After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. ...more
We've showed you how to make Butterfingers and Kit Kats, as well as custom-shaped chocolates, but have you ever thought about making your own gourmet chocolate bars? It's a fairly simple process, once you understand tempering, and there are endless flavor possibilities when y ...more
Breaking off a piece of that Kit Kat bar gets a lot more difficult when the whole thing weighs 13 pounds. Ann Reardon, a food scientist and dietitian with an ironic obsession for unhealthy desserts, started the very successful blog How To Cook That back in 2011 to showcase he ...more
In this article, I'll show you how to send SMS messages with Python. You'll need Python 2.7 or later, urllib and urllib2. The code basically uses an online text messaging service to "POST" html data, as if a person was entering the data themselves. The uses for something like ...more
Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself. Alas, most people don't know how to c ...more
If you've ever taken a university course with an awesome professor, you're more than likely acquainted with the precious and all-glorious cheat sheet. Like the midterm, the professor usually allows a one-sided cheat sheet for the most important exam of the class—the dreaded fi ...more
The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if yo ...more
Photoshop Disasters presents their top 20 monstrosities of 2010. Wow. Take a lesson. Egyptian newspaper Al-Ahram doctors the above photo to put President Hosni Mubarak at the head of the procession. (Read more) Shiseido amputates model. Utterly disturbing window display in ...more
This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of othe ...more
Now that Apple Pay Cash has arrived, you (hopefully) might end up getting sent some money right from inside an iMessage. If so, that money gets added to your Apple Pay Cash card in iOS 11.2, which you can use just like any other card in your digital wallet. If you're not so lu ...more
It's Monday, which means once again, it's time to highlight some of the most recent community submissions posted to the Math Craft corkboard. I also thought we'd take a look at building a sliceform model of a hyperbolic paraboloid. Rachel Mansur put up two posts on her Modula ...more
Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers w ...more
If you're not using your iPhone's Files app yet to manage images, documents, and other files on iCloud, third-party cloud services, or your local storage, it's time to start. Apple's built-in file manager is finally a powerhouse with many tricks up its sleeve in the latest sof ...more
Glass is one of the least reactive substances known to chemistry. It is the standard container material for almost all lab chemicals because it's so inert. But there are a couple of substances that have strong reactions with glass. Sodium hydroxide, aka solid drain cleaner or ...more
Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more. This project is somewhat similar to OTW's article here, and pry0cc's here, in which b ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
Need help getting started on this week's WTFoto Challenge? Look no further! In this tutorial, I will teach you how to create simple chalk symbols and writing in Photoshop. So read through this post and try it out yourself—or I'll tell your cousin what you said when you were dr ...more
The cell phone has come a long way. The very first "mobile devices" were made and used by the military in the late 1930s, with the first commercial mobile telephone service introduced by Bell in 1946. These devices were hardly what we'd call mobile today—some took up the whole ...more
If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streamin ...more
As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a giv ...more
Your phablet's large screen is perfect for viewing movies and music videos wherever you are, but as gorgeous as the Note 3's screen is, holding it gets old and you can't always find something to prop it up at a decent movie-watching angle. But there's a secret you might not k ...more
The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! As much as I love other SSH bruteforcing tools like Ncrack, Metasploit, THC-Hydra, ... ( Just to mention a few ). I prefer using my own script. The tools ab ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Let's face It ... Pennywise is going to be the Halloween costume to beat this year. It's terrifying, simple enough to pull off, and with the original movie's gargantuan box office gross and the hit status of the sequel, released in September, everyone and their pet dog will ge ...more
What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering". Before I even start, as always, I wanted to apologize for any uncl ...more
The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practic ...more
Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of har ...more
When Apple announced its new iPhone 7 and iPhone 7 Plus models in San Francisco, one of the biggest new features was an "IP67" water-resistance rating. Couple that with a few official renderings that show the new iPhone covered in water, and you'd probably arrive at one logica ...more
They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perha ...more
Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time. Bash is a simple language for stringing together several different Linux utilities. Its simplicity makes it easy for beginn ...more
There are two things I can definitively say about Katy Perry. One, she makes extremely terrible but catchy songs that I end up hating myself for singing in the car. Two, she single-handedly made Elmo the most popular Sesame Street character ever for males 13 and up (though, Ke ...more
The most convenient way for US users to buy Ripple (XRP) or Stellar (XRM) is through Binance. However, you can't deposit money directly into this app, but you can deposit cryptocurrency like ether or bitcoins to buy other alt-coins. The easiest way to do that is by using Coinb ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week: A New Year's Eve cell phone phot ...more
Would you like to create ghost flames or other custom paint effects, but don’t know how? Here is a quick, easy, and inexpensive method. This method does not require a paint gun, airbrush, or even paint. Follow this step-by-step procedure and watch the video tutorial and you’ll ...more
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information i ...more
The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems ...more
Learn from Betty Crocker Kitchens, how to easily and quickly make a dinosaur birthday cake. You do not need a special cake pan for this recipe. She uses two 9" round cakes, to cut all the shapes you need to make the dinosaur. It is only required to cut out 3 shapes, and you ca ...more
Largely self-taught, Ryan John Kothe is an animator working out of Auckland, New Zealand. After picking up some rudimentary After Effects skills, he went on to create an impressive portfolio of beautifully rendered stop-motion animations with a distinctly tactile feel. Curious ...more
Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all kno ...more
Whether or not The Purge franchise will be as successful as Friday the 13th, A Nightmare on Elm Street, Halloween, or even the Saw movies remains to be seen, but it's definitely winning in the Halloween costumes department. Don't Miss: Halloween Makeup Masks from Purge: Anar ...more
This tutorial teaches you how to download sheet music from movies, video games, and tv series. Learn to modify the sheet music to transpose the notes to any instrument and print it out. Again if you can get sibelius or finale, it might be better but Noteworthy Composer works f ...more
After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimiz ...more
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Duc ...more
These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine. In simple terms the script is self explanatory and goes to: -"%APPDATA%\..\Local\Google\Chrome\User Data\Default\Login Data" where t ...more
Invert the colors in your Windows screen by pressing Shift+Alt+Print Screen. This makes a great PC prank. Invert the screen colors in Windows. Click through to watch this video on tricklife.com
As if Captain America: The First Avenger wasn't awesome enough, Marvel hit us with Captain America: The Winter Soldier this year, and it was even more spectacular than its predecessor. Grossing nearly $260 million in domestic sales, it's safe to say America loves Captain Ameri ...more
While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach. All of the celebrity accounts that were compromised were targ ...more
Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the ...more
What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system. Understanding the Attack Whi ...more
This is one of the easiest and best computer pranks ever invented. It's simple to do, and works great. This prank causes all of the icons on the desktop to be unclickable, as well as the start bar. 1. At your desktop, close all windows if any are open, and press Print Screen/ ...more
With the plethora of programming that we promote at Null Byte, I figured a lot of you newbies that stop by IRC will need a big boost in the right direction to make your dive into programming a lot easier. A hot question that has been thrown around in IRC a lot when making the ...more
There are many things your iPhone or iPad can do, and Apple does an excellent job of documenting everything on its website. But there are some features that won't show up in any Apple manuals or help pages. We've rounded up some of the best secret features hiding in iOS 15 an ...more
Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websi ...more
If you thought the last post on Two Circle Wobblers was wild, then wait until you see what happens when you build wobblers out of two half circles or two ellipses. In both of these cases, the center of gravity still remains constant in the vertical direction, allowing them to ...more
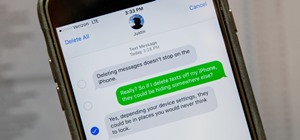
You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours. The only thing that makes you pause is that ...more
From time to time, you may need to locate the version and build number for a particular app on your iPhone or iPad, but it's not at all obvious where you can find the information. Well, there's more than one place to look on iOS 18 and iPadOS 18, but none are perfect solutions ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
The recently released HTC One M8 and the upcoming Samsung Galaxy S5 are both boasting selective focus features for their camera apps, but with a 13 megapixel camera, the GS4 can take some pretty stellar pictures, too. To get that nice blurred background effect being showcased ...more
Applique is fabric cut in a fun shape that is applied like a patch, directly onto the fabric. This tutorial shows you how you can use fun woven print fabrics and fusible interfacing to create your own appliques and patches for your projects.