Night People: A Bad Vibes Label Profile Shawn Reed is one of our favorite people, not content with making music with Wet Hair, he also runs 'Night People' - an almost complete DIY record and tape label operation in Iowa - a label which has consistently put out and introduced ...more
It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to interce ...more
Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA ha ...more
Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to in ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
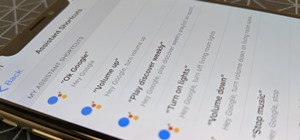
One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messagi ...more
Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let ...more
With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world. As th ...more
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll ...more
For our final part of recognizing crowd control, we shall look at the mind. It's the most complicated thing in the universe, but also the most easily influenced. What makes us to gullible? What methods to commercials, companies and the media use to influence our position on th ...more
Are you a PC user who's made the switch to Mac but you miss the Windows O.S? Maybe you're a Mac user looking for a more savy experience? The Lab Rats, Andy Walker and Sean Carruthers, will show you how to run Windows or Linux on your Mac.
Made the upgrade from Windows XP to Vista, but you're having troulbe with some of your old programs? The Lab Rats, Andy Walker and Sean Carruthers, teach you some software troubleshooting tips for Windows Vista.
BURKITE n pl. -S a burker 63 points (13 points without the bingo) There's no better time than Halloween to have the BEJABERS scared out of you, and no better way than with a slasher flick or horror movie about HEXEREI. To some, Halloween is a time for candy, costumes and cel ...more
There's only a few week left until costumes and candy take over the streets, which means they'll be more and more seven-letter words in the Scrabble Bingo of the Days that relate to the Fall season, horror movies, and of course… Halloween. Below you'll find bingo words relevan ...more
See how to make a figure four deadfall trap. This is a great survival trap that can be easily constructed (with practice) out of very basic materials that in most environments can be easily found. The trap can also be made with very limited, or primative tools. This trap is a ...more
Homemade circuits are amazing. You can build any kind of circuit on a simple perfboard, as we have seen in previous projects. However, some projects require very tiny circuit boards. We could special order some boards from a printed circuit board (PCB) factory, but that will m ...more
Ball Pythons have become big business in the pet trade industry over the years, due to them being one of the most docile snakes in the constrictor family usually preferring to roll into a tight ball hiding it's head than to striking out with the intent to bite. These snakes co ...more
APOLOGIZE Hello my masters and colleagues, first of all I would like to apologize for my absence during the past month, to say that i was busy with some projects and decide to leave the white-side for a while and made some visits on the dark-side(every good COP has a dealer f ...more
Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria. There ar ...more
No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it. Yet even the smallest, most normal behaviors in our day-to-d ...more
I grew up in a household where bacon was considered its own necessary food group. My mom saved the bacon fat in a jar and reused it in other dishes, which my friends considered vile, unless they were also from immigrant families or the American South, where saving bacon fat ha ...more
Avian flu is making the news again with new human cases in China reported in January. What does "avian flu" mean to you—and how dangerous is it? Each year you, or someone you know, probably gets a flu shot. The seasonal flu shot changes each year to reflect circulating influe ...more
Not So Humble Pie, creator of yummy cookie lab rats, chocolate atoms and gingerbread scientists (to name a few), brings us a delectable contribution to the world of cake decorating: the candied bacon cake. This cake looks like bacon, and actually tastes a little bit like bacon ...more
With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Pyth ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fightin ...more
So, it's Halloween time, and you feel like playing around with some augmented reality apps? Well, you've come to the right place — if you have an iOS device. Sure, you could load up some Halloween-themed filters on Snapchat (like the new lens sponsored by Stranger Things 2) a ...more
Even if your cat drives you a little nuts, don't worry, because a new study says that cats pose no risk to your mental health. Media reports in the last couple of years placed emphasis on the danger of your cat to your future mental health, and that of your children. No kiddi ...more
So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one. Native to North America, you can find raccoons just about everywhere except for parts of the Rocky Mount ...more
While it is easy to create and maintain your compost pile, you can enjoy it more knowing a few basic tips. International Compost Awareness Week (ICAW) is May 7 through May 13, 2017. First launched in 1995, ICAW is a great opportunity to share enthusiasm and awareness of the b ...more
A sometimes serious disease spread by fleas is making inroads in Texas, quietly doubling case numbers since 2008, and beginning to encroach on larger metropolitan areas. While considered a nuisance on cats and dogs, fleas have spread disease around the world, including plague ...more
Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detec ...more
It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography. In this article, I will ...more