Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now. From what I can tell, it's a very safe a secure method keeping passwords, links, and personal stuff encrypted and online. TURTL https://turtl.it Turtl is ...more
The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are light ...more
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manuf ...more
For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list. There are a lot of tools out there for creating fake access po ...more
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance tha ...more
Apple released iOS 17.4 on March 5 with over 30 new features, but now it's iOS 17.5's turn for the spotlight. The update, currently in beta, gives us a few interesting updates and changes for iPhone, including a new word game, and there's even a sneak peek at what could be com ...more
Apple said goodbye to iTunes with the release of macOS Catalina, breaking up music, videos, and podcasts into their own respective apps, Music, TV, and Podcasts. But without iTunes, what app's in charge of interfacing with your iPhone? That would be Finder, and you use it to s ...more
Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System ...more
I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff. So, I figured it was time to add some Bond to my daily life by beefing up on my data deletion know-how, ...more
There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your comput ...more
If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely. Even if nothing is w ...more
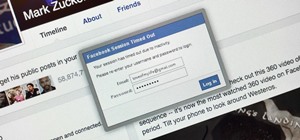
Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily act ...more
Since the new Mac OS X 10.11 El Capitan is brand new, I recommend installing it on a separate partition on your hard drive. This will keep your current Yosemite system safe from harm, and will let you easily switch back to it should El Capitan become unusable for any reason. ...more
In iOS 11, Apple made it easier for you to share passwords with friends. Back then, it was just Wi-Fi passwords, which made sense. "What's the Wi-Fi?" gets old after a while. But now, whether you're running iOS 12 or 13, you can share any password you want with any iPhone arou ...more
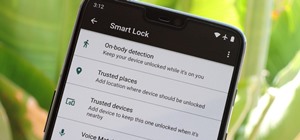
Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions. Sometimes privacy and securit ...more
Every time you log in to a website in Safari on iOS, you're also asked if you would like to save the username and password—a great feature of just about all browsers that makes it so that don't have to enter your credentials each time you access website in the future. While th ...more
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physi ...more
Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less ...more
After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimiz ...more
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's eas ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
Apple's password manager, iCloud Keychain, lets you securely save important login credentials for apps, websites, and services that sync up across all of your Apple devices — iPhone, iPad, iPod touch, and Mac. One of its biggest highlights is that it can create strong password ...more
Windows is a mess sometimes, full of problems. And your password just might be the biggest problem of all, if you've lost it, of course. What should you do when you forget the password to login to Windows system? Ask an administrator to reset the log on password for you. If y ...more
First things first: You can't actually recover a Joomla administrator password. That's because Joomla uses a one-way MD5 hash that prevents you from doing so. However, it is possible to reset your password. We all have our brain fart days, so for those when your password comp ...more
Gary Rosenzweig from MacMost looks at one method to protect a set of files with a password on a Mac. It involves using Disk Utility to create an encrypted disk image.
When Windows stores a password, it is done so by hashing the password in an LM hash and putting it in the Windows SAM file. In the scary moment that you lose your password, but don't want to pay some geek to have full root access to your computer, you need to recover it using ...more
Uh oh, you've forgotten your AT&T Online Account Management password! No worries, this simple guide shows you how to regain access to the site and reset a new password. Your AT&T Online Account Management portal is vital to keeping your information up to date, so make sure you ...more
Forget the password to your Win 7 PC? Recording it is easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over six minutes. For more information, including step-by-step instructions, take a look.
Want to find out a forgotten password on a Windows PC? This clip will teach you everything you'll need to know. With MailPassview, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over ...more
A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is s ...more
Watch this video for a helpful tip on how to use secret folder application and protect folders in your MAC PC by hiding it. you could download secret folder application from version tracker.com for free go to the Website and click download button to download the application on ...more
Password protect your files and folders in Mac OS X. This free video tutorial from CNET TV will show you how. Thwart would-be snoopers with this home cryptography guide, which presents easy-to-follow, step-by-step instructions on how to protect your privacy by encrypting your ...more
In this tutorial, we learn how to password protect your folders on a Mac computer. First, use the spotlight tool to type in "disk" and then click on disk utility on the drop down menu. From here, go to the save as menu and enter in the name for the volume. After this, change t ...more
In this tutorial, we learn how to password protect a folder in Snow Leopard on your Mac. First, go to the finder and click on "utilities". Now go to "file, new, disk image from folder". Now, you can select the folder you want and then click "image". Make it a read/write folder ...more
Whether you want to edit photos, compress files, play games, or DJ your next party, there's a free Mac app that can help you out. But things can get annoying real fast if you download a lot of free apps from the Mac App Store, since you have to type in your Apple ID password e ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vul ...more
More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered. Passwords are normally ...more
One thing that makes Apple great is the connectivity between its products. Many tasks you do on an iPhone can be switched over to a Mac or iPad quickly and easily. The Notes app is no exception to this advantage, but you need to make sure you're set up so that your notes sync ...more
Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication f ...more
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processin ...more
Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of ...more
I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After ...more
The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job. There are paid services th ...more
While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the ha ...more
Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics seri ...more
Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But w ...more
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB d ...more
Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to k ...more
If you use the Notes app on your iPhone and haven't updated to the newest software yet, you're missing out on some pretty valuable upgrades that improve smart folders, note security, collaboration, and more. So what are you waiting for? The new tools in Apple's Notes update m ...more
Have you ever been locked out of your iPhone? Maybe you forgot your passcode. Or perhaps someone with access changed the passcode as a prank. Your iPhone's display could have even been damaged and unresponsive. Whatever the reason, there's an easy way to get back access to you ...more
It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default ...more
While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show y ...more
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?" As the hacker is among the most skilled information technology disciplines, it requires a wide knowledge of IT technologies and techniques. To truly be a great h ...more
Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some ...more
Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered ...more
Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone. Th ...more
The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just rel ...more
On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's ...more
Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians acro ...more