You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and en ...more
Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). R ...more
As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port ...more
Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase tha ...more
The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an ...more
For the most part, when you're copying text on your Android device, it's because you intend on pasting it into a different app than the one you're currently using. For instance, you might be looking at a posting on Craigslist. So you copy the seller's phone number, then head t ...more
Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with ...more
Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educate ...more
One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple ...more
The new and improved Side button, as well as a plethora of new swipe gestures, are responsible for picking up the slack left by the missing Home button on the iPhone X. If you're really missing that Home button, however, Apple's built-in AssistiveTouch tool can help you out by ...more
Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the sca ...more
Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering. One such distribution is Pentoo, a Gentoo-b ...more
CONTEST ENDED: WINNERS ANNOUNCED This contest has ended and winners have been announced. To see who won, check out our quick winners post. Thanks to everyone for submitting their ideas! ORIGINAL CONTEST Mad Science is back with another contest this month. This time, you've ...more
If you don't want to wait for Android 4.3 Jelly Bean to hit your HTC One, you don't have to. Android developer LlabTooFeR released his MaximusHD ROM, which includes a leaked copy of HTC's own 4.3 update, complete with Sense 5. Warning This will only work on GSM models of the ...more
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way. What Exactly Is a Nandr ...more
Lookin' to master a hot new dance move? Check out this tutorial and learn how to rock the Jerk and the Dougie. Both of these dances are fun to perform and will earn you a ton of street cred if you're good. So, why not check out this step by step clip and get on your feet!?
Many of our everyday apps include a menu tab or search bar, like Chrome and Twitter. In fact, a lot of times those are the first things we go for, as search is universal in most apps, and app settings are just about always accessible through the menu. Like the Back, Home, and ...more
The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10. Don't Miss: How Anyone (Even Pirates) Can ...more
Software issues occur more frequently on jailbroken iPhones, though, they're usually minor bugs that can be fixed easily with a respring. But if your device freezes up, restarting is the only way to get back to normal, which also means having to re-enable your jailbreak. There ...more
Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's ...more
It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploi ...more
Need help tracing an IP address to a location? Well, Tinkernut has a clear and effect way to help out. First, you'll need the URL of a website you desire to trace, in this case, YouTube (youtube.come) is used. After you've done that, you'll want to go to the Start menu (Windo ...more
As great as Google's own Play Music app is, your MP3 library is restricted to Google's own app. There are much better music players that give Google Play Music a run for its money, but duplicating music files on your device for this reason alone is a waste of storage space. B ...more
The Calculator app on your iPhone may seem boring and basic, but there are a few interesting tricks worth knowing. You can ask Siri to perform calculations for you, long-press on results to copy them, long-press the field to paste numbers in, and swipe left or right above the ...more
It seems impossible. Ripping one piece of paper is effortless. Ripping a small stack of papers takes a little force. But ripping a book? No way! Actually, it can be done, but only with a telephone book. This tutorial will show you how to rip a phonebook in half, quickly and ea ...more
To share a song or album to family and friends, it's as easy as copying its link in the app and pasting that into a message. However, not everyone uses the same music streaming service, so a link to an Apple Music song won't do a Spotify, Tidal, Pandora, Deezer, or YouTube Mus ...more
For the purpose of simplicity, we shall consider the Windows version to be used as Windows XP. How to start the calculator in Windows XP? Here are two ways to get there: Start -> All Programs -> Accessories -> Calculator Start -> Run -> calc This demonstration of the usage ...more
Most coin vanishing tricks rely on sleights of hand and some skill; this easy magic trick just uses the physical laws of light refraction, and is much easier than that makes it sound. Learn how to perform this disappearing coin trick, great for a night out at a bar, by watchin ...more
No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the In ...more
File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, ...more
Checkra1n is by far the best way to jailbreak A7- through A11-powered iPhones on iOS 13 and later, but it's not without its downsides. Besides the lack of Windows support, the tool limits your choices to Cydia alone. With a little elbow grease, however, you can easily replace ...more
The pumpkin is everyone's favorite cucurbit come Halloween time, and while there are only a few types of Halloween-friendly pumpkins out there, there is definitely no shortage of what you can do with them. You can carve faces into them, perform brain surgery, make them sing, ...more
Your brand new iPhone SE packs the latest A13 Bionic chip into the form factor of the iPhone 8. With all that modern tech, you'd expect your iPhone to be unstoppable. That said, no smartphone is perfect, and sometimes, the iPhone SE will give you trouble. If your device is fro ...more
The Pixel 5 is a bit of a departure from previous Pixels. Gone are the Pixel 4's Soli-based Motion Sense gestures, the Pixel 3's dual front-facing speakers, and the glass back panel of previous generations. But perhaps the most notable omission for long-time Pixel users is the ...more
Rooting has a long and storied history in the Android community. As OEMs push out more refined software, the need to root has diminished — still, the number of incredible things you can do with a rooted phone is enough to tempt many enthusiasts. Luckily, some manufacturers are ...more
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at ...more
In this tutorial, I'm gonna show you how to make another amazing paper plane that can fly really far. GUARANTEED. Video: . Once you've made all of your folds and the plane looks symmetrical, it's time to trim it, or adjust it, for flight. This is very important, unless you wan ...more
Rave light shows are one of the most intimate and enjoyable experiences that people can share at a rave, but getting started when you don't know what you're doing can be a scary thought. Watch this video to learn how you can perform some basic glove lighshow moves like the fig ...more
There are times when physically interacting with your iPhone is less than ideal, like when you're cooking or driving. Fortunately, iOS 13 has you covered regardless of the circumstance you may find yourself in. With the new Voice Control feature, you can control pretty much ev ...more
With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. ...more
The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the ...more
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your ...more
Samsung and Google have done some amazing work together in the past, particularly with Android related projects. But after years of an inexplicable lack of interoperability, the primary smart home hardware divisions from both companies are finally on the same page — starting r ...more
Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebo ...more
One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple ...more
We may all have a Nexus 7 tablet, but we don't all want to have the exact same look and feel, which is why we softMod for a more personalized vibe. There are hundreds of cool mods you can perform on your Nexus 7, whether stock or rooted, but one of my favorites in Android 4.4 ...more
In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need f ...more
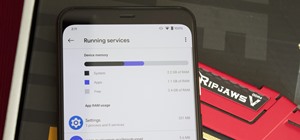
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has contin ...more
This is a guide for how to perform and as a patient prepare for a pap smear.
Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbl ...more
Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's ...more
Connecting your new smartphone gadget to your desktop isn't just connecting these products with a USB cord. It is important to sync them to allow the transfer of data from your smartphone to your computer and vice-versa. This is desired if you wish to transfer information incl ...more
Team Win Recovery Project (TWRP) is a custom recovery for Android devices and the one used by most softModders, mainly because it has touch-based actions, as compared to the more time-consuming button-based approach that ClockworkMod (CWM) uses. With TWRP, you can flash new R ...more
Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science. Watch ...more
This video will show you how to perform a great bar trick/puzzle/proposition bet called the "Three Knife Scaffold". This trick is super easy, it just takes a bit of know-how. In this tutorial, learn how to place your knives in order to fool your friends and win any bets they m ...more
I don't know about you, but when I shoot a slow-mo video on my iPhone, I'd also like to have a regular speed copy of it, just in case slow motion doesn't fit the video right. Traditionally, converting slow-motion video required manually speeding the video back up in editing a ...more
How to make TCPO or bis(2,4,6-trichlorophenyl) oxalate, used in glow stick reactions. WARNING: This procedure should only be performed by, or under the direct supervision of, an experienced chemist. Please refer to the material safety data sheets of all chemicals for their ha ...more
This is an easy & simple way to make your home made compass using stuff that can be found in every home. You will need a magnet, a paper clip, a glass of water and a piece of paper. Check out this instructional science video to learn a a quick and easy method of making your ow ...more
The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely. The sheer volume of Windows computers currently in operation around the world ...more
While Siri came up on the scene with hardly any competition back in 2011, Google Now has not only caught up to Apple's intelligent personal assistant, but also excelled in certain areas—with its ability to quickly answer questions, give recommendation, and even deliver informa ...more