The herpes simplex virus (HSV) can cause devastating complications for infected newborns whose mothers have genital herpes. Understanding risk and research can help you, and your baby, when the time comes. In the US, about one out of six people aged 14 to 49 have genital herp ...more
A long time ago I was reading an issue of Saveur and saw an article about a trendsetting bar in Portland. The bartender at the joint had started making enormous blocks of smoked ice for his cocktails. When a patron ordered a drink that called for the smoked ice, the bartender ...more
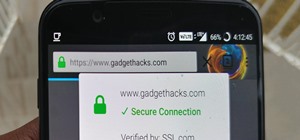
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! As much as I love other SSH bruteforcing tools like Ncrack, Metasploit, THC-Hydra, ... ( Just to mention a few ). I prefer using my own script. The tools ab ...more
Creating a haunted house for Halloween was a big deal when I was growing up, and the neighborhood kids were always coming up with ways to try and out-do each other when it came to this frightful night. One beloved game was to blindfold the participants and play the Withered Co ...more
While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.) Some of these secret tricks take advantage of function ...more
The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack usi ...more
This video shows us how to make a shawl when knitting on a large knitting loom. Here are the following steps: Step 1. First of all take the knitting ring and wrap the wool around it. Now take the wool and form a peg by forming a loop and then turning it clockwise passing it ...more
Since Apple launched iOS 13, we've seen four major updates for iPhone, each of which added some cool new features. Between iOS 13.1, 13.2, 13.3, 13.4, and all the minor updates in between, there's never been a better time to be on iOS. And now, we've got even more positive cha ...more
The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company ...more
Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes ...more
Back in the day when computers relied on CRT monitors, having a static image displayed for too long actually resulted in the image being burned into the screen. For this reason, screensavers were developed, which display animated images in constant motion to prevent burning in ...more
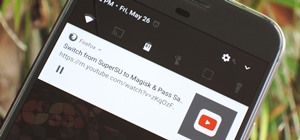
OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, y ...more
Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time! Today, Minecraft 1.4.2 was released, and it's a doozy. Versions 1.4 and 1.4.1 were actually skipped entirely, as lots of bug-fixes were patched between th ...more
Vasectomy is birth control option for men which involves a surgical procedure that will prevent sperm from passing through the vas deferens. Watch this instructional video to learn more about vasectomy and see demonstrations of two occlusion techniques that involve thermal cau ...more
The best go-to method for reducing your risk of infection is to wash your hands. Next time you reach for the soap, here is some news you can use. For years, soaps and healthcare products touted their "antibacterial" properties. While soap was good, antibacterial soap had to b ...more
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exp ...more
While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we ha ...more
If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone. Several Nexus 5 owners, myself included, have complained of a seemingly random spike in auto brightness levels towards the high or low e ...more
Since iOS 11, a thumbnail preview appears on your iPhone whenever you take a screenshot. It's useful for access to quick sharing options and editing tools, but you can't disable the preview image. You can wait for it to disappear or swipe it off-screen, but that's as good as i ...more
Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your sys ...more
Holton Rower's Pour recalls the lysergic 1960s at their most saturated. So much so that, had Timothy Leary been an abstract expressionist, it's easy to imagine that his work might have borne more than a passing resemblance. The process is essentially self-evident: build a flat ...more
In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between ...more
OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all ...more
For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and se ...more
Learn how to make a pen in which to easily conceal and retrieve test and exam answers by watching this how-to video. If you're too lazy to do your reading, or you don't think you have a prayer of passing, try a cheat sheet. Check out this video tutorial and learn how to hide a ...more
The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right n ...more
Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks ...more
You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down th ...more
In a recent arbitrage tip, we showed you the secret to making money fast by buying and selling the same thing over and over again on eBay. But there's one thing you need to know about the buying part—get the lowest price possible! This article aims to show you some of the best ...more
There's no doubt about it—the most elite military force in the United States is hands down, the Navy SEALs. They can operate at sea, in the air and on land, and their ability to conduct missions underwater separates them from most other military units in the world. They've fou ...more
While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. ...more
When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. Bu ...more
So, you want to install the Oreo beta on your Galaxy Note 8 but you're not sure if it's stable enough. It is a beta, of course, so waiting until others have tried it out sounds safer. Well, over the past five days, I've used the T-Mobile version as my daily driver and there ar ...more
Now that you have your two-letter words down and have practiced your skills, it's time to move on to another important part of Scrabble gameplay—the opening move. There's a well known adage that states, “The player going first will win 54% of the time—all other things being eq ...more
If you have so much as a passing interest in jazz piano, then you've surely heard of Art Tatum. This two-part tutorial offers a visual demonstration of one of Art Tatum's favorite licks, the two-finger descending run. While this tutorial is best suited for intermediate or adva ...more
Home cooks are often quite intimidated when trying to reproduce the delicious ethnic dishes they enjoy at various restaurants. Thankfully, there are definite flavor profiles and spice/seasoning/herb combos that are very specific to various regional cuisines and cultures; with ...more
Getting a tattoo will never be a walk in the park, but it can be less painful if you take a few simple precautions. You Will Need * A licensed tattoo artist * A morning appointment * Loose clothing * A full stomach * A non-aspirin pain reliever * Deep breaths * Scrupulous afte ...more
Minecraft Beta 1.3 has introduced some awesome elements to the game, foremost among them for all you Redstone heads out there is the Redstone Repeater. It's a new block you can craft that allows you to adjust the delay on the redstone circuit passing through it, allowing more ...more
Learn how to do dumbbell clean and presses. Presented by Real Jock Gay Fitness Health & Life. Benefits This exercise converts a classic shoulder exercise, often done with a barbell or kettlebell, to take advantage of its leg-busting potential. Put squats between the elements o ...more
The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users. Even after the initial re ...more
Many recipes call for self-rising flour as a staple ingredient. Oftentimes, we find ourselves passing these recipes by because we don't have it on hand, or because we don't use it enough to actually want to buy it. Don't Miss: Cook Like a Chef: Use Ratios, Not Recipes Lucki ...more
With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative. Ruby is just one wa ...more
Hello friends. This is actually my first how to. In this tutorial I'll be teaching how to simply copy someone's WhatsApp pictures gallery into your computer, in an automated way. It is just an example of how easy is to steal data from someone's smartphone. I am covering Whats ...more
Whether your plane made a crash landing or your ship got lost on a three-hour tour, now you're stranded on a remote island. Here's how to get help. You Will Need * A freshwater source * Some dry sticks * Rocks and leaves * Clothing * A mirror or a reflective object * Cell pho ...more
Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all beca ...more
If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module. This tool is useful if you're managing a large num ...more
A half nelson is a modification of the nelson wrestling hold in which you pin your opponent down by passing one hand under the arm of the opponent and locking your hand at the opponent's neck so he can't move. This is a basic though super effective wrestling move used commonly ...more
When is a knot not a knot? When it's a grip. The knot outlined in this video isn't a knot per se but a way to wrap objects to increase their grip and also to store extra paracord. Specifically, this video demonstrates how to County Comm Micro Widgy Bar, which is a miniature p ...more
The Galaxy S5's fingerprint scanner feels like something straight out of a sci-fi movie. Giving you the ability to lock your device without having to fuss with a PIN or password every time you go to use it, the feature is definitely one of the device's main selling points, esp ...more
Watch to learn how to get infinite EXP with proxies in MyBrute (04/23/09). It shows how to get exp from pupils you make by passing the current two checks (Flash SOL files and IP check). Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Visit mybrute.com to ...more
Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in th ...more
Learn how to make a ‘Spool Tractor’ using common household items, as demonstrated in this video. You would need the following items to make it: • A spool of thread • Rubber band- 1 • Paper clips- 2 • Clothes peg- 1 Begin by passing a paper clip on one side of the rubber band. ...more
Apple likes hiding things in its software, including secret apps, hidden iMessage effects, status bar customization, nameless icons, and red screen mode, but some of its best Easter eggs are right in front of you on the Home Screen. Some of Apple's app icons on iOS 17, iPadOS ...more
Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software en ...more
Greetings my fellow aspiring hackers, Huh :) . Its that part of the year when friends and family come together for reunions and family gathering. Christmas is the only time of the year where the sensation and desire to bond and repair lost and broken relationships becomes str ...more
Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the g ...more
Learning to play your favorite songs on your guitar is not only a wonderful way of passing the time–and impressing those whom you'd like to impress–, it can do wonders for your technique. In this song tutorial from Siggi Mertens' series of beginning guitar lessons, you'll lear ...more
In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffi ...more
I passed a cool looking bar the other day that I wanted to check out. When the weekend came around, I was ready to go, but for the life of me couldn't remember where it was. Not wanting to retrace my steps or drive around aimlessly, I gave up. Sure, I could've browsed Yelp fo ...more