Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things. Some Benefits of URL Shorteners We can create ...more
Google+ is the most exciting new social network to come around this decade, and the only product with a chance of challenging the monopolies we know as Facebook and Twitter. As an Internet addict, I've joined every major social network there is - from Friendster (who?) to MySp ...more
INTRODUCTION If you are a part-time blogger and owns a blog which is hosted on blogger, then the first thing which you could want to do is to convert your blog layout to a professional looking website. You can either edit the XML file yourself or you could choose to use a tem ...more
Do you want to be that cool person on the web? Heh. Actually, did you just want to try spicing up your embedded YouTube videos? Try it in HD, or have it in autoplay or different sizes! With this code, you will be able to play music, or display your latest vlog as soon as you g ...more
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES... USE EASEUS DATA RECOVERY WIZARD V5+... USE FROSTWIRE P2P FILE SHARING CLIENT... USE INCREDIMAIL 2 (LATEST)... USE SAFARI (ONE OF THE ...more
Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying vario ...more
You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down th ...more
There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikiped ...more
Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like? Not great? Do you think it coul ...more
Last week I had a quick look at V.I.K.T.O.R, the anthropomorphized automated editing app that lives on your iPhone, and today it’s time to put it to work. There’s a powerful idea at the center of V.I.K.T.O.R. Our mobile devices make it absurdly easy to shoot high quality vide ...more
Now that Google+ is open to everyone, there are a lot of new people who aren't techies trying out the service. When you first sign on, it can be overwhelming. I've decided to round up a bunch of resources to help you get started, and recommend some people for you to follow, if ...more
The days of having to pay for video games are over. Generally, retail games are better because they're made with more effort and care than their free counterparts. But free browser-based game sites are insanely popular, specifically Kongregate, Armor Games, and the grandaddy o ...more
Real-time strategy (RTS) was the most popular genre in PC games at one time. It put Blizzard on the map—one of the biggest game developers in the world. And it buried the once venerable turn-based strategy genre, the only survivor being the Civilization series. But like hair m ...more
noob - Short for "newbie." Someone with little to no experience or skill. In some gaming communities, there is fierce debate over the distinction between "noob" and "newb"—one being derogatory while the other simply indicates being a novice. While some may argue the semantic d ...more
It's really a shame that it is so hard for people to make money on the internet these days. The dot com bubble has receded and scams are plentiful on the web. There are, however, a couple of legitimate ways to make a few extra bucks online, Amazon Mechanical Turk, or MTurk for ...more
ClariTrans is a requester on MTurk (www.mturk.com) they pay very well for transcribing short snippets of audio. Here is how you can transcribe their audio snippets properly to ensure your text will be approved and you will be paid: ClariTrans Transcription Formatting Guide S ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
One of the things I consistently notice amongst fellow internet users is that many people don't know how to properly search for stuff. Google may have served you well in the past, but I'm going to share a few little tricks with you to help make your search results even spiffie ...more
With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these al ...more
SCRABBLE. I miss it. That idiosyncratic smell of cardboard, cheap wood and plastic that rushes out when I remove the box's cover. The instant gratification of unfolding the board into the sweet spot of the table, smoothing it out into the perfect receptacle for a heated battl ...more
Time to confess a personal bias: I love Gmail. I think it's the best thing since sliced bread. I try to be impartial when I write about software and online services, but seriously -- of all the free email services out there, why would you use anything else? A quick point of o ...more
Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared E ...more
This method works for anything except sidekicks. First open your browser then in the address bar go to MYXERTONES. Look through the site and choose a ring tone that you think you might like. Click the song and upload it, then type in your phone number, or edit the song to just ...more
Downloading pictures from Orkut, Google's social networking site, is simple and can be accomplished in five steps. First, log into Orkut. Second, open the image you want to save. Third, drag the image to your web browsers address bar. Fourth, right click and select Save Pictur ...more
There's a cool little plugin for your WordPress blog that will help you get more traffic from people searching the web on mobile devices. It's called MobilePress. Your visibility will become greater on mobile phones and other mobile devices when activating this plugin on your ...more
The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your iden ...more
The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week. The premise should be familiar to anyone who has followed augmented reality over the past year, and likely old hat to those who t ...more
Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, Stand ...more
Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin ...more
The Internet has had a huge influence on many areas of our lives, but, in particular, has resulted in nothing short of a revolution in the way we work. The web has offered the sort of flexibility to the individual that few people would have dreamed of just a couple of decades ...more
Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them ...more
Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective. In addition, by knowing what files ...more
The next big event Apple is holding is WWDC 2018, its Worldwide Developers Conference, is about to happen. If you want to see the first glimpse of iOS 12 for yourself, as well ARKit improvements, Apple Watch news, and maybe even some macOS announcements, here's how you can tun ...more
Progressive Web Apps hope to one day bridge the gap between websites and apps by giving the former more access to your phone's features, but they're not very common yet. In the meantime, you can take matters into your own hands with an app that uses your system WebView to rend ...more
There are many reasons you might want to increase your text size in Google Chrome. The browser's accessibility options have a few tools to help the readability of text on websites. Changing the text scale, enabling zooming, and toggling the simplified view can customize Google ...more
Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are ...more
Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore. Google announced the release of the WebXR Device API last month for VR experiences in Chrome version 67. Now, Google has made the WebXR Hit Test A ...more
Immersive advertising company Vertebrae has extended its native ad platform to augmented reality via mobile Chrome browsers for Android and Safari for iPhone. Originally built for virtual reality, the platform provides advertisers with six templates. For the front-facing came ...more
As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache h ...more
When we surf the web, we tend to do it for selfish reasons. Whether it's on Facebook, Twitter, YouTube, Pinterest, or Wikipedia—we're trying to connect with people, voice our opinions, watch funny videos, or do research for that 12-page paper due tomorrow. Whatever it is, it's ...more
Augmented reality's status as a new storytelling medium has already led to the reinvention of filmmaking and journalism. Now, AR is helping non-profits draw attention to their respective causes. Don't Miss: USA Today Deepens Story on Afghanistan War with AR Experience On Mo ...more
Mobile augmented reality developer Blippar has escalated the augmented reality advertising arms race, introducing a new rich media ad format that enables augmented reality experiences without a dedicated app. Augmented Reality Digital Placement (ARDP) delivers content to smar ...more
In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need Apache web server with PHP An image (included bellow) An email Account (I use gmail) Step 1: Setting Up Make a folder called "image.jpg" in your ...more
Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, ...more
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity! Social Eng ...more
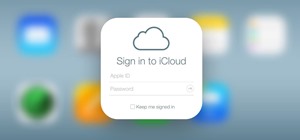
Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for expl ...more
Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA d ...more
Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side sy ...more
Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform. However, one of those essential features, shar ...more
Koushik Dutta, the developer behind the Android app AllCast, has made the leap over to the realm of personal computers with his latest offering. AllCast Receiver for the Chrome browser, much like its Android counterpart that turns older devices into media servers, allows you ...more
To celebrate YouTube's 17th birthday, Google has gifted the app with new features, including pinch to zoom, precise seeking, and a darker dark theme. But the highlight is a new cosmetic upgrade called Ambient mode, which makes the viewing experience more immersive. Here's ever ...more
During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform O ...more
Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, con ...more
Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimat ...more
If you ever looked at Apple's Peek and Pop feature on Safari and said "I want that," Google has kinda-sorta delivered. A new hidden Chrome feature brings similar functionality to Android despite the lack of 3D Touch, and while it's a bit redundant and nowhere near as polished, ...more
One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines conn ...more
Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to prote ...more
While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes ...more
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used. If you've ever gone over your allotted mobile data limit, you know firsthand how costly your carrier's overage fees can truly be. From that poin ...more
If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible. A few months ago, Dallas covered six ways to speed ...more