If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government. Last y ...more
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device. So if you've rece ...more
You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication b ...more
This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this. Thank You: First thank you for wanting to become a hacker, it is not an easy path. Becoming a hacker, at least in the way that I s ...more
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get famili ...more
Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype. What we are going to do today? 1 - get the IP from h ...more
So, how does someone keep their hacking life completely secret? What This Is: I'd like to know how hackers keep their hacking life secret. So with a bit of experience and knowledge obtained from elsewhere I want to share what I know, and also ask a few questions to become ev ...more
In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to ...more
Not to be outdone by the announcements of Mac OS X El Capitan and iOS 9, the Apple Watch is also getting a much needed software update. Some of the notable new features we can look forward to on watchOS 2 are Nightstand mode, additional screens for friends, email replies, and ...more
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedbac ...more
Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world! Advanced Per ...more
It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked thei ...more
If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company ha ...more
|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcas ...more
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta. The iOS 13.6 beta first appeared as an iOS 13.5.5 ...more
With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, thos ...more
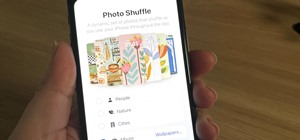
Smart home speakers, such as Google Home and Apple HomePod, are must-have accessories if you're trying to turn your home into a smart home. While HomePod is made to be used with the Apple ecosystem, the less-expensive Google Home can also be used with your iPhone — in more way ...more
The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If th ...more
The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an ...more
If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't us ...more
Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to ...more
If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your ...more
If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only the ...more
In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmles ...more
For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are sti ...more
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer. It's puzzling to imagine about 100,000 .onion websites in existence. Readers who ...more
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see t ...more
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few ...more
| Update: ZTE's issues with the US government have finally been resolved. Check out the details below. ZTE has a history of bumping heads with the US government. Multiple agencies have expressed distrust with the Chinese company and even discouraged Americans from using their ...more
Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial ...more
Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship. It wouldn't be an exaggeration to say the Nokia 9 PureView is the flagship device most Nokia fans have b ...more
Earlier this year, Nokia released the Nokia 8 Sirrocco overseas. The new device served as an upgrade to the 2017 model with a minor specs bump and a more modern design. However, HMD isn't done with the 8 series. A rumored Pro version is coming later this year that brings innov ...more
As expected, Apple began pushing out the final version of iOS 11.2.5 to all iPads, iPhone, and iPod touches today after 41 days of beta testing. Highlights include a fix for the ChaiOS vulnerability, a persistent Now Playing bar in Music, and some signs of AirPlay 2 just in ti ...more
IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple ...more
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 ...more
Shortly after we detailed several indicators that the Galaxy S8 Oreo Beta Program would begin rolling out in the month of November, we now have a full changelog for the update. Many users on Reddit already found references to the beta in the Samsung+ and Samsung Members app. ...more
A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) to ...more
Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission. This issue is a lot more common than you'd think. Most of us have seen the MTV show 'Catfish' or at least have heard of it. A pers ...more
LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader ...more
An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS. Thankfull ...more
Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device. Don't Miss: Turn Your Old Android i ...more
Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have over ...more
Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI. Although we would love to ...more
In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop b ...more
Google now has an iOS version of Android Wear, so if you own an Android smartwatch (Moto 360, ASUS ZenWatch, Huawei Watch, LG Watch Urbane, Sony SmartWatch, etc.), you can finally connect it with your iPhone. Previously, we covered a nifty hack that let you use an Android Wea ...more
Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way ...more
If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing ...more
Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't ge ...more
Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly al ...more
In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem. The Federal Communications Commiss ...more
Apple released iOS 12.3, the latest version iOS 12 for iPhone, on May 13. Great features to know about include Apple TV Channels such as HBO and Showtime that you can subscribe to in the TV app, support for audio, image, and video streaming to AirPlay 2-enabled TVs, and the ab ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a si ...more
With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone. Virtual Network Computing, be ...more
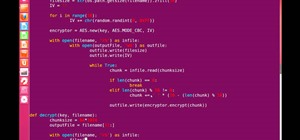
Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary fl ...more
Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect somet ...more
Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians acro ...more
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to se ...more
It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen ...more
One of Apple's most prominent iOS 16 features lets you unsend iMessages, but those aren't the only things you can take back. Your iPhone's Mail app also has the Undo Send feature, and unlike the Messages app, you can even customize the amount of time you have to stop an email ...more