Welcome back Hackers\Newbies! Hey guys first of all I would like to explain my absence here in NullByte. I got a little "occupied" with "other things". When I got back, I saw all these HowTo's, articles, Help Questions, I decided, I need to share more of what I have, to you g ...more
Although iOS 8.4 was just released, the team behind the iOS 8.3 jailbreak have updated their tool for the latest operating system, and will work on an iPad, iPhone, or iPod touch. So if you've been wanting to get all your tweaks back, or want to start exploring all of Cydia's ...more
A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email co ...more
These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more. But just because there are lots of opti ...more
Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack. Hello, my hacker friends! Today we are going to look at how hackers can take advantage of the system, and repeatedly crash the ...more
We have all seen videos of people walking off of platforms and into street signs because they were too distracted by their phones to pay attention. This has become such a problem that cities have even considered fining pedestrians for texting and walking. Even though I find t ...more
As a Mac and Sasmsung Galaxy S6 user, I quickly realized that the two devices don't play well with one another out of the box, and using ADB commands to record my Android's screen isn't as simple as it is would be with a Windows PC. Though you might feel like attempting to us ...more
Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important). A while back I covered an app that sent out a ...more
To contemporize a popular quote, "A cluttered desk(top) is a sign of a cluttered mind." Of course, it's difficult to maintain a tidy desktop... as you read this, mine is cluttered with screenshots, folders, Word documents, videos, pictures, and apps. While a messy desktop is ...more
With recent security breaches in the news, there is no better time than the present to make sure you know exactly what's happening on your device. Most of us trust our friends, but sometimes you'll lend out your phone and get it back with some apps newly opened, meaning that ...more
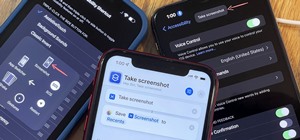
While screenshotting a received Snapchat has never been a hard thing to do, saving one without being noticed is a completely different story. Previously, you would have to have either a rooted Android or jailbroken iOS device to save one of those self-destructing messages unde ...more
Keeping prying eyes off your device isn't always the easiest thing to do, especially once you lend somebody your phone to make a call. Seems that whenever someone is scrolling through your pictures or checking out your new phone, they always end up somewhere you don't want the ...more
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you ho ...more
For those of you who've already gotten Beta Preview or Developer Preview access to Mac OS X 10.10 Yosemite, I highly recommend installing it on a separate partition on your hard drive. There have been many reported bugs and even blank gray screens that prevent access to the s ...more
If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps. ...more
Watch out Samsung (and you too, Pebble, Sony and the still unrealized Apple), your hold on the smartwatch market is about to get a lot less firm. Announced today, Google has released Android Wear, their platform for developing smartwatches, along with a preview of the Moto 360 ...more
Recently, I offered a guide detailing how to run two separate windows on a Nexus 7 tablets for better multitasking. While extremely useful, that mod was limited to only two windows, and you also needed root access to use it. Today, I'll be highlighting a non-root Android app ...more
Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mea ...more
...since the old reliable F8 doesn't work anymore. There is a way to do it. Step 1: Open the Charms bar, go to Settings, then select Change PC Settings. Step 2: Go down to General, then scroll down and find Advanced Startup Step 3: I'm unable to get images to show you the ...more
Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you ...more
The allure of Snapchat is that all pictures and videos sent through the app vanish a few seconds after being sent. They're completely obliterated not only from the phone, but from the Snapchat server, as well. The popularity of the application has even incited Facebook to rele ...more
One of the main reasons why the Samsung Galaxy S III has dethroned Apple's iPhone 4S as the best-selling smartphone in the world is due to Android's open-source operating system. The vast spectrum of customization that comes with Android has become one of its focal points, all ...more
Let's say you forgot the code to your Master Lock combination padlock. What can you do besides buy another one? Well, there's a surprising abundance of ways to open a combination lock other than with just the combination, some of which will even let you reset the code. Of cour ...more
Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got t ...more
What started as an accessibility setting for hearing aids turned out to be a super helpful tool for anyone with a good set of Bluetooth headphones. The problem is that most iPhone and iPad users still don't know about it. If you're one of them, you need to see what this underr ...more
There is no default option on iOS 16 or iOS 17 to lock your apps behind Face ID, Touch ID, or passcode authentication. However, a clever, easy-to-implement workaround will protect your sensitive apps from nosy friends and family temporarily using or looking at something on you ...more
The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having ...more
Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its ser ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps ar ...more
When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your de ...more
You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay sec ...more
If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a ...more
There's a way to get instant access to your most-used websites and webpages on your iPhone, and these shortcuts live directly on your Home Screen. Whatever you need fast, frequent, or more convenient access to, whether it's a vital web document or a web app without a native iO ...more
One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. ...more
In the past, if you upgraded to a new Galaxy or if you had to factory reset your existing one to fix an issue, you had to restore your home screen layout manually. Your wallpaper, widgets, icon placement, and launcher settings were all dependent on you to be put back in their ...more
Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem. ...more
I'm a new parent and I just moved into a new home. The first thing I wanted to do was ensure my toddler's safety in his new digs. That meant buying a bunch of baby-proofing products from Amazon, realizing most were junk, then buying some more until I found solutions for all my ...more
Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once i ...more
Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is maki ...more
Millions depend on Google Maps for directions, and it's easy to see why. The app comes with tons of features like offline navigation, location sharing, and more. Google is far from done, however, and continually improves upon its navigation app to make it even more efficient a ...more
These days, cellular connections can be just as fast — if not faster — than traditional internet providers. That, coupled with the prevalence of unlimited data plans, means less worrying about hopping on a Wi-Fi network to download something. However, try to install an app or ...more
OnePlus pulled out almost all the stops with their latest flagship, but there are a few areas where the phone falls just short of perfect. The single bottom-firing speaker leaves a lot to be desired, for instance, but thanks to the awesome development community for the OnePlus ...more
Carrier-branded Galaxy S9 models come with a ton of bloatware that you usually can't get rid of without rooting. With a little digital elbow grease, however, there is a way to disable bloatware on your S9 or S9+, and it's a lot safer that attempting to root and modify you prec ...more
When you accidentally close out of an important tab on your iPhone, Safari's "Recently Closed Tabs" list really comes in handy. However, when it comes time to clear the list, things get a bit complicated. There's no "Delete" or "Erase" button on this page, but don't let that f ...more
Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs. Coinbase has a ...more
The final developer version of iOS 11 was leaked a few days ago, but Apple quickly stopped signing it so nobody else could install it. With Apple's Sept. 12 event now over, the Golden Master (GM) version of iOS 11, the same version that will be released to everyone around Sept ...more
The internet's an amazing place. The entirety of human knowledge is now accessible in an instant, and all sorts of media can be streamed directly to the palm of your hand. But, of course, that also includes the darker side of humanity, so there's plenty of NSFW content floatin ...more
A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists righ ...more
Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking. Luckily for those o ...more
In case you didn't know, Google has an awesome app that gives you free money to spend on apps, games, movies, books, and virtually anything you can buy on the Google Play Store. The app is called Google Opinion Rewards, and all it asks in exchange for the Play Store credit is ...more
While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows. Blue Coat is notor ...more
Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels. "Why would I do that?" One might ask. Good question m ...more
Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record. OTR does all the right things to make your instant messa ...more
Remembering keyboards shortcuts can prove difficult, especially when there are so many to remember, not to mention that they differ from app to app. While tools like CheatSheet can make them easier to use, today I'm going to show you how to enter them without using your keyboa ...more
Keyboard shortcuts can make using your Mac faster and easier, and leave your mouse feeling archaic. With just a few taps, you can save files, open new tabs, or play a movie—all without using your mouse even once. Don't Miss: 30+ Keyboard Shortcuts You Should Be Using on YouTu ...more
Since the new Mac OS X 10.11 El Capitan is brand new, I recommend installing it on a separate partition on your hard drive. This will keep your current Yosemite system safe from harm, and will let you easily switch back to it should El Capitan become unusable for any reason. ...more
If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achi ...more
One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issu ...more
The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try ...more