It's become a routine for many of us to ring in the New Year with pledges to finally get our budgets and finances under control. Unfortunately, it's also quite difficult to to keep those promises. Some of us will just dive into our resolutions and wing it as we move forward, w ...more
Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help ...more
With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain applicat ...more
When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists. As a repair tech, I would buy ...more
Beginners luck is a phrase I have always hated. But really, beginners luck comes down to not letting your experience in something get in the way of the idea. This past weekend, I drove to Atlanta for my first ever hackathon, HoloHack, presented by ThyssenKrupp. Twenty hours a ...more
WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs ...more
Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' k ...more
GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it i ...more
Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The ...more
Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking. Luckily for those o ...more
Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and lon ...more
The Google Chrome browser for Android is packed with many great features, but it definitely has a bad rep for being slow and laggy on low-end or midrange devices. Without a top-notch processor, you'll likely notice some stutter with choppy scrolling, and pages can take too lon ...more
After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking t ...more
With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials. Git is currently the most widely used version control system (VCS) in the world, ...more
The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe. When you're connected to a Wi-Fi network, internet speeds are general ...more
Thanks to Project-Infrared, there's now a pretty straightforward way to add motion tracking to the HoloLens: Connect it to a Kinect. Wavelength LLC's created a way to get the Microsoft Kinect working as a motion-tracking input device for HoloLens, which my colleague Adam Dach ...more
Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal. The terminal is a key component of any pentester's setup. We're going to be spending a lot of time wo ...more
In the Western world, the only time you'd associate food with cockroaches is health code violations. And while other cultures and countries are more open to cooking with and eating these and other little buggers, insects are probably not a food trend that will be adopted by th ...more
Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking. Just like most other people, we hackers have a lot of credentials to manage. We're also human, so we have a hard time creatin ...more
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use ...more
In case you didn't know, Google has an awesome app that gives you free money to spend on apps, games, movies, books, and virtually anything you can buy on the Google Play Store. The app is called Google Opinion Rewards, and all it asks in exchange for the Play Store credit is ...more
What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap be ...more
Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using ...more
The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff befor ...more
When Google issues an Android update, the changes are usually all over the place—fixing issues, adding functionality, playing catch-up with the latest thing Apple added to iOS. It's how the smartphone wars have evolved, where the two competing operating systems continually mat ...more
Verizon Wireless executives recently cooked up a plan so devious that it could have only come from one of the four major US carriers. Apparently, they aren't satisfied with simply loading every Android device they sell with their own bloatware, so now they're reaching out to b ...more
Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little scre ...more
The international, Exynos-powered Galaxy S7 and S7 edge have had a working root method ever since a few days after release. But the North American variants—those using Qualcomm's Snapdragon 820 processor—have locked bootloaders, and have proven to be almost unrootable up until ...more
Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies. Through partnerships with other hardware manufacturers, Microsoft is hopi ...more
If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff ...more
While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows. Blue Coat is notor ...more
Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage. You can check out the work-in-progress app in action in the video below. It was created by iOS/Android app developer Eric Chee, who has the source code for PieMess ...more
These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time insta ...more
With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile bankin ...more
Greetings my fellow aspiring hackers, Its been a long time and I have to confess I would not be around for long as I am not free yet. I just have some few hours to spare and decided to help out. I learnt OccupyTheWeb won't be around to help out anymore which is like a slap in ...more
The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being ma ...more
Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of ...more
Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about. Sometimes, if yo ...more
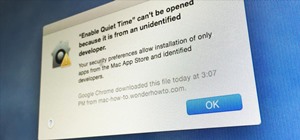
Whether you want to edit photos, compress files, play games, or DJ your next party, there's a free Mac app that can help you out. But things can get annoying real fast if you download a lot of free apps from the Mac App Store, since you have to type in your Apple ID password e ...more
The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You: Google are stacked with money for decades, and even with that at their disposal, that wasn't enough. They thought hey, even though we have products being sold world ...more
Encryption is on everyone's mind these days, from the FBI's battles in court with Apple to WhatsApp's recent announcement of end-to-end encryption for their one billion users. Now you can add Signal, whistleblower Edward Snowden's favorite messaging app, back to that whirlwind ...more
This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document: Step 1: Creating the Payload For this tutorial, I'll be using a pyth ...more
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a ...more
Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics. But ...more
Google has added some fun Easter eggs to Hangouts that'll give you a few more ways to procrastinate throughout your day. All of them (except for one) work on the web browser version, the Chrome app, and the mobile apps for Android and iOS, and are activated by sending a specif ...more
When to throw meat away is a common question, and one I often ask when faced with meat sitting in the fridge after a few days. With vegetables, you can usually tell on sight (or with this guide) when they're past due, but meat is not as simple. As long as meat is refrigerated ...more
Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us. If we are running a Linux distribution with a GUI (graphical user interface) like Kali or Ubu ...more
Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of at ...more
Knowing if your meat is cooked properly is both the difference between a delicious meal and an inedible one... and the difference between making your guests sick and keeping them safe. Yes, you can use a thermometer—but not everyone has a reliable gauge, and sometimes you may ...more
This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7. User Account Control (UAC) Processes in Windows run at different levels of integrity, representing the different amounts of "trust" they have to interact with the com ...more
SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. Tha ...more
Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow. Scenario Let's say, that we have done all the recon(both passive and active) and we have scanned the web serve ...more
In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenari ...more
Microsoft is working hard to make Bing a good alternative to Google for more than just looking up images of the "human anatomy" that Google and a lot of other search engines filter out of their results. The Bing App home screen has five buttons that let you start searching qui ...more
T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On ...more
Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this info ...more
Spaghetti squash is a versatile vegetable, but it has a reputation for being intimidating to prepare... not to mention time-consuming. Heating it up in the oven can take at least 30-40 minutes, which is a definite time-suck for those who want to get dinner on the table, stat. ...more
Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or datab ...more
If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart. When you run programs an ...more
Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the prev ...more