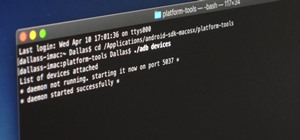
If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achi ...more
Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a b ...more
Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No lon ...more
While it's easy enough to take a screenshot of an end-to-end encrypted Telegram chat thread using an iPhone, it's an entirely different story on Android phones. Telegram disables screenshots for Secret Chats by default on Android, and not everyone can turn it on. Sometime in ...more
There's a recently discovered flaw by iDownloadBlog that lets thieves reset a stolen Apple Watch without a hitch, which is the result of Apple not including the Activation Lock feature that iPhones have had since iOS 7. Activation Lock requires your Apple ID and password to e ...more
No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly! I hope you had a good Christmas and happy new year! Update1: Added the section "weaponizing your Android" where I talk about apps and fundamental Kali ...more
Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by ...more
If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart. When you run programs an ...more
We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web. However, I should ...more
Want to make a phone call on an iPhone 4 running Apple's iOS 4.1, but don't know its passcode? Not a problem. In this clip, we learn a simple trick that will allow you to bypass the lock screen entirely and permit you to view the phone's contact list and place phone calls to a ...more
If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand. New feat ...more
Windows 10 makes it a cinch to change the lock screen background: simply go to Setting -> Personalization -> Lock screen, then change the background to whatever you'd like. But, trying to change the login screen background—the screen where you enter your password—was a long, c ...more
Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have alread ...more
Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking. Luckily for those o ...more
With AirPlay for iOS, Chromecast Screen Mirroring, and even third-party PC-pairing apps to play around with, getting your devices to interconnect could not be any easier than it is today. Samsung has never been prone to leave a feature unexplored, so in this mold, they create ...more
The iPhoneHackers shows viewers how they can install Installous on their iPhone and Download free applications. First, you will need to have a Jailbroken iPhone or iPod Touch with Cydia. Your first step, will be to load Cydia on your iPhone. When Cydia has loaded click on 'Man ...more
Apple released iOS 12 on Sept. 17, and most of the announced features have been released for the iPhone's latest available operating system. However, some brand new features can be accessed with Apple's latest beta, iOS 12.4. If you want to try out all its new features before ...more
To serve as a framework for the "Nexus Imprint" feature in their new Nexus 5X and Nexus 6P smartphones, Google added native fingerprint scanner support to Android 6.0. Sure, Android devices have had fingerprint scanners in the past, but this is a unified, system-wide implement ...more
Developers options is one of the first things tinkerers unlock on a new phone. However, even the less tech-savvy users will find some benefits to revealing this hidden menu, as it enables features such as GPS spoofing and faster animations. By default, this menu is hidden awa ...more
Windows has always been pretty customizable, and there are a ton of ways to change up the way your PC looks—though, it hasn't always been easy. In the past, changing anything other than wallpapers, titlebars, and fonts involved long hours of switching out system files with mod ...more
What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break? But leaving your phone at home or in the office when you go out is absurd, I mean, everyone b ...more
Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds. These banners are what the ...more
Did you know that you can use Gmail to make free phone calls to anywhere in North America? We're not talking computer to computer, but actual free phone calls to cell phones and home phones. All you need is a Gmail account, a microphone, and speakers plugged into your compute ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more
After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their M ...more
Facebook's mobile app lacks many features from the desktop site. Even if you open Facebook in your phone's browser and request the desktop version, all that does is basically resize the mobile app. But there's a simple workaround that will force Facebook to appear in all its d ...more
Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications. In previous tutorials, we have touched on some of the techniques and tools for web app hacking. We looked at web app vulnerab ...more
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Ac ...more
The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better compr ...more
If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particula ...more
Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But ...more
Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits! Requirements If you don't already have it, install MITMf via apt-get install mitmf. Yo ...more
I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase. If someone can access your wireless networ ...more
Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But w ...more
EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit ...more
According to WitsView, 8-inch displays will rule the tablet scene this year at 11.9% market share, compared to yesteryear's 2.6% market share. By year's end, it'll be almost 18%. Apple broke the trend for smaller 7-inch tablets with their iPad mini, which is just under 8-inch ...more
One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a les ...more
Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device. Deleting your messages and pictures manually is a good to protect yourself from aver ...more
By default, your Samsung Galaxy S III comes equipped with a few app shortcuts that are available from the lock screen. But what if you don't use those apps very much? Wouldn't you rather customize the lock screen icons on your S3 to your favorite and most used apps? Well, it' ...more
For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your ...more
Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone. Th ...more
By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions. We've spent the last few days getting to know it, and let ...more
WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs ...more
I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After ...more
PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's comput ...more
If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the ...more
If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask. Whatever ...more
Macheads101 shows us a simple command to erase your entire hard drive in a MAC OS x terminal. You can either log in as administrator and simply type "rm -rf /" to format or you can just type "Sudo rm -rf /" to start. If you don't log in as administrator, then it'll ask you for ...more
Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 month ...more
I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends. Everyone who l ...more
SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highl ...more
In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as ...more
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you ...more
When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings. Why? Well, for once, we finally had a smartphone, or in this case, a pair of sma ...more
If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs ...more
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone ...more