Below, 10 step-by-step instructional videos for transforming yourself into a Na'vi being this Halloween. Step 1: Choose your favorite Avatar look from the list below. Step 2: Apply your chosen look. Step 3: For the dedicated fans with (more than a little) time on their hands, ...more
Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, t ...more
There are times when physically interacting with your iPhone is less than ideal, like when you're cooking or driving. Fortunately, iOS 13 has you covered regardless of the circumstance you may find yourself in. With the new Voice Control feature, you can control pretty much ev ...more
If you have a sunroof on your car, it's important that you regularly clean out the sunroof drains. Not doing so will result in a wet, stinky interior that can lead to a hefty repair bill. Checking and cleaning out the sunroof drain isn't a very hard task and can take up to 15 ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
You just sat down, coffee in hand, and the day is ready to start. Now that you have taken a few sips, let me pose a question: What is living in that coffeemaker of yours? The answer might make you dump that coffee down the drain pronto. Extremophiles are rugged microbial indi ...more
Do you know how to pick a lock? If you do, you know that sometimes a little lubricant can do the trick. This video tutorial will show you how to make homemade graphite powder for lock picking. Graphite powder is the preferred lock lubricant of professional locksmiths, so you ...more
If you're lucky enough to have a dishwasher, you probably use that sucker to clean everything (minus your good cooking knives), and maybe even to cook your food, too. However, dishwashers are not without their faults. Dishes can still come out spotty and even with chunks of fo ...more
The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the ...more
Cheat and hack Castle Age on Facebook! Castle Age is a new fantasy flash game where you conquer the world with your army of mythical beings. Watch this video tutorial to learn how to get the Castle Age friend add and invite link (11/17/09). A simple way to get the Friend Add a ...more
Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best ...more
Wondering how to get long hair naturally? How do you grow your hair? In this video Rachelle and Sam give you 10 tips to get those long locks naturally! Video: . Step 1: Practice Good Hair Habits Daily treatment to your hair; Don't brush it too hard; Harsh chemicals; and High ...more
Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecur ...more
On its quest for online domination, Amazon.com continues to expand past its basic web marketplace to fulfill the needs of everyone and anyone with a little cash to spend. First, they battled the likes of Barnes & Noble and Borders Books with their online Kindle eBook shop. Ne ...more
In this Photoshop tutorial video from Tasktutorial, the host leads you through the process of creating a speech bubble in Photoshop. As you watch this video and follow along with the host, you will learn how to create a speech bubble, like they use in the comics. You will also ...more
Now that the cutting-edge iPhone X is up for preorder, everyone is excited to see how the new device will compare to offerings from Apple's competitors. Namely the Galaxy Note 8, which is a beast of a phone in its own right. The reasoning behind wanting to see how the iPhone ...more
Here's a weekly on-line Modern Jive dance lesson from Dance Yourself Dizzy. This is a two part step by step from the man's perspective showing the steps in lead during basic modern jive dancing. Jive is a style of swing. Part 1 of 2 - How to Dance modern jive. Part 2 of 2 - H ...more
Have you ever heard someone else's iPhone ringing and thought it was yours? Of course you did. iPhone ringtones are iconic, but not varied. If you're using one of the more popular iOS sounds, you'll likely encounter it in the wild multiple times. Why bother, when you can creat ...more
Every year, Apple releases a new version of iOS. Each iteration promises new features to make using your iPhone that much better. This year, iOS 13 introduces over 200 new features and changes, including system-wide Dark Mode for the first time on iPhone. That said, you might ...more
During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the ...more
Apple dropped the sixth public beta for iOS 13 today, Aug. 15. This public update comes just hours after the release of developer beta 7, an interesting move for Apple. The company has recently stuck to a schedule of seeding the public beta at least one day after the developer ...more
Parents rejoice, Apple Pay is making it much simpler for your kid to use Greenlight, the MasterCard for kids app. The goal of Greenlight is to prepare kids for the world of financial independence while making it as safe as possible for them. Parents are able to monitor and co ...more
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and u ...more
Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely da ...more
Whether you loved or hated the blockbuster hit Joker for its slapdash violence and unflattering portrayal of mental illness, if you have been online lately, you know you can't afford to miss it. If you are in the former camp, you can now show your appreciation using a new fil ...more
When purchasing a new phone, one of the most vital features to consider is battery life. Everyone wants to know how long they can use their device without needing to hug a wall. Increasingly, more and more manufacturers ship their devices with some variation of a "battery savi ...more
First things first, gals: NEVER, EVER use a nail clipper to clip off your cuticles. You may think clipping your cuticles off is a quick and easy way to get rid of your cuticles before a manicure, but doing so is highly dangerous because it can lead to infection and tearing. T ...more
Want to play lead guitar in a rock band? Well first you have to learn techniques from the masters. This guitar lesson from Siggi Mertens teaches you how to play a ohn Lee Hooker style blues riff. There are similar blues riffs to this John Lee Hooker riff. "Boom, Boom" or "Suzi ...more
Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are ...more
The big fireworks day is almost here, but most of you are limited in what you can do when it comes to celebrating the Fourth of July with a bang. Unless you live in a dry area prone to wildfires, one type of fireworks you can probably still legally buy are sparklers. But why ...more
I loved the Gold Rush unit back in third grade. We went up to the American River and panned for gold, and my panning skills balled above all. I got like three tiny pellets. Of course, it was all fool's gold, aka pyrite, but it was still pretty legit. And this was before wearin ...more
The Halloween update from Notch added many amazing features to the game including Biomes, and more! One of the more prominent, game changing additions were Gateways that lead you straight into Hell. Every step you take in Hell is equal to 16 steps in the outside world. The way ...more
If you just purchased an Android enable mobile device with Bluetooth, then one of the main objectives you'll have on your to-do list is to set it up in your vehicle for hands-free dialing and phone calls. Activating Bluetooth inside your car is easy, and all you need to rememb ...more
Staying inside during the coronavirus pandemic isn't easy for most of us. As important as it is to keep away from others, it can be challenging to keep to ourselves day after day. That's why mobile game developers are stepping in to help; many are making their games free for a ...more
Cloud drawing is a snap, and it's a great place to learn how to smudge your pencil lead when you are drawing. Step 1 - The cloud shape Create your shape using circular motions to define the outline. If you're having problems getting nice circles, go get a compass and use that ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead t ...more
Andre Geim and Konstantin Novoselov, from the University of Manchester, have just won the Nobel Prize in physics from their work with graphene. They've found a way to isolate graphene from graphite (carbon in pencil lead) and distinguish its behavior, which holds extreme poten ...more
Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help ...more
It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released D ...more
Though they share the same name, the HTC One and OnePlus One have completely different sound quality. HTC had put a lot of time and effort into fine-tuning their BoomSound technology, while OnePlus is still fairly new to the game, with brand recognition being a much greater ob ...more
A deck of cards may be a magician's best way to demonstrate his or her's sleight of hand, but for the prankster, it's the perfect way to deliver a shocking 300 volts of electricity! And that's exactly what I'm going to show you how to do today. Stuart Edge used it in his "Elec ...more
Inspiration for tutorial: Foxtrot's "How to Trap a Tracker" If you have been following my past tutorials, (and it's fine if you haven't,) you would know how much social engineering and doxing I do. During these moments when we are convincing people that we are a different per ...more
Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate. While smartphones continue to improve and push the limits ...more
If cameras are a priority, one of the first specs to check on a new phone is the image stabilization. You've probably been told optical image stabilization (OIS) reigns supreme, but this isn't the case if you're taking a lot of videos. Instead, we would argue, electronic image ...more
Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer. Any stone block can be replaced with blocks of your choice. Mycelium is used in ...more
Watch to learn how to replace knobs and buttons on a Neff oven. You'll remove and replace the knobs and buttons on a Neff oven. Lost oven knobs or worn oven buttons detract from the ovens appearance. eSpares videos show you how to fit common spare parts and accessories into y ...more
Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, t ...more
No doubt, you've heard a lot about 5G lately. This might have you looking at your current 4G phone and lamenting your inability to connect to the faster network. But is 5G worth buying a new phone over, and should you buy one right now? There are plenty of reasons why 5G is g ...more
Pinning a tweet to your profile is a fantastic way to get people to view and engage with your most important content on Twitter. In fact, it could very well be the best way to improve your overall Twitter strategy. Think about it: Every time someone visits your profile page, ...more
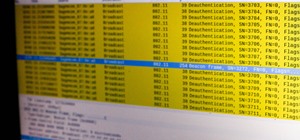
Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it i ...more
Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up f ...more
A small scrape or spot on your car where the paint has been removed can hurt the value of your car and lead to rust. This step-by-step video will walk you through touching up the paint on your car in a safe and easy way. Take a look at how they manage to repair the scrape in t ...more
Life's pretty good for iOS public testers — we get to check out new iPhone features months before the general public even knows they exist. That said, we aren't first to the party. Developers get priority during beta testing, as evidenced by yesterday's iOS 13 dev beta 6 relea ...more
Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able ...more
Unlike VR, when you're talking about augmented reality, describing what an experience is like can be incredibly difficult — primarily because the experiences are even more contextual than relatively static virtual worlds that don't involve real-world settings. In AR, everythi ...more
Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access ...more
As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid fo ...more
Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre ...more
Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. M ...more
Learn how to do cheerleading stunts and routines in this free video series from a national cheer leading champion. Part 1 of 18 - How to Do basic moves for cheerleading routines. Do basic moves for cheerleading routines - Part 2 of 18. Click through to watch this video on expe ...more