The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that wi ...more
You may not always be connected to the internet, but if you're anything like me, your thirst for web content is insatiable. Whether you're on an airplane or stuck in an area with no reception, having some offline content stored on your Nexus can definitely save the day. Apps ...more
When you take a screenshot on your iPhone, it's automatically saved to your Photos app. You can ignore the screenshot thumbnail or swipe it away, but you shouldn't. If you open the screenshot editor instead, you'll gain access to your iPhone's most useful screen capture tool: ...more
Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corres ...more
Given the volatility of cryptocurrencies like Bitcoin (BTC), Ethereum (ETH), and Ripple (XRP), it's good to keep track of your transaction history and get a better idea where you stand financially. Though tracking down past trades on Binance may seem convoluted at first, it ge ...more
Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other ...more
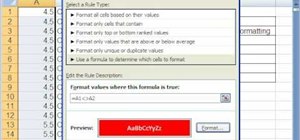
To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant ...more
Welcome to Math Craft World! This community is dedicated to the exploration of mathematically inspired art and architecture through projects, community submissions, and inspirational posts related to the topic at hand. Every week, there will be approximately four posts accordi ...more
When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the in ...more
Computer Science Professor Francesco De Comité has a fantastic gallery of mathematical images on Flickr. As part of this collection, he has a few hundred images of real or rendered polyhedra made out of paper or playing cards which he calls "slide togethers." These are constru ...more
Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal. And ...more
One of the most useful new features Apple included on iOS 16 lets you instantly lift the subject out of a photo, separating it from the background. Once extracted, you can paste, save, or drop the cutout wherever you want as a new image, and you can even make it a sticker in m ...more
Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's ...more
One of the greatest things about the internet? Free papercraft downloads. Enjoy Botropolis' collection of 50 fun robots. Just download, print, and assemble. My top ten favorites below. Wall-E. Robocop. Optimus Prime. R2-D2. The Terminator. Poseable Toy Robot. Retro Bot. Godzi ...more
Apple has finally given us a decent file manager in iOS 11. The new "Files" app replaces the not-very-old iCloud Drive app that appeared in iOS 9, but you can still access your iCloud Drive files in the new Files app, as well as files from third-party cloud services. A nice im ...more
In this article you will learn how to understand written origami instructions, called diagrams. You can follow the video below or read the entire article Video: . History of Origami-Diagramming While many do not realize, the now accepted system of explaining how to fold origa ...more
Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System ...more
So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for? And what about your movies? W ...more
As the holidays draw closer and closer, stores are getting more and more crowded, and of course, many have put off their Christmas shopping until the very last minute. Why not avoid the mall rush this holiday season and make a personalized do-it-yourself snow globe to gift to ...more
Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price lo ...more
While some mobile sites have built-in text-resizing tools, many do not. A lot of those that don't won't even let you pinch-to-zoom. That makes it difficult for people with low vision to read small fonts on their iPhones. In some cases, like with photo captions, even those with ...more
I know what you're thinking—taking a screenshot is super simple. While that is partly true, taking of a screenshot of the Start Screen in Windows 8 is little bit tricky, unless you're on your Surface. The new Windows 8 works in two different realms; the normal desktop mode th ...more
Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments. Welcome to my 9th post, this tutorial will explain how to extract and decrypt WhatsApp database from the Victim's android system. ...more
Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/W ...more
This video instructs the watcher on how to create a passport-sized photo in Photoshop. First, open Photoshop and choose the image that you want using the "Browse" option. Then go to "image", from there "select image size" and select the image size you want (e.g. 35 mm by 43 mm ...more
An awesome new feature appeared in iOS 11 that lets you easily share your Wi-Fi password to anyone else with iOS 11 or higher just by tapping "Share Password" on your iPhone when they try to connect to the same network. However, if your friend is using Android or another mobil ...more
Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more paral ...more
Fifty-four percent of Americans 18 and older drink coffee every day, and why not? With 100 milligrams of caffeine per six ounces of drip coffee, it's just the morning beverage to wake you up and kickstart your day. You can feel the caffeine surge through your body like the Hol ...more
Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 month ...more
SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to ...more
You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone. The status bar's background on iOS is transparent, so you'll see different colors and gradie ...more
In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! Hello Guys, Welcome to my tutorial and in this tutorial, We are basically going to create a python script that serves as a proxy server ( Without External ...more
Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here. As I mentioned in previous tutorials, Python is prob ...more
Your first, very basic web crawler. Hello again. Today I will show you how to code a web crawler, and only use up 12 lines of code (excluding whitespaces and comments). Requirements Python A website with lot's of links! Layout the logic. OK, as far as crawlers (web spider ...more
Adding and subtracting may be the easiest of mathematical operations, but once you get it down, multiplication and division can be just as easy. That's why it's called elementary arithmetic. If it were harder, it would be called college algebra or trigonometry. But it's not— i ...more
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle ...more
Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input ...more
Dried out markers are the worst. They take up space, and for some reason, even though they're totally useless, most of us have at least a few lying around just for the sake of not throwing them out. Luckily, Julie Finn over at Crafting a Green World has come up with a way to r ...more
To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added ...more
In the tech world, it's all too common to slap a fake label and packaging on a lower quality product, especially SD cards. If you've ever bought an SD card on the cheap from a slightly-less-than-reputable source (or even a reputable source, in some cases), how do you know if i ...more
There's a little-known secret in the world of microwave ovens that even the manufacturers don't care to tell you in their manuals. And once you know it, you'll never go back to using your microwave as you used to. Some microwave owners have figured this "hack" out on their ow ...more
I won't mince words: the Notes widget in iOS 14 is bad. But you're not stuck with it if you want sticky notes on your home screen. Although I enjoy iOS 14's updated widgets overall, its Notes implementation was poorly thought out. I was hoping for a large sticky note on my ho ...more
Pioneered by Rufus Butler Seder in his popular children's picture book Gallop!, and ably demonstrated by WonderHowTo favorite brusspup in the video below, "scanimation" refers to a novel (but distinctly old-timey) technique for cramming multi-frame animations onto a single she ...more
With portable devices being a necessity in modern everyday life, they may be subject to overuse, improper charging, or normal wear and tear. For those people who carry around their smartphone or iPod with them all of the time, how many times have you been out and about just to ...more
I can't believe it, but I've actually read about dozens of people getting their iTouch, iPhone, or iPad stuck in a bricked recovery loop and then going out to buy a new one. This is overly unnecessary. When it gets stuck in the recovery loop, some people mistake themselves by ...more
Let's say you receive $10 from a friend through Apple Pay Cash via an iMessage. You could spend that money in the App Store or at any retailer that supports Apple Pay using your Apple Pay Cash card. If you'd rather save it or use it for bills, it's easy to transfer that money ...more
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins ...more
File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target. To demonstrate these vulnerabilities, we'll be practicing PHP file inclusion using the Damn Vulnerable Web App. We'll ...more
"Ahoy-hoy." If telephone titan Alexander Graham Bell had his way, we'd all be answering phones like Mr. Burns. Thankfully, frienemy Thomas Edison had enough sense to realize we weren't always on the briny. He preferred "hello" as our standard telephone greeting, which he is c ...more
Cameras can be pretty pricey, but this one only costs a buck, though it's pretty limited in its functionality. That's because it's no ordinary camera, but an origami one made using nothing but a dollar bill. Of course, you don't need to spend a Washington to fold this origami ...more
An invaluable button on your iPhone can do hundreds, even thousands, of amazing things, but most iPhone users don't even know it exists. You can't push it. You can't click it. You can't press it. But it's the largest button on your iPhone, more powerful than the versatile Side ...more
When it comes to making pancakes in the morning, most of us probably follow the instructions on the box. Mix all the ingredients together, pour onto a hot greased pan, and form perfect circular flapjacks one by one. But pancakes are so much more than that. You can turn them i ...more
The "slide-together" paper construction method is a fun and satisfying way to build 3D geometric objects. It only requires paper, scissors or an exacto knife, and some patience. In Tuesday's post, we explored the slide-together method, using ordinary playing cards to build th ...more
Scanning important paperwork on smartphones is a tedious process, often relying on either external scanners or third-party apps that had to be either purchased or were loaded with annoying ads just to get the job done. Thankfully, iOS 11 now lets you easily scan documents usin ...more
To some, vegetables are even more flavorful than meat, but they're also more sensitive—overcook them and they go from extremely delicious to extremely icky real quick. They generally require very little prep, and the best recipes are the simplest. A little salt, olive oil, and ...more
I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhon ...more
During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform O ...more
Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutoria ...more
Making your own circuit boards can be a daunting challenge. You have to design a schematic, test it on a breadboard, design the board layout, and then after all of that, you still have to print and etch a board! Luckily, we have Fritzing. Fritzing is a free open-source PCB d ...more