Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, th ...more
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these e ...more
A single movie download can consume a good ten percent of the storage on your Nexus 7 tablet, unless you went all crazy and opted for the 32GB model. Even then you're bound to run out of space fast, especially if you're like me and have tons of media files you want readily acc ...more
If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, ...more
Out of the more than 200 new features Apple included with iOS 13, perhaps none is more anticipated than system-wide dark mode. Finally, we no longer need to blind ourselves when responding to an iMessage late at night or checking Reminders to see the following day's tasks. But ...more
Want to search through your Samsung Galaxy S III or other Android smartphone using only a web browser? Thanks to XDA-Developers member Metal Droid, you can now access and download anything from your phone through any browser on your computer using DroidXPlorer. With DroidXPlo ...more
Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable. For example, you could send the credentials your victim enters to a script that mails you notifying you of new data someone's just entered, or automatically store them in ...more
Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help ...more
Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device. Th ...more
The Android Nougat preview build for Nexus devices comes packed to the brim with new functionality: multi-window mode, a dark theme, and a data-saver toggle, just to name a few. However, unless you have a Nexus device, it will be a while before you get these exciting new featu ...more
Inspiration for tutorial: Foxtrot's "How to Trap a Tracker" If you have been following my past tutorials, (and it's fine if you haven't,) you would know how much social engineering and doxing I do. During these moments when we are convincing people that we are a different per ...more
Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics seri ...more
You may note be able to root your Snapdragon-powered Note 10, but thanks to the hidden Developer Options, you can still tweak low-level settings like custom codecs for better audio quality on Bluetooth headphones and faster animations to enhance your experience. Best of all, y ...more
In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential v ...more
To restore an iPod Touch from lockout or forgetting a password, pull up iTunes on whatever computer you are using. Plug the USB cord into the iPod touch and plug the USB cord into the computer. The iPod will say "locked out" or "access pass code" and the computer will says tha ...more
This video teaches you to sync Google Calender with the Apple iPad Calender app. The first step involves going to 'Settings' and then to 'Mail Contacts Calenders'. Add an account to the application. For doing this, go to Microsoft Exchange. Type in your email ID in the space p ...more
Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it i ...more
Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way ...more
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buy ...more
You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen? Instead of entering in your passcode or pa ...more
A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangib ...more
For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's abili ...more
Beta software can be exciting because you get to experience cool new features before most other people. But it can have unwanted consequences such as bugs, UI glitches, and horrible battery life that'll make you wish you never installed it. If that sounds like you with iOS 16 ...more
Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up f ...more
Hello NullByte! This will be my first How To series. In this tutorial you'll learn what SQL is, what SQL injection is and how it benefits you as a hacker. I strongly recommend learning at least the basics of PHP before attempting to learn/use SQL Injection. list of reference ...more
Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop. Having a strong password is the ...more
The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program ...more
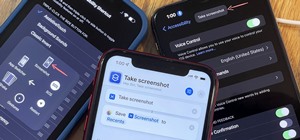
Videos are great for catching fleeting moments, and photos are insanely easy to share with anyone, but how can you get the best of both worlds? Apple includes an easy way to take snapshots while you're in the middle of recording video, but that's just too much work for me. I' ...more
We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privac ...more
Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. M ...more
Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic functio ...more
Have you ever been locked out of your iPhone? Maybe you forgot your passcode. Or perhaps someone with access changed the passcode as a prank. Your iPhone's display could have even been damaged and unresponsive. Whatever the reason, there's an easy way to get back access to you ...more
Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre ...more
For parents that have an iPhone X, things are about to get a lot easier for you in iOS 11.3, which finally lets you approve app and media downloads on your child's iPhone using Face ID instead of typing in a password. You can ban certain apps and movies, as well as in-app pur ...more
You don't have to see every app installed on your phone if you don't want to. Samsung One UI makes it easy to hide apps from your Samsung Galaxy's home screen, app tray, and search tool, whether you want to declutter, simplify things, or keep other people from seeing some of t ...more
This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong. You probably know that Ettercap is a very powerful tool for man in the middle attacks. You probably know tha ...more
While there isn't as much personal data residing on your Apple Watch as there is on your iPhone, it's still a good idea to set a passcode for it and lock it up when you're not using it. If you don't, while it's charging or otherwise off your wrist, others may be able to sneak ...more
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device ...more
Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills. Wh ...more
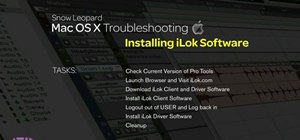
Spotlight, Apple's selection-based search system, received a major facelift on Mac OS X Yosemite. Packed with dozens of new features, such as a central search window and increased app suggestions, the reworked Spotlight was a breath of fresh air. While the Spotlight Search to ...more
With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative. Ruby is just one wa ...more
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin ...more
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling ...more
So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a ...more
I love my Mac to pieces, but there have been times, so many times, that I wanted to silence that classic Apple start-up chime. I mean, the only thing the sound does is notify everyone around you that you have a Mac, and that you have turned said Mac on, right? Well it's not so ...more
It's easy to back up and restore your iOS devices using iCloud, but there are a few downsides to encrypted iCloud backups. For one, Apple holds the key to decrypt all the data. Plus, you're limited to only 5 GB of data for free before you have to upgrade your storage to 50 GB, ...more
It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for ...more
BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the ve ...more
SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool c ...more
It took a while, but the premiere custom recovery for Android is now available for Google's Pixel 4 and Pixel 4 XL, so it's finally open season on root mods. TWRP custom recovery allows you to install Magisk and get root access in a few taps, and it can even save you from the ...more
The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that ...more
Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by acci ...more
With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world. As th ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your devic ...more
Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are th ...more
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, b ...more
Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app. Since Androi ...more
Apple might not be finished with iOS 17. While the iOS 18 update was already released, there may still be things for Apple to fine-tune on your iPhone. This brings us to iOS 17.8. Will it happen? And will there be a beta? Since the feature-packed public release of iOS 17, we' ...more
Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don' ...more