly in water and glows blindly bright under flame. And wit ...more
Anonymity is very important to many internet users. By having your "e-identity" exposed online, you can be stuck with a number of unwanted issues, such as: Privacy invasion. Internet tracking. Exposure to being hacked. However, what if we wanted to spend money anonymously? T ...more
Having a custom Linux distro can be the coolest thing ever. Most of you will probably be satisfied with any particular Linux distribution, but I know I'm not the only one out there who wants it to have custom configurations and programs preloaded while leaving the bloatware be ...more
Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person ...more