As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfor ...more
This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartblee ...more
A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open. So, how would y ...more
Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion ...more
I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe. Until recently, if you wanted to use strong encryption you had to either learn d ...more
In the early days of the internet, if something was there and not password protected, you could see it. In the process of becoming the indispensable work and entertainment resource that it is, the internet also grew the same borders that countries have while also getting less ...more
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in. Starting with the BlackBerry KEYone, ...more
OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well. Android 8.1 Oreo acts more as a revision to Android ...more
The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix ...more
The Xposed Framework is an incredibly powerful tool. But because of this power, there's a chance that something could go wrong when installing a broken or incompatible module, which can cause bootloops or even soft-brick your phone. Depending on how bad the situation is, the ...more
Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a compute ...more
Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remote ...more
Apple Watch owners know there's a built-in way to remove water from the device's speaker. However, even though modern iPhones are IP67 and IP68 water resistant, there's no official way to deal with water-clogged speakers that can muffle audio and cause prolonged damage if not ...more
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet. So no, there's no such ...more
If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while i ...more
Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiri ...more
Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all o ...more
Microbial cells can improve the functionality of clothes in creative and useful ways, including cooling us down during a workout or making clothing glow for better visibility. The innovative products were developed by a team of 14 researchers from MIT, in such broadly diverse ...more
Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an ...more
Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments. Welcome to my 9th post, this tutorial will explain how to extract and decrypt WhatsApp database from the Victim's android system. ...more
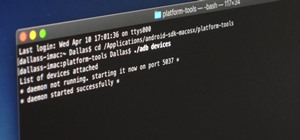
Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC. After rooting, you can enjoy many of tomorrow's features to ...more
You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root. The big 'R' word can be intimidating for the new ...more
THE FERRISWHEEL!!! Lifts and THROWS are a great way to spark up a dance routine! Practise in a large open space and be safe!!! Video: . ENJOY!
Safari is an excellent app for all your web browsing needs, but Apple gives you the freedom to choose a different default web browser on your iPhone to open links in. If you primarily use a third-party web browser like Chrome or Firefox on your computer or tablet, changing you ...more
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to ...more
Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can. After four films, the dystopian horror The Purge is jumping to the small screen on USA Networks as a television se ...more
Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat. Most Linux distributions are highly c ...more
Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google. Google offers ...more
Full disclosure: I really like Apple's stock ringtones on the iPhone. After all, there are over 50 to choose from if you include the classic ones. With all that choice, why would you ever need more? Personally, I get bored easily, and I'd like my music to play when people call ...more
Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now. From what I can tell, it's a very safe a secure method keeping passwords, links, and personal stuff encrypted and online. TURTL https://turtl.it Turtl is ...more
With over 500 million downloads on Android alone, I find it safe to assume that most of us use the Chrome Browser on our mobile devices; it's great for reading articles with Reader mode enabled, syncs open tabs and bookmarks across all your devices (as long as you're signed in ...more
Pumpkin carving and decorating is a favorite October pastime. After you've carved an amazing design or face into a pumpkin or two, you want to show it off through your window or set it out on your porch for the neighbors to see. But, without knowing the tricks to save your ho ...more
Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house. Probably, you already know what SSH means, but for ...more
By now, Samsung's Multi-Window Mode is a pretty well-known feature. With other manufacturers now recreating this functionality in their own flagships, like LG, it's safe to say the feature has been a hit with consumers. But a lesser-known aspect of Multi-Window Mode might jus ...more
The term "selfie" is taking the world by storm. Having been around since 2002, the slang word for "self-portrait" went into hyperdrive thanks to the addition of front-facing cameras on mobile devices. It's even popular enough to have been included in the Oxford Dictionary, and ...more
You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down. There are a surprising number of new privacy and security-related issues in iOS 7's default settings, from allowing A ...more
With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll t ...more
The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's si ...more
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta. The iOS 13.6 beta first appeared as an iOS 13.5.5 ...more
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter th ...more
In the Western world, the only time you'd associate food with cockroaches is health code violations. And while other cultures and countries are more open to cooking with and eating these and other little buggers, insects are probably not a food trend that will be adopted by th ...more
Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information. While your Mac does a good job of protecting you, thanks to built-in features l ...more
Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long ...more
Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that ...more
Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebo ...more
Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a b ...more
One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messagi ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of ...more
Safari isn't the only web browser on your iPhone or iPad that will let you add icons to your Home Screen for progressive web apps and website bookmarks. Apple gave developers the key to its "Add to Home Screen" feature, and your favorite iOS or iPadOS web browser may already s ...more
Apps can learn a lot about you just by reading information about your smartphone. They can easily track what device model you have, your phone number, and in some cases, your hardware MAC addresses. Many third-party apps will only track your device values for advertising purpo ...more
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll ...more
Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you. ...more
It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from website ...more
When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden ...more
Almost certainly, you've closed out of a webpage that you didn't want to at some point in your iPhone-owning life. Whether you accidentally swiped the tab away or closed it only to need it moments later, tab-regret is just a part of our internet culture. Luckily, Safari on iOS ...more
With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it req ...more
Maybe you decided to make your own pumpkin pureé because of all the buzz about canned pumpkin actually being squash (which, by the way, is a load of bull: it's made with ugly pumpkins, but pumpkins nonetheless). Or maybe you just wanted to be that person that proudly proclaims ...more
When to throw meat away is a common question, and one I often ask when faced with meat sitting in the fridge after a few days. With vegetables, you can usually tell on sight (or with this guide) when they're past due, but meat is not as simple. As long as meat is refrigerated ...more
Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow. Scenario Let's say, that we have done all the recon(both passive and active) and we have scanned the web serve ...more