Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can b ...more
Welcome back, my hacker novitiates! Now, and more so in the future, wars will be fought hacker v. hacker. The number of soldiers, guns, tanks, and ships will be less important in your success in warfare than the number of well-trained hackers you have. Every nation and every ...more
Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (tak ...more
Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the or ...more
No matter how cool my 3D live wallpaper is, or how often my Google Now wallpapers automatically change, I always want more backgrounds. Zedge has made it easy for me to find new ones, and 500 Firepaper helps me keep my background lively with rotating wallpapers—but these aren' ...more
Not everyone has the "Sun" or "Apollo" line on their palm. For those lucky enough to have it, such a line indicates many potential gifts and popularity! Watch this video as Jim Winters explains how to identify the Sun line and what it indicates for the individuals who have them.
I don't like paying for repairs, and I don't like purchasing extended warranties. When one of my gadgets break, I perform emergency surgery and try and fix it myself. It doesn't always go well, but I've managed to resuscitate a few iPhones, an HDTV, an Android tablet, multiple ...more
The Kinect for Xbox 360 and PlayStation Move might be fun to play with, but people do not look very cool while they're doing it. Air guitar is not particularly flattering (even if done on stage), and neither is air-anything else, as pleasurable as it might be. This is why I fi ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
Your Instagram followers deserve to be heard. Whether through polls or DMs, Instagram offers your followers a unique way to share their thoughts and opinions with you on any subject you can think of. Now, the social media giant is expanding these options with the introduction ...more
I loved the Gold Rush unit back in third grade. We went up to the American River and panned for gold, and my panning skills balled above all. I got like three tiny pellets. Of course, it was all fool's gold, aka pyrite, but it was still pretty legit. And this was before wearin ...more
Swipe keyboards such as GBoard, SwiftKey, TouchPal, and Swype are handy for quick one-thumbed typing on an iPhone, but Microsoft upped the game with its experimental Word Flow Keyboard. In short, the keyboard fans out to occupy the natural range of your thumb, where you can ty ...more
With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping ...more
Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudul ...more
Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this ...more
Andre Geim and Konstantin Novoselov, from the University of Manchester, have just won the Nobel Prize in physics from their work with graphene. They've found a way to isolate graphene from graphite (carbon in pencil lead) and distinguish its behavior, which holds extreme poten ...more
Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craig ...more
Maya can count itself among the most powerful and also most challenging programs in all of computing. It's 3D modeling potential is nearly limitless if you can master its intricacies. This video features a professional digital art teacher teaching you how to model a 3D head us ...more
It's tough out there on the battlefield, especially when your stuck in the trenches and your comrades are dropping like flies. There's no hope. At least, until the next airsoft battle. So, enlist the help of a little unmanned airsoft artillery with this DIY motion-activated a ...more
Making a video game requires an incredible amount of work. It requires people skilled in many disciplines to work together for thousands of hours merging visual art, computer programming, game design, sound design, and music composition into a fun game. The Indie Stone is a Sc ...more
IV's are used on patients to either administer fluids or medicines, and for a nurse, it's the number one task performed on the job in a hospital. Knowing the proper procedure for peripheral intravenous catheter insertion is a must. This interactive video module will help famil ...more
Learn how to do dumbbell clean and presses. Presented by Real Jock Gay Fitness Health & Life. Benefits This exercise converts a classic shoulder exercise, often done with a barbell or kettlebell, to take advantage of its leg-busting potential. Put squats between the elements o ...more
There is something so satisfying about dipping your spoon into a perfectly smooth slice of cheesecake. There is something a bit less satisfying about it if the top of the cheesecake is cracked and cratered. A Bailey's cheesecake, humorously called an "earthquake cheesecake.". ...more
Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities. I ...more
Lamb has the potential for great dinner recipes. Watch this how to video tutorial and find out how to prepare a leg of lamb to roast with UKTV Food. Learn to trim the leg of lamb for so that you get the most flavor from it.
Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version ...more
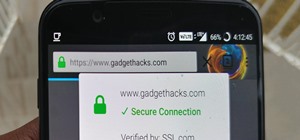
In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential v ...more
Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combinatio ...more
Among the many new changes ushered in by the iPhone 7, only one has the potential to completely change the way you interact with your smartphone—a new 3D Touch-enabled home button. Instead of the mechanical click we've grown accustomed to, your home button will now behave like ...more
Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for An ...more
So, when Christopher brought up Nikola Tesla in his very first post on Fear of Lightning, it got me interested in learning more about the man behind alternating current. There is plenty of info out there on the Internet, widely available for free, but sometimes it's just nice ...more
Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre ...more
There's a feature that every Apple Watch owner should know about — one that makes navigating menus, tapping tiny icons, and interacting with complications, among other things, much easier on the small display. The little-known feature gives you complete control of your Apple ...more
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the ...more
Yogurt is more than an excellent source of protein, calcium, and gut-healthy probiotic bacteria. A protein isolated from probiotic lactobacillus bacteria in yogurt is capable of inhibiting drug-resistant bacteria. Rachelle Allen-McFarlane, a doctoral candidate at Howard Unive ...more
With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play ...more
If the rumors are right, Microsoft has decided to cancel the second version of the HoloLens, and they will instead move onto version three of their mixed reality headset. In the latest report, Thurrott's Brad Sams states that the expected release date of this new Windows Holog ...more
There are already a few ways to use your home computer on the go, but none of them feel very natural when you're out and about, and are clunky options at best. Samsung wants to change that with Monitorless, their upcoming augmented reality smartglasses, which offer remote desk ...more
With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative. Ruby is just one wa ...more
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin ...more
The most gifted and inventive fashion designers and DIY artists see the potential in things other people would overlook or deem trash. DIY guru Gianny L, for instance, takes everything from men's underwear to oversized t-shirts and turns them into fashionable clothing for wome ...more
In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers wi ...more
Whether your plane made a crash landing or your ship got lost on a three-hour tour, now you're stranded on a remote island. Here's how to get help. You Will Need * A freshwater source * Some dry sticks * Rocks and leaves * Clothing * A mirror or a reflective object * Cell pho ...more
Crusty, itchy, red eyes? There is a decent chance you could have conjunctivitis, or pink eye, an infection of the thin lining around the eye and the eyelid, caused by bacteria, an allergen, virus, or even your contact lenses. Whatever the cause — you call up your doctor to get ...more
So very pointless, yet unquestionably spectacular. The best kind of "art" performs no other function than to delight the viewer, and Japanese YouTube user Denha's complex marble machines do just that. But are marble machines art? You can call them that—or toys, scientific cont ...more
Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all beca ...more
This past weekend Berlin celebrated the 20th anniversary of the fall of the Berlin wall with a visit from France's Royal de Luxe street theatre company. Royal de Luxe creates insanely amazing large scale, mechanical street marionettes. Founded in 1979 by Jean Luc Courcoult, t ...more
The shooting of Walter Scott (who was unarmed) has been dominating the news these past few weeks. Scott, who ran away from police officer Michael Slager after a routine traffic stop, was shot in the back and pronounced dead shortly thereafter. Unlike similar cases where a cop ...more
We Harry Potter fans all remember Hogwarts students pulling Mandrake Roots in the greenhouses in Chamber of Secrets. Well, in Harry Potter: Wizards Unite, we now have an opportunity to work in our own Greenhouses, as well as dine inside Inns scattered throughout the map. Let's ...more
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most ot ...more
How does text messaging figure into a dating relationship? Tracey Cox discusses the proper way to "text flirt" in any relationship. Learn the etiquette of text messaging and the potential relationship pitfalls associated with it. Flirt with text messages. Click through to watc ...more
A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks. GitHub user ZioShiba posted the iBoot source code for i ...more
Galaxy S8 preorders have begun arriving at doorsteps, and some websites seem to be enamored by Samsung's latest visual revamp of TouchWiz — but don't buy the hype, it's a trap! From TouchWiz to Grace UX to Samsung Experience, no matter what the name is, it's still the same old ...more
Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app. Since Androi ...more
Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to prote ...more
Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if ...more
Although mainly demonstrational, this video shows you how to play a song "Summertime" in D minor on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning: This is a loose an ...more
No matter if you've used one or not, you've got to admit that 3D printers are pretty darn awesome, especially the self-replicating ones that extrude molten plastic and the shoebox-sized versions that use mesmerizing stereolithography to build tiny objects layer by layer. But w ...more
Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such f ...more
We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're ...more