How To: Customize and Use Control Center on Your iPhone for Quick Access to Your Most-Used Apps, Features, and Settings
If you're not using Control Center on your iPhone, you're missing out on a powerful tool that can streamline how you interact with your device, make certain tasks more efficient, and give you quick access to system tools, switches, and sliders for quick changes no matter where you are or what app you're in.

How To: 10 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
The app getting the most significant update on iOS 17.5 is, by far, Apple News. While there are a few changes in Books and Settings, as well as minor changes in apps like Podcasts, Apple News has at least 10 new features and changes you should know, some of which are worth getting excited about.
How To: Apple's Integrating Game Center Leaderboards into News+ Puzzles with iOS 17.5
Your iPhone is going to get a few significant improvements with the iOS 17.5 software update, but my favorite is Apple's enhancements to the Apple News app, which is making its Puzzles section even more fun with Game Center integration and even a new type of word puzzle.
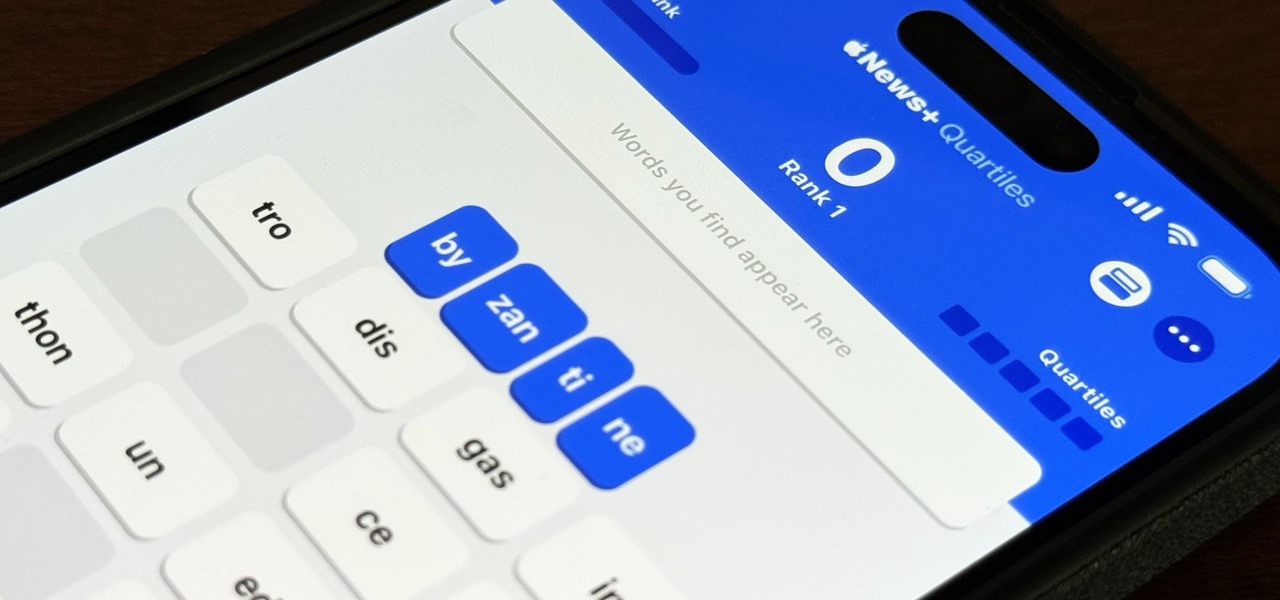
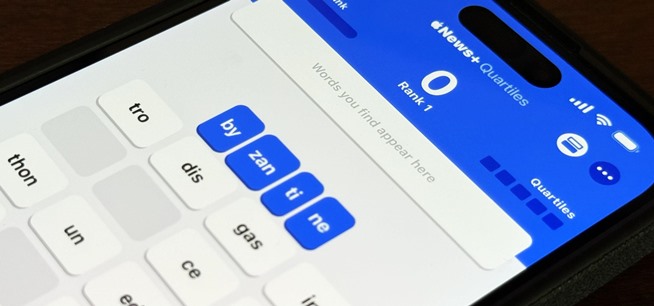
How To: Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
Apple's next software update, iOS 17.5, is relatively minor. Still, it includes one killer new feature for people who like word games: another lexical challenge to complement the crossword puzzles that Apple News already has.

How To: Identify Any Song Playing on Instagram, TikTok, and Other Apps on Your iPhone Using Shazam
Since Shazam became available on iPhone, it's been easier than ever to identify a song playing somewhere in the background. You could hear something you like while watching a movie or sitting in a coffee shop, and all you have to do is open the Shazam app and have it listen for you. But what about music playing on your iPhone via Instagram, TikTok, and other social media apps?
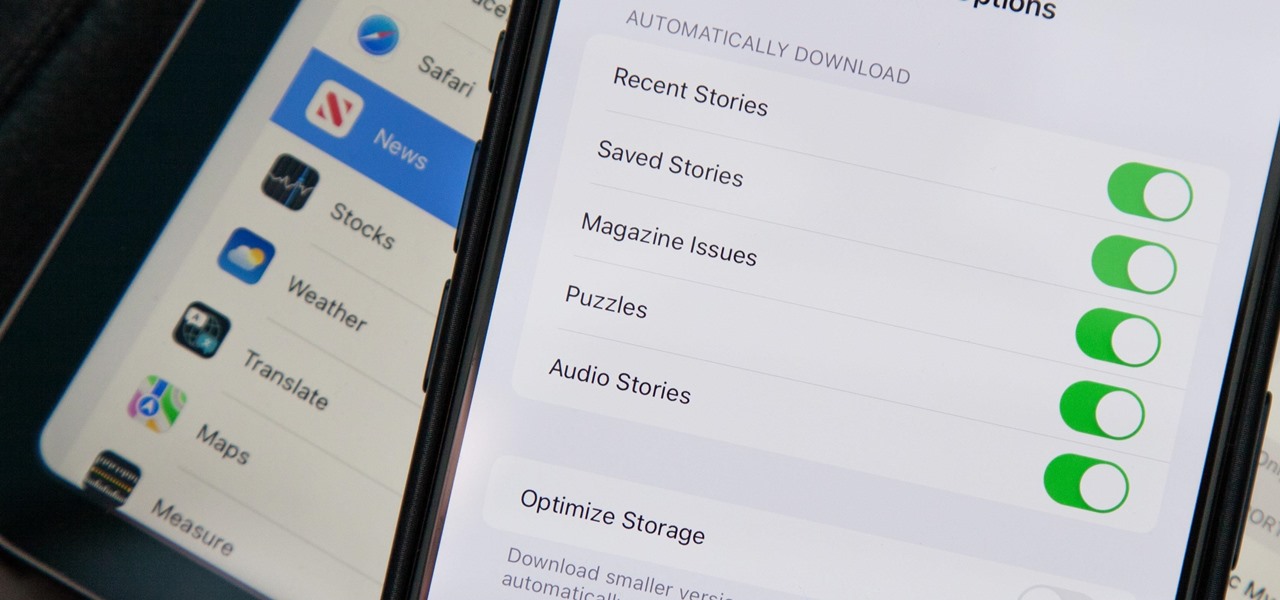
How To: Apple News Gives You More Options for Automatic Downloads on iOS 17.5
In the upcoming iOS 17.5 software update, there are new features for EU countries and mobile device managers only, but there are also more widespread user-facing changes to Books, Podcasts, and other apps. News is one of those other apps, and it's giving us more preferences for automatic downloads.
Top Trending Posts
How To: 25 New Features and Changes Coming to Your iPhone with iOS 17.5
Apple released iOS 17.4 on March 5 with over 30 new features, but now it's iOS 17.5's turn for the spotlight. The update, currently in beta, gives us a few interesting updates and changes for iPhone, including a new word game, and there's even a sneak peek at what could be coming in the stable build.
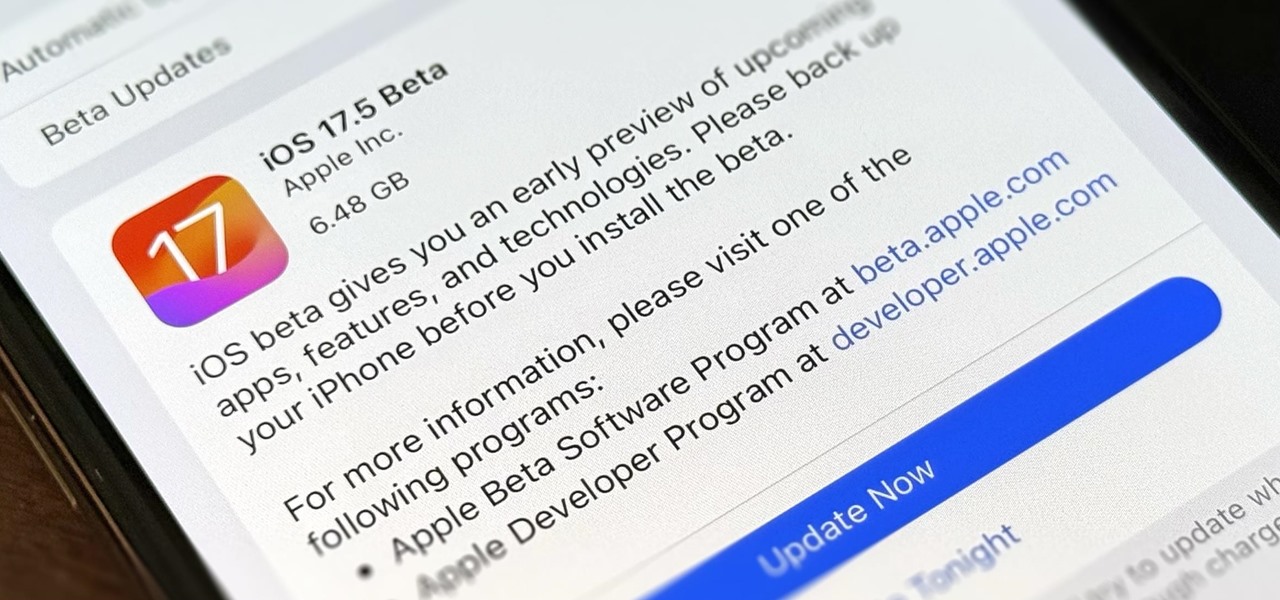
How To: Download and Install iOS 17.5 Beta on Your iPhone — And Try New Features Before Everyone Else
Apple is still not finished with iOS 17. We're just a few months away from its developer conference, where iOS 18 will be revealed, but there are still things to be fine-tuned on your iPhone until then. This brings us to iOS 17.5 — now available to try on your iPhone.
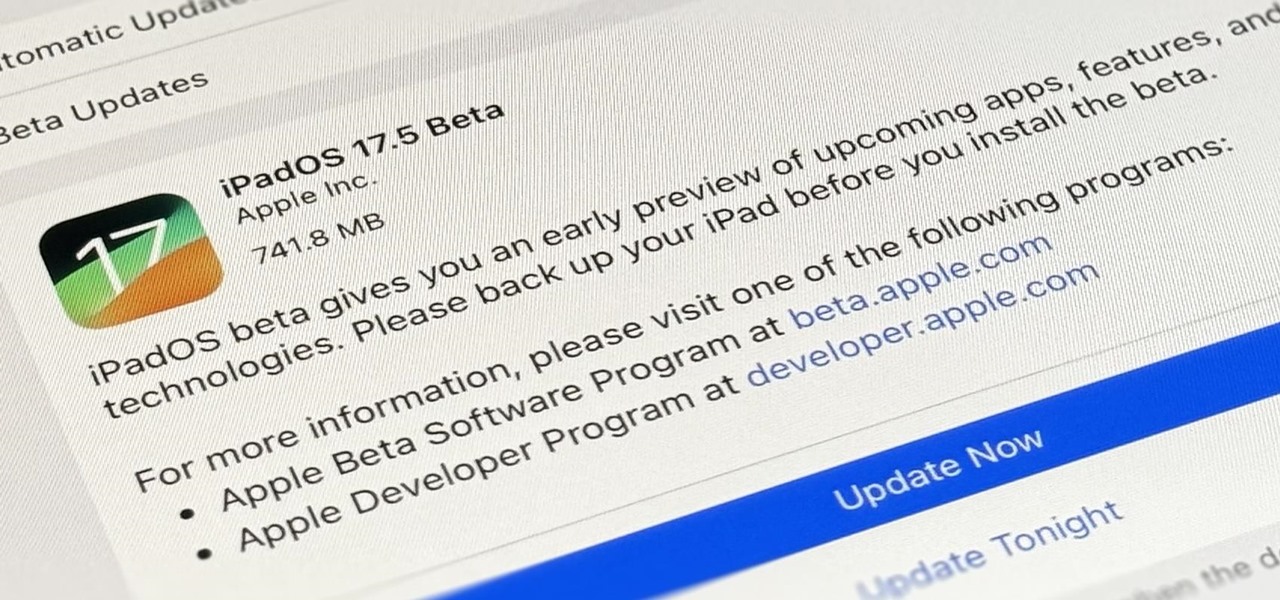
How To: Download and Install iPadOS 17.5 Beta on Your iPhone to Explore New Features Before Everyone Else
Apple's developer conference, where iPadOS 18 will be revealed, is just around the corner. But before we get there, there's still work to be done on iPadOS 17. That brings us to iPadOS 17.5 — and you can test drive it on your iPad right now before the masses.

How To: Update Your iPhone's Lock Screen with an Attention-Grabbing Note, Reminder, Warning, or Other Custom Message
There's a lot you can customize on your iPhone's Lock Screen — wallpapers and photos, widgets, the display mode, notifications, and even the time's font and color. But there's another feature that lets you add custom text for whatever you want, whether it's an inspiring quote, a reminder, a warning to anyone who dares touch your iPhone, or even just your name.
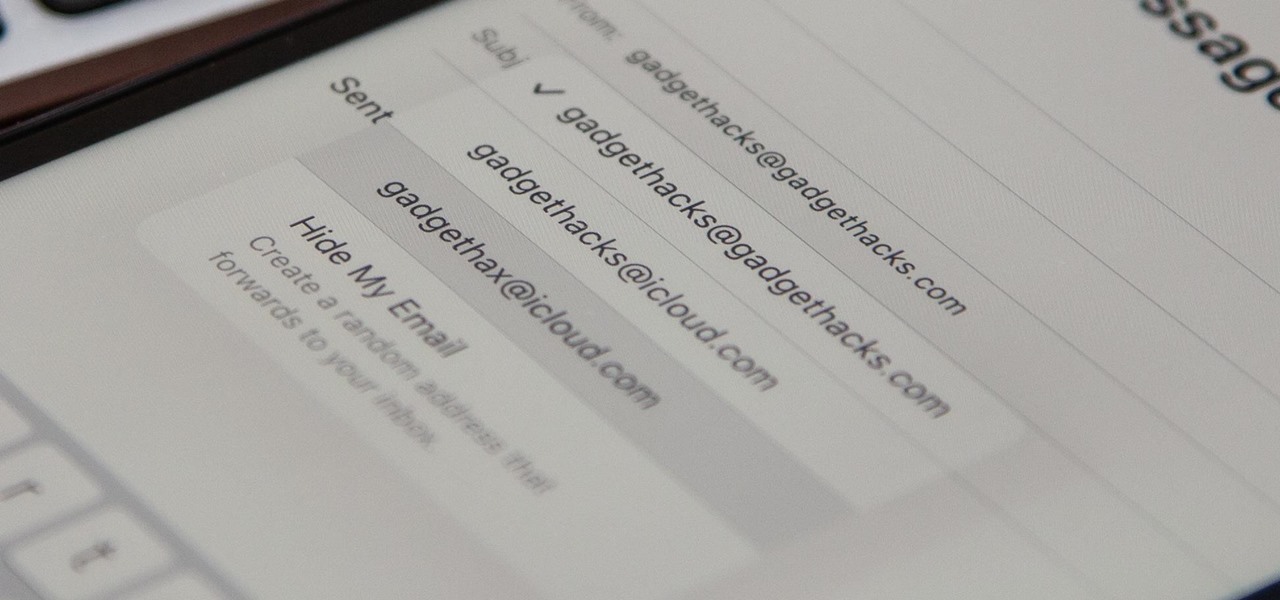
How To: Your iCloud Email Lets You Create Aliases to Protect Your Primary Email Address and Organize Your Inbox
On your iCloud Mail account, you can easily use subaddressing to create hundreds of new iCloud email addresses to give to companies and other parties, all of which go straight to your primary iCloud email address's inbox. The problem with these types of alternative email addresses is that you can't ever respond to emails with the plus tag intact. But Apple has another alternative for you to start using.
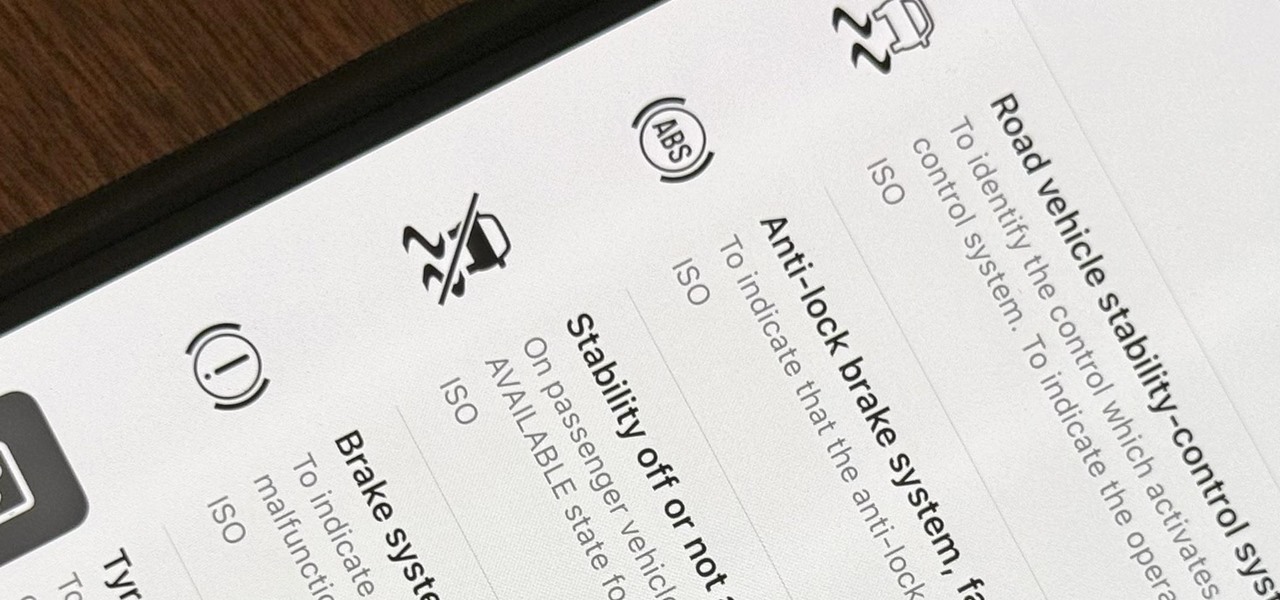
How To: Use Your iPhone's Built-in Image Analyzer to Reveal the Hidden Meaning Behind Symbols, Signs, and More
When you encounter a mysterious laundry care symbol or alarming vehicle indicator light, you might just ignore it rather than ask somebody, search online, or open a user manual for the answer. If you have an iPhone, there's an easier way to decipher the meanings behind perplexing symbols and signs—and it only takes a few seconds.
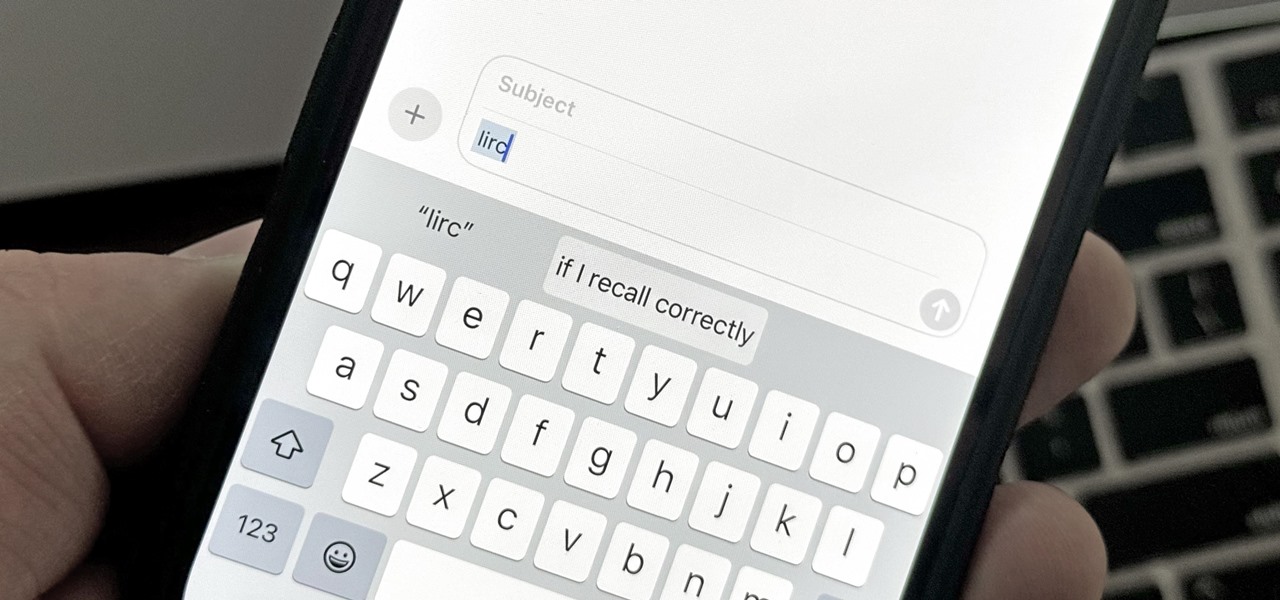
How To: Unlock Your iPhone, iPad, or Mac's Hidden Text Replacement Feature for More Efficient Typing
There are plenty of tools that'll help you type faster and more efficiently on your iPhone or iPad, such as Slide to Type, Dictation, and even a case with a physical keyboard. But one of the best tricks will help you type frequently used words, phrases, sentences, email addresses, and more faster, and you can sync your settings with your Mac so you can type more with less effort on all your Apple devices.
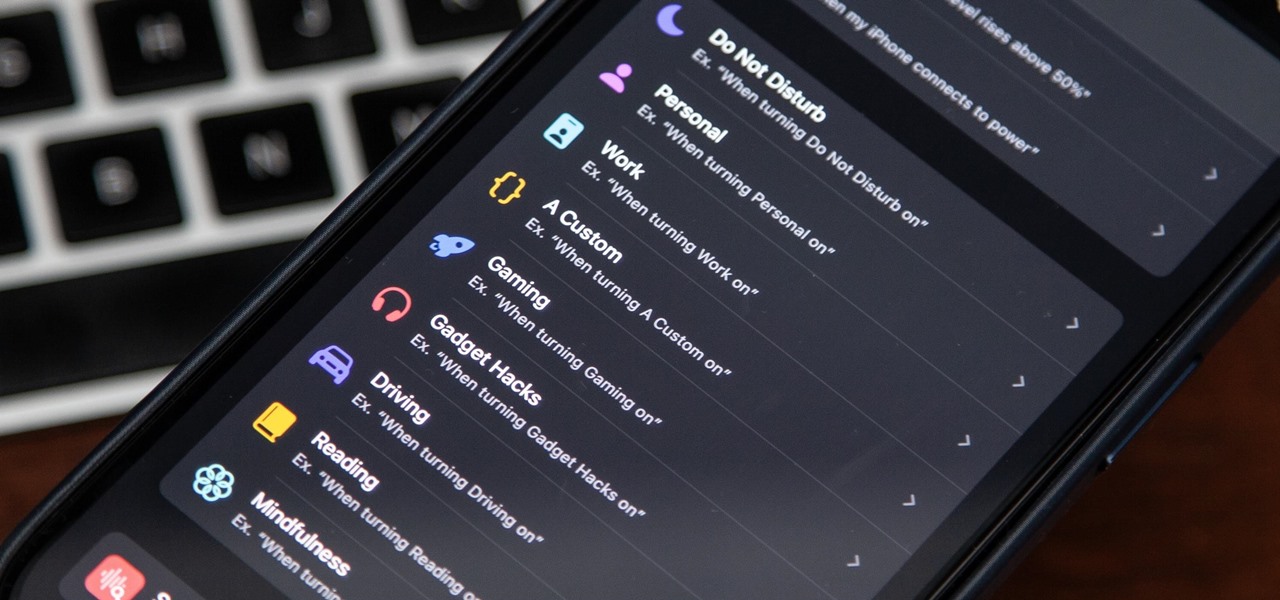
How To: Focus Profiles Will Change How You Use Your iPhone — Here's How to Set Them Up for Distraction-Free Experiences
There's a powerful tool on your iPhone that can fine-tune your iOS experience based on what you're doing and when, and it's completely customizable. With it, you can control what notifications appear or are silenced, who can call you, which Home Screen pages you want to view, the Lock Screens you can pick from, and more. And you can automate it based on a variety of triggers.
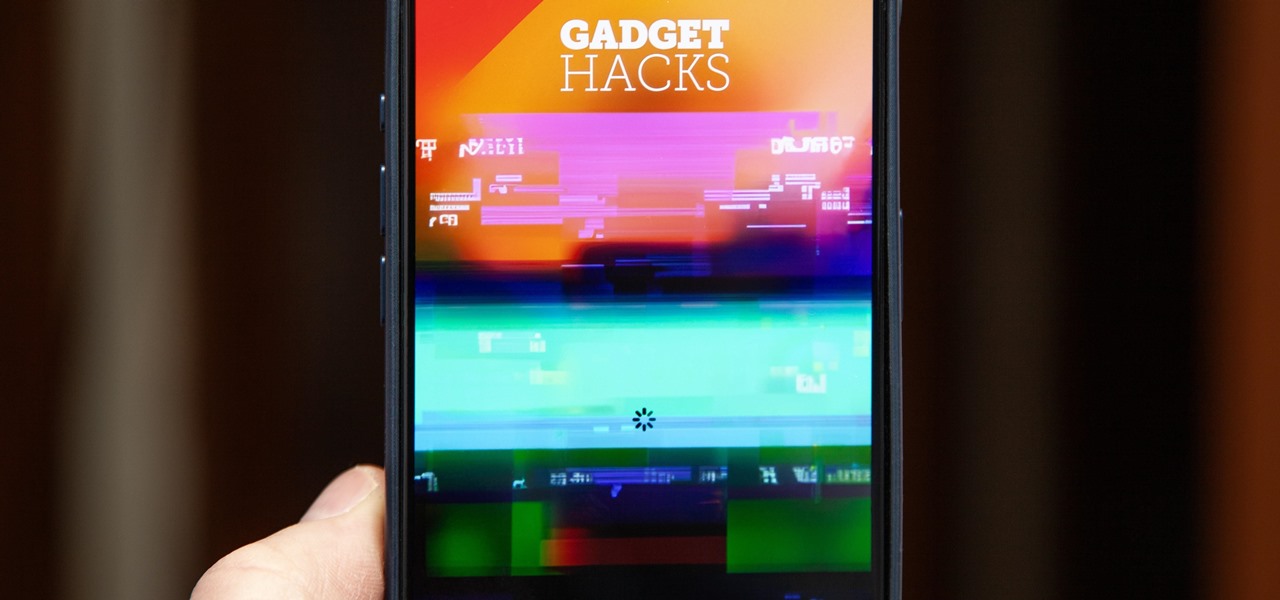
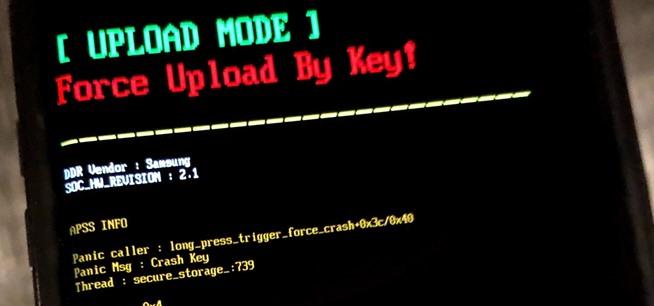
How To: Force Restart an iPhone 15, 15 Plus, 15 Pro, or 15 Pro Max When It's Frozen, Glitchy, or Won't Turn On
The iPhone 15, iPhone 15 Plus, iPhone 15 Pro, and iPhone 15 Pro Max are Apple's most powerful iPhones to date with features like USB-C connectivity, improved camera capabilities, and faster CPUs. But no matter how impressive these phones are, they can still freeze, become unresponsive, or get stuck when powering on — and a force restart is how you get things working again.
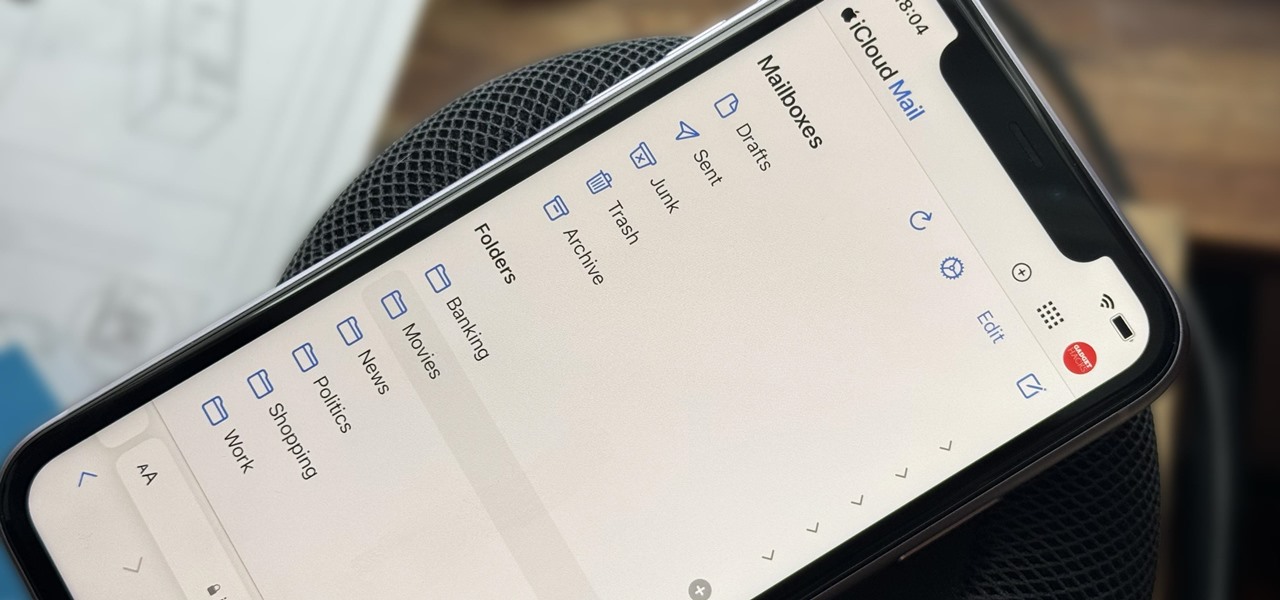
How To: Create Unlimited iCloud Email Address Variations to Take Total Control Over Your iCloud Mail Inbox
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro.

How To: Use Your iPhone to Hear the World Around You Better, Spy on Conversations, Listen to Your Heartbeat, and More
What started as an accessibility setting for hearing aids turned out to be a super helpful tool for anyone with a good set of Bluetooth headphones. The problem is that most iPhone and iPad users still don't know about it. If you're one of them, you need to see what this underrated gem in iOS and iPadOS can offer you.
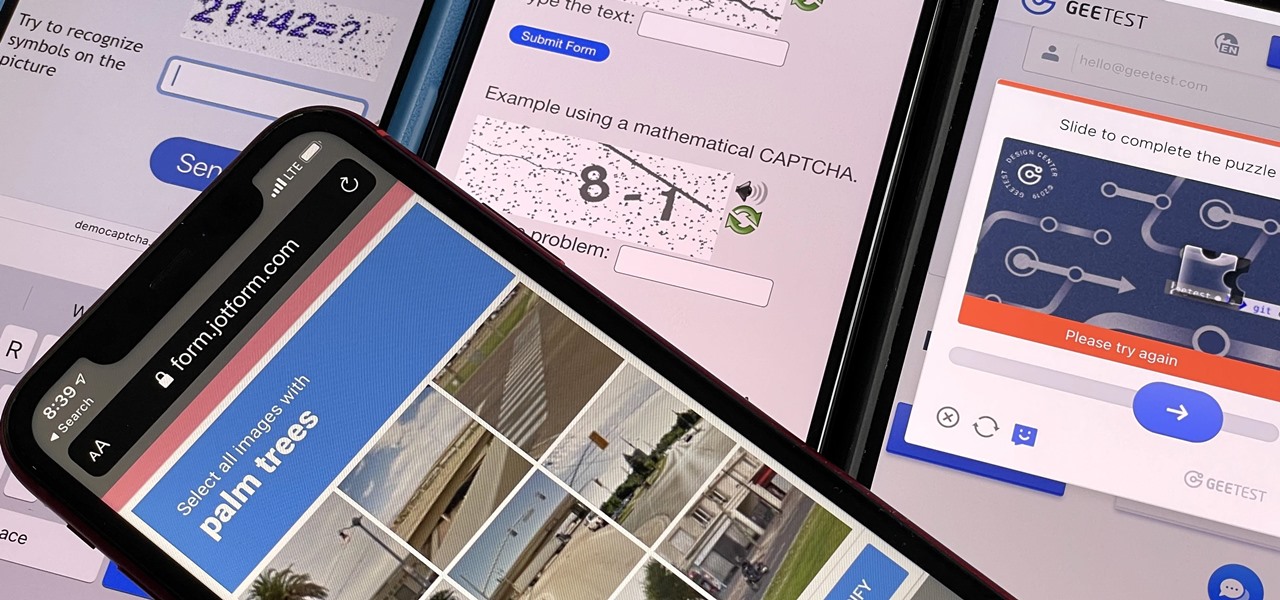
How To: Automatically Bypass Human Verification Prompts on Your iPhone, iPad, or Mac to Experience Fewer CAPTCHAs
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.
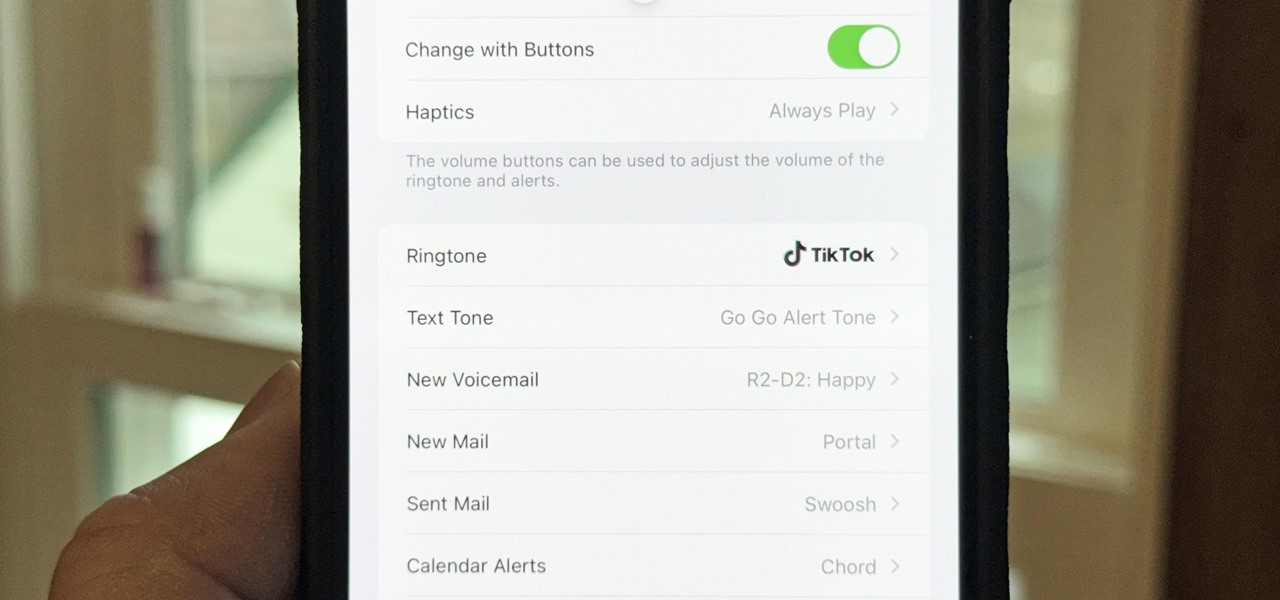
How To: Turn a Viral TikTok Sound Bite or Song into Your iPhone's Next Ringtone
There seems to be no end to all the viral TikTok sound bites and trending TikTok songs, and there's a good reason why they are ingrained in the fabric of our pop culture. TikTok's short audio clips can evoke laughter, tears, and a wide range of other emotions, and many of them just happen to be the perfect length to add to your iPhone's or iPad's arsenal of ringtones.

How To: Make Siri Say Whatever You Want Every Time You Connect Your iPhone to a Charger
Whenever your iPhone's ringer is on, you'll hear Apple's iconic "Connect Power" chime every time you connect it to a wired or wireless power source, which lets you know that charging has started. There's no way to disable the sound without turning on Silent mode, but there is a way to make Siri automatically say whatever you want after a successful connection.

How To: Take Scrolling Screenshots of Entire Webpages, Text Documents, and More on Your iPhone or iPad
When you take a screenshot on your iPhone, it's automatically saved to your Photos app. You can ignore the screenshot thumbnail or swipe it away, but you shouldn't. If you open the screenshot editor instead, you'll gain access to your iPhone's most useful screen capture tool: full-page screenshots.
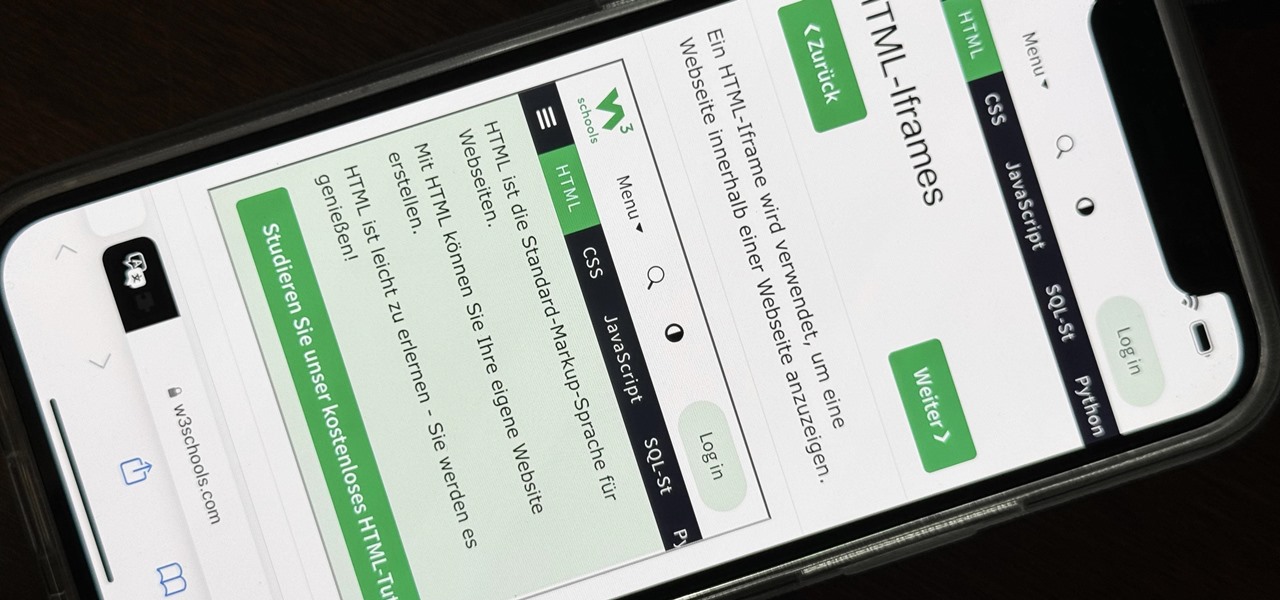
How To: 5 Hidden Features in Safari's 17.4 Update for iPhone and iPad You Didn't Know About
The latest 17.4 update for Safari includes a prompt for EU users to choose a different default web browser available in their region. It also gives us new ways to customize the Favorites Bar on an iPad. And Apple Cash virtual numbers are now supported as an AutoFill suggestion. But there are also some hidden changes in Safari 17.4 for iOS and iPadOS that you might not ever notice unless you keep reading.
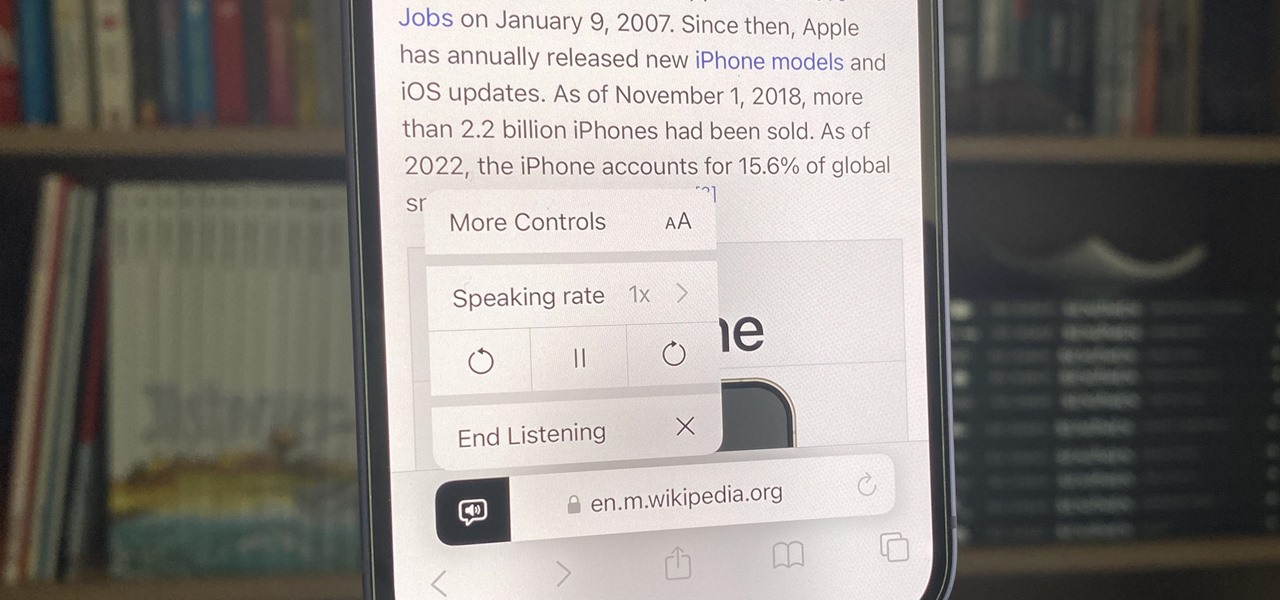
How To: Unlock Your iPhone's Many Hidden Text-to-Speech Features to Make It Read Virtually Any On-Screen Content
Speech-to-text technology can be seen on your iPhone in various places, from the Dictation tool to Apple's new behind-the-scenes, auto-created transcripts for podcast episodes. Your iPhone also has some pretty impressive text-to-speech capabilities. With them, your iPhone can read webpages, documents, or whatever text is on the screen out loud to you — only some of these tools aren't easy to find.
How To: This Hidden Setting Gives Safari's Favorites Bar Better-Looking Shortcuts to Your Most-Used Bookmarks
Apple has a new way to tidy up your favorite bookmarks in Safari, making them easier to access than ever before. This new feature saves space, allowing you to quickly see more of your favorites at the same time.

How To: View Podcast Transcripts on Your iPhone to View, Search, and Navigate the Audio
Apple's Podcasts app just got a big feature: transcripts. Before, you had to rely on third-party services or the off chance that podcast creators posted transcription links to each of their episodes. Now, you can view, read, and search show transcripts directly in Podcasts, whether uploaded from the creators or automatically generated by Apple.

How To: 34 New Features and Changes for Your iPhone on iOS 17.4
The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

How To: Your iPhone Just Got 118 More Emoji — Here Are All the New Characters and Variations
There are now more emoji on your iPhone's keyboard that you can send as reactions or stickers or insert wherever else you use emoji — and it's about time. It's been nearly a year since the last emoji update for iOS, and we only received support for 31 new ones then. The new iOS 17 software update brings almost four times as many.
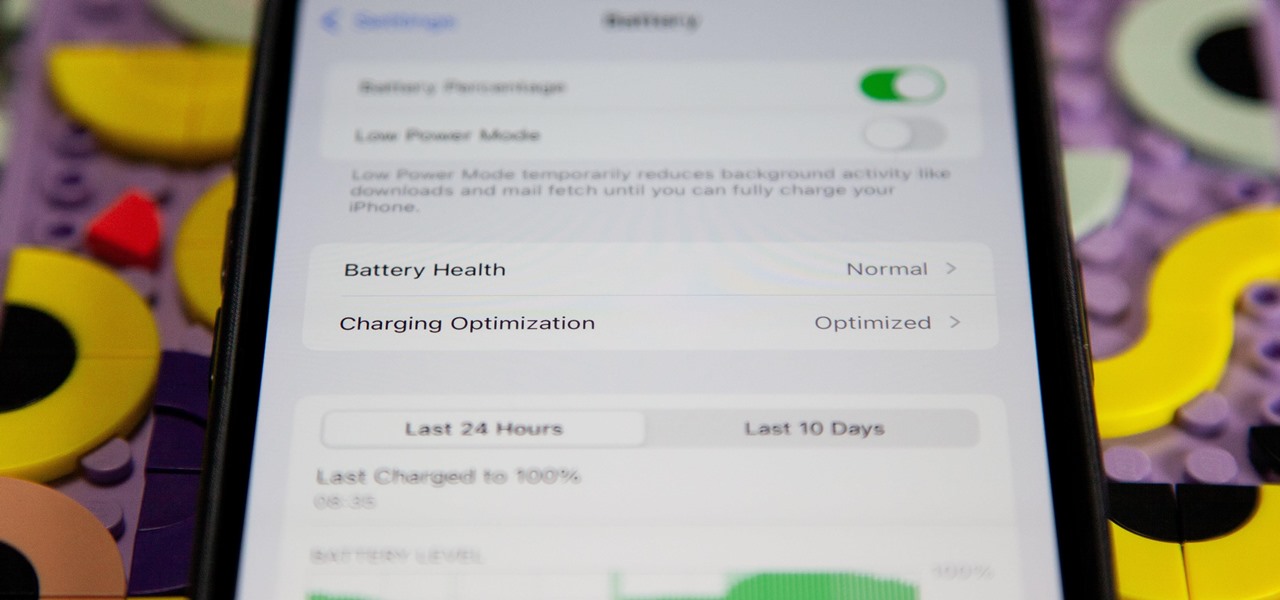
How To: Apple Just Gave Your iPhone 15 or 15 Pro Better Battery Health Stats
If you're ever curious about your iPhone's battery health, there are easy-to-access stats that let you know the last charge amount, which apps are eating away at most of your power, and even your battery's remaining capacity. Now, a new update makes it easier to know how well your battery is doing.

How To: Set Up a Virtual Card Number for Apple Cash on Your iPhone to Use Where Apple Pay Isn't Accepted
For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.
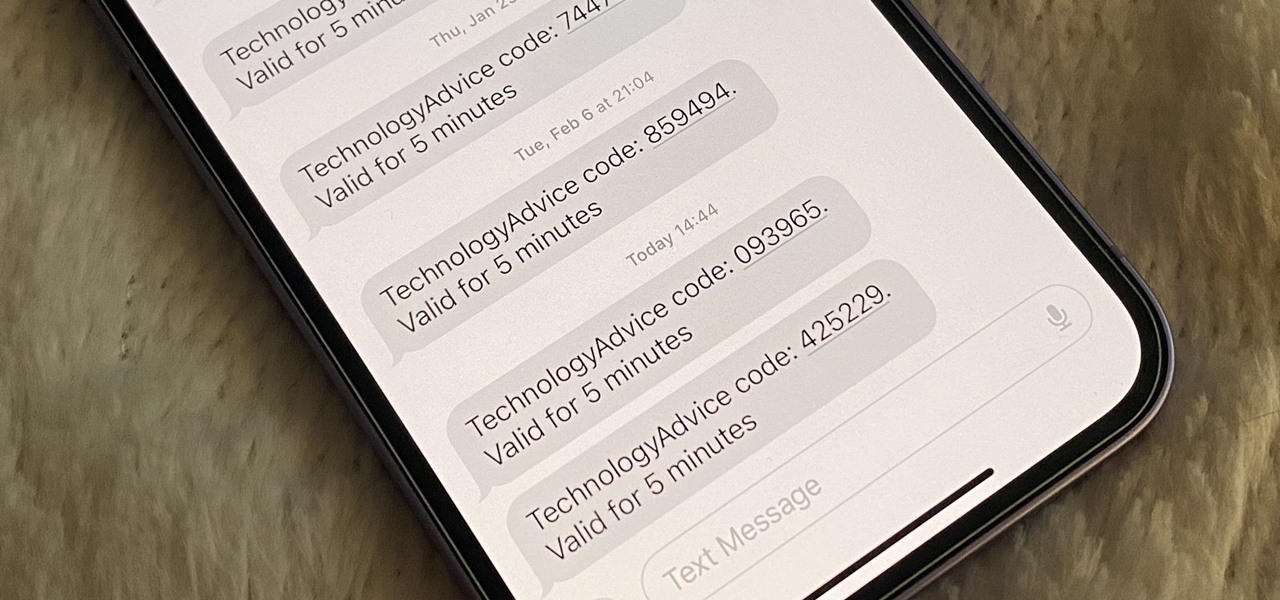
How To: Your iPhone Can Help Keep Clutter from Piling Up in Mail and Messages — Here's How
Many of your accounts online likely require two-factor authentication (2FA) or two-step verification (2SV) to confirm your identity when logging in, and there's a good chance the second factor or step for each is a one-time email or SMS verification code. If you get a lot of email and SMS codes, it can clutter your Mail and Messages apps with junk if you don't delete the messages after signing in.

How To: Unlock Safari's Secret Dual-Search Engine Experience to Optimize Your Web Browsing
If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

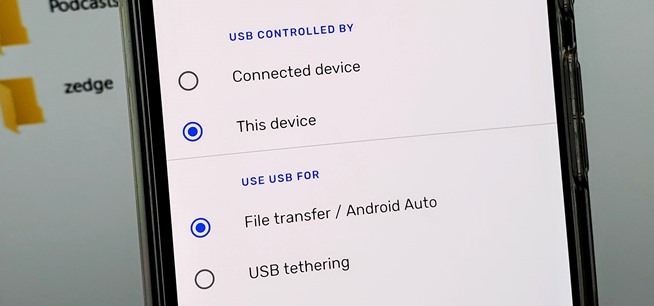
How To: Best External USB-C Storage Options for iPhone and iPad
If you bought an iPhone or iPad equipped with USB-C but didn't max out the local storage, there are some great external storage solutions beyond iCloud and other cloud storage services. And now that the iPhone lineup comes with USB-C ports, you have better-performing external drives available to you than anything you could ever get for a Lightning-based model.
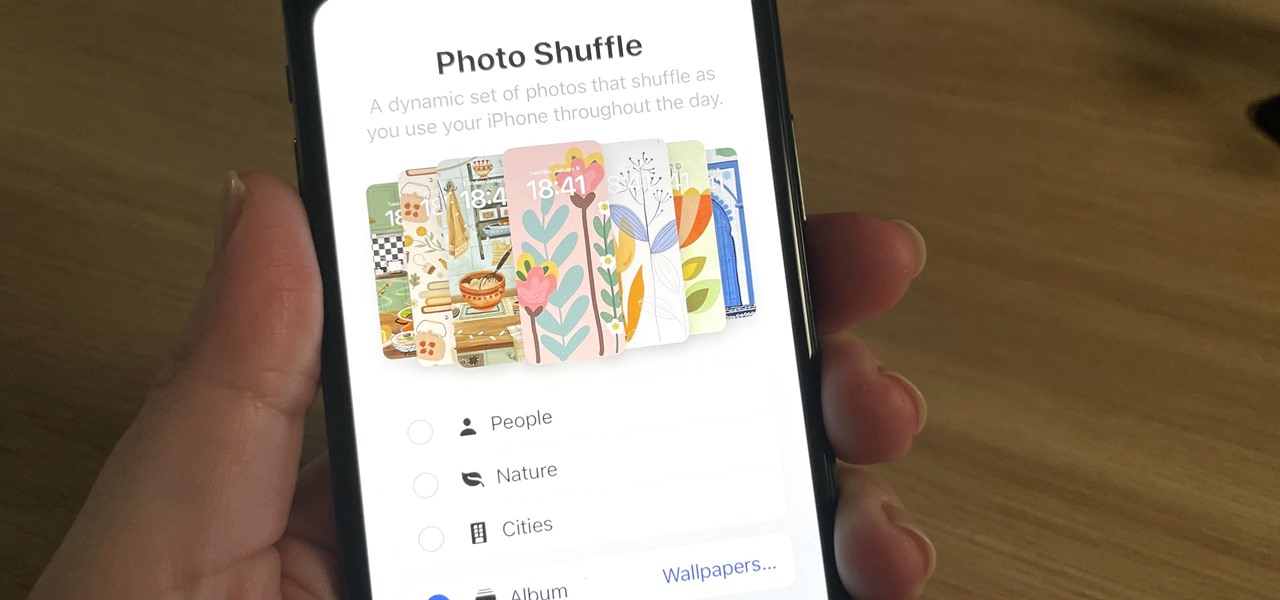
How To: Rotate Wallpapers on Your iPhone to Photo Shuffle All Your Favorite Pics by Tap, Lock, Hour, or Day
Your iPhone has plenty of already-created Apple wallpapers just waiting for you to set as your Lock Screen and Home Screen backgrounds. But using a photo from your own library can provide a more emotional connection, help you express yourself better, and give your phone a more unique look. To maximize these effects, auto-rotate your personal images daily, hourly, when locked, or when tapped.

How To: Turn Your iPhone into a Samsung Galaxy S24 or Z Fold 5
Are you thinking of switching from an iPhone to an Android phone? Before you make a permanent change from Apple to the other side, it's good to try out the other ecosystem and see if it makes sense for you. If you can't get your hands on an Android phone to try it out, you can simulate Android right on your iPhone. You can even see what a foldable smartphone feels like!
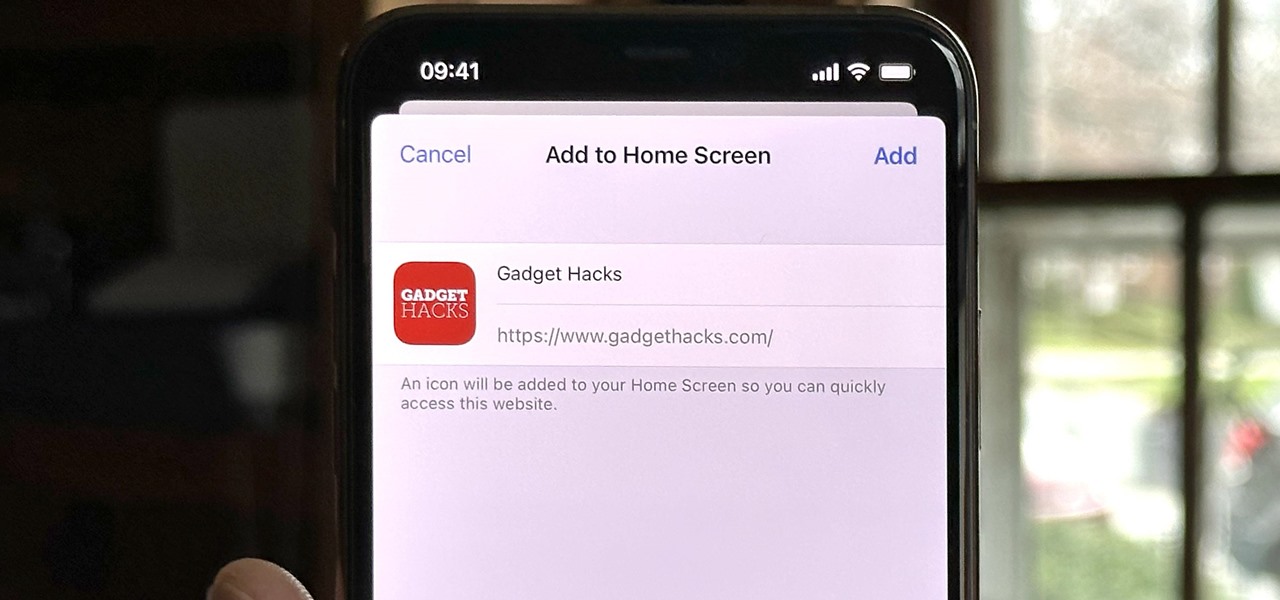
How To: iPhone Browsers That Support 'Add to Home Screen' for Web Apps and Bookmarks
Safari isn't the only web browser on your iPhone or iPad that will let you add icons to your Home Screen for progressive web apps and website bookmarks. Apple gave developers the key to its "Add to Home Screen" feature, and your favorite iOS or iPadOS web browser may already support it.
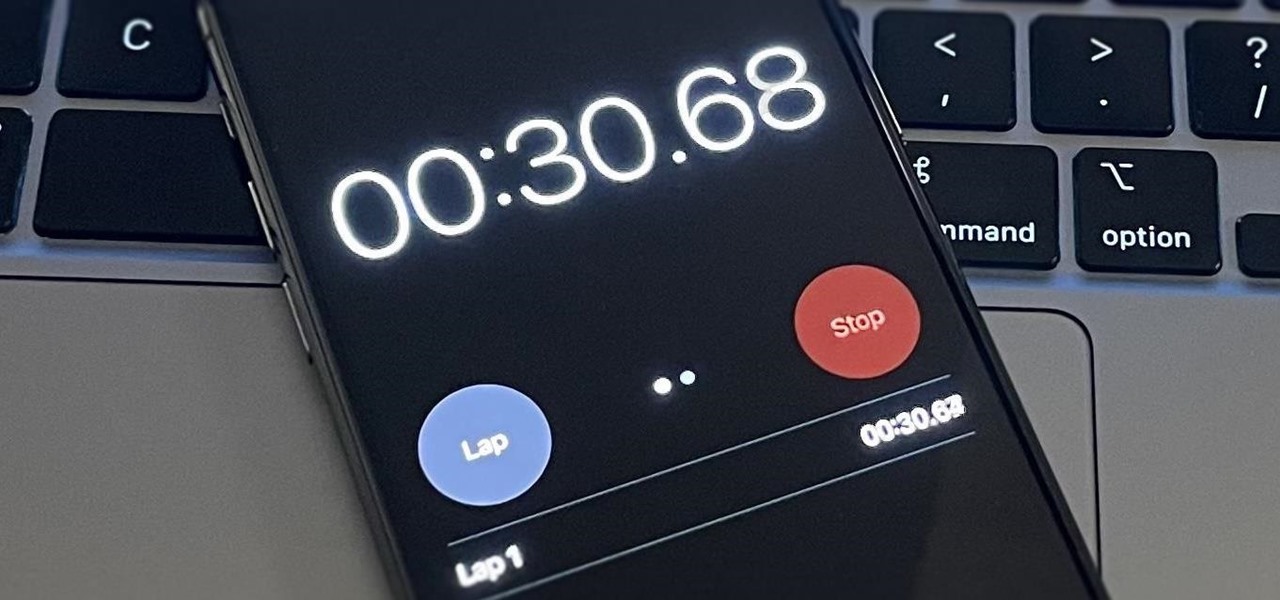
How To: Your iPhone's Clock App Is Getting a Big New Feature in a Future iOS Update
When iOS 17 first came out, the iPhone's Clock app received a giant new feature, one that lets you set multiple timers and keep track of them on the Lock Screen, in the Notification Center, and in the Dynamic Island. A future iOS 17 software update may give us something just as exciting for the stopwatch.

How To: Hear Conversations During Calls Much Clearer with These Hidden iPhone Features
Whether it's everybody or just a specific contact you can't hear during audio and video calls when wearing headphones, your iPhone has hidden, little-known tools to help you catch every word they say in the conversation. Even if you can normally hear everyone during calls, customizing these headphone preferences can make conversations crystal clear.

How To: Get the Time Without Looking Using Apple Watch's Hidden Time-Telling Features
Our everyday lives are inundated with displays from smartphones, computers, tablets, TVs, and other devices, so it's important to find ways to limit your screen use wherever possible to improve your overall digital well-being. One simple thing you can do if you have an Apple Watch is make your watch tell you the time so you don't have to look yourself — and this little-known feature is easy to unlock.

How To: The Best Smartphones to Buy in 2024
If you're in the market for a new smartphone and want nothing but the best of the best, now's the time to act. Some of the greatest phones money can buy are being released as we speak, while others are still in their prime and will continue to be for most of 2024. Whether you want an iPhone or Android, we've rounded up the best picks you have to choose from for top-of-the-line specs and advanced features.
How To: 12 New iOS 17.3 Features for iPhone You Need to Know About
Apple last month released iOS 17.2, its biggest iPhone software update since iOS 17.0, with 60 new features. Now, as of Jan. 22, we have iOS 17.3. Overall, it's not the behemoth software update that iOS 17.2 was, but it has a few exciting new things you'll definitely want to know about.