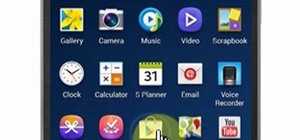
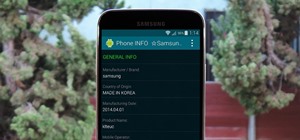
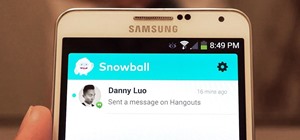
When you send an emoji from your Android device to someone that uses an iPhone, they don't see the same smiley that you do. And while there is a cross-platform standard for emojis, these don't work the same way as unicode-based smilies or dongers, so not every operating system ...more
Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. I ...more
Gotta catch 'em all, right? That's easier said than done, considering that Pokémon GO has region-specific characters that you may never get a chance to see. Sure, you can spoof your GPS location to make the augmented reality game think you're at a different spot on the map, bu ...more
Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff. Apple sells its smart trackers — small, circular white discs 1.26 ...more
As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those lookin ...more
Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is ...more
Pain is, for the most part, unavoidable when you stub your toe, break your arm, or cut your finger open. It's instantaneous and, in some cases, long-lasting, but it only feels as bad as you want it to. Yes, that's right—that pain is all in your head. Now I'm not saying that p ...more
SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. Tha ...more
So you've been using iOS 13 for a little while and noticed your iPhone is pretty slow to charge. Using the 5-watt power adapter out of the box, in the time it used to take your iPhone to charge its battery to 100 percent, your iPhone is stuck at 80% or below instead. That's be ...more
Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords in ...more
Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software b ...more
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan ...more
As we go about our daily grind, our smartphones and tablets take a silent beating. Dirt, dust, oil, and grime that our hands have picked up immediately gets transferred over to our shiny pocket-sized computers every time we check the time or look for new notifications, and ove ...more
SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most o ...more
The new Jelly Bean is out in the wild, but if you've installed Android 4.3 from stock, you'll notice rooting is now not possible. If you miss the ad-blocking capabilities of AdBlock Plus, how Seeder made apps snappier, or the convenience of backing up with Titanium Backup, you ...more
If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning e ...more
It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters t ...more
Ready to try and sew-in your own weave? It's a big decision. As with everything that concerns our hair, we struggle with the pros and cons and often dwell on what could go wrong. Pixie cut. Perm or not? New shade (of pink, purple, or blue). These are all major decisions becaus ...more
Emoji icons can vary greatly from manufacturer to manufacturer. Normally, this isn't be a problem, unless all of your friends use iPhones and you're the only one that receives a different icon than the rest of your group. And for the record, they don't all correspond to each o ...more
When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Appl ...more
Following in the iPhone X's footsteps, the iPhone XS and XS Max, as well as the iPhone XR, have all ditched the iconic Home button last seen on the iPhone 8 and 8 Plus, which is one giant leap toward Jony Ive's ultimate vision of an iPhone that's a clean slab of glass. However ...more
SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing ...more
White or light-colored dinnerware is a classic: it looks crisp, clean, and elegant. The only problem is that after you've used it for a few years, the surfaces bear a lot of grey scuff marks from forks, spoons, and knives being dragged across the surface. It's tempting to don ...more
Clash of Clans is one of the most successful games ever to come out for Android and iOS. It has been downloaded over 50 million times from Google Play alone, and shows no signs of decline. Part of its success is the constant need for players to sign in to avoid being raided a ...more
When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network w ...more
How many of you have or know people who have a smartphone? There's a lot of you, right? Well, depending on how most of you use those smartphones, there could be all kind of sensitive information stored on it, and that doesn't just mean sensitive personal information, but it co ...more
Rooting, bootloaders, custom ROMs, CyanogenMod, ClockworkMod... it's all pretty confusing, isn't it? You're not the only one having trouble with this. Many users in the Nexus 7 SoftModder forum have been scratching their heads at these many terms. First, let's cover the terms ...more
Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making cus ...more
Many midrange phones are being manufactured without a gyroscope sensor—the Moto X Play, third-generation Moto G, and several of Samsung's Galaxy Grand models, among others. It's not exactly an essential smartphone sensor, and leaving this out keeps the phone's price point down ...more
If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to ...more
Your smartphone stays with you everywhere you go, so it's only a matter of time before you spill coffee all over it or drop it on the ground. For some of you, it has already happened, perhaps even multiple times. That's why we thought it was important to find out which flagshi ...more
The new lock screen in iOS 10 is a lot different than previous versions, but one thing that stuck around is the quick access camera shortcut. The only real difference aside from aesthetics is that now you don't have to swipe up from the camera icon. Instead, you can simply swi ...more
Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy. Many beginners come here looking t ...more
Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world. The main draw of word games is that they're great f ...more
There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going t ...more
Apple's iMessage is one of the main reasons to use an iPhone, and there's a lot you can do in chats without being overly complicated. But there's one issue that continues to drive people nuts, and that's the blue typing bubble indicator with the moving ellipsis (•••). Can you ...more
I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still ...more
When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the in ...more
Having trouble getting a strong Wi-Fi signal on your Samsung Galaxy S3? Does the signal drop out on you when changing rooms? Frustrating, isn't it? GS3 SoftModder forum member Taral had the same problem, and asked about ways to increase the Wi-Fi range on his GS3. While there ...more
There are countless methods and cleaners aimed at eliminating stubborn stains from everything to clothing, carpet, and furniture. But completely removing every last trace of a stain doesn't require an arsenal of chemical cleaners and repeated cycles in the washing machine. Mos ...more
Sometimes you've got a head of lettuce that you want to eat but it lacks a certain youth. In other words, it's wilted and browning at the edges. Other times, you get to the grocery store near the end of day and the only lettuce or greens available look a little on the sad side ...more
When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving i ...more
Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal. And ...more
What do Hulu Plus, Pandora, and YouTube all have in common? Ads—and lots of them. Sometimes, an advertisement or two isn't a big deal, but when you're bombarded with them daily on your iPhone, they can get old really quick, and might even lead you to delete the apps entirely. ...more
You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and co ...more
I love making beeps and bloops with the Arduino pitches library, but sometimes archaic 8-bit tunes just don't cut it. Whether you want your robot to terrify your enemies with a demonic synthetic voice, you just need a pocket boom box on the go, or you want to a miniature guita ...more
It's one hell of a device, but the Samsung Galaxy S5 is still susceptible to the many hazards that other smartphones are prone to: theft, cracked screens, poor battery life, and particularly, overheating. If your Galaxy S5 is burning a hole in your pocket—and it's not from yo ...more
This past weekend's workshop on replacing normal levers with buttons masquerading as levers went really well. Lots of players showed up and everyone had a great time. Most importantly, everyone learned how to make and use a T flip-flop! Why bother with a T flip-flop? T flip- ...more
Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ...more
Back in 2007, YouTube user HouseholdHacker posted a parody video on how to make a high-def speaker for under a buck. MythBusters took on the challenge and busted it. Although that particular method doesn't seem to work, that doesn't mean you can't make your own speaker for le ...more
Knowing if your meat is cooked properly is both the difference between a delicious meal and an inedible one... and the difference between making your guests sick and keeping them safe. Yes, you can use a thermometer—but not everyone has a reliable gauge, and sometimes you may ...more
One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders. But it too ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve ...more
While there were a ton of features added in iOS 12, one that Apple had been bragging about since June was nowhere to be seen. Until now. With the iOS 12.1 update, your iPhone gets a huge feature, as well as a few smaller ones to boot. The iOS 12.1 update was released on Oct. ...more
Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people ar ...more
Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly ...more
We've already done a tutorial explaining why buttons are superior to levers, but now I want to show you a way to make them even more useful than they already are. You can't get this sort of functionality with levers! A button only emits a one-second (or so) pulse of power. We ...more
The passcode, or the four-digit code you enter in order to access an iPhone or iPod touch, was created to ensure security and prevent hacking. But what if you haven't touched your iPhone in a month and you simply don't remember what your passcode is anymore? Don't fret; just ...more
No matter how many camera improvements a phone adds, you're always better off using manual mode. Known as "Pro Mode" on the Galaxy S20, this feature can remove Samsung's pre- and post-processing from photos, putting you in total control. At first glance, manual mode is intimi ...more