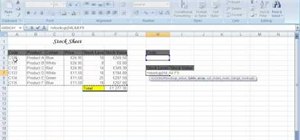
In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenari ...more
With over 20 million songs, Spotify has become my go-to source for music. I can stream tunes to my desktop or phone, without ever having to worry about storage space being eaten up. One key difference between the desktop and mobile version that really bugs me is the lack of o ...more
There are a ton of great mods and tweaks available in Cydia, but occasionally there will be one you want to install that hasn't quite made it into one of the main repositories yet. If you're not patient, it can be still be installed by manually placing the .deb file directly o ...more
To bring things up to code with a new FCC standard, Android recently added an "Emergency broadcasts" feature that will make your smartphone notify you whenever a potential safety threat or Amber Alert is posted in your area. Even if you have your phone set to silent, these eme ...more
In an attempt to keep things simple, Snapchat has a limited amount of editing features, made up of "smart" photo filters, drawing pens, and special text captions. If you want more editing capabilities, you'll be pleased to know there's a way, no thanks to Snapchat, but you wil ...more
Welcome back, my budding hackers! If we are considering a social engineering attack against a target, we are probably going to need email addresses. By having the email addresses of people within an organization, we can tailor our social engineering attack to particular peopl ...more
Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how ...more
A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data. The ...more
A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge. The goal in this article is to acquire a target's .plist file which contains the ...more
For most Android phones, the system clock is set using a protocol called NITZ, which relies on a connection with your carrier to ensure that the time stays in sync. The trouble here is that this feature won't work when you're outside of cellular range, and a lot of times, the ...more
The Google Play Store exists so you can download as many apps as your heart desires (and as your memory can hold). Sure, you may only use them once, but it's your choice—and isn't that what life is really about? With that said, the Samsung Galaxy Note 2 already comes with a to ...more
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones ...more
In a previous softModder tutorial, we installed CyanogenMod on our HTC Ones to approximate the look and feel of the Google Edition HTC One. Unfortunately, this rendered Beats and HTC's ImageChip (among other things) useless. This is no longer an issue, though, thanks to Andro ...more
YouTube is a great place for all your mainstream audio and video needs. But you can't simply plug in your headphones, choose a playlist, and put your phone back in your pocket without subscribing to YouTube Red, which costs $9.99/month for ad-free and background playback. If y ...more
Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot ...more
Navigating through the darkness—literal darkness, not the existential variety—is always a difficult task on its own, and my Android doesn't necessarily make it any easier. Many manufacturers offer quick access to a flashlight or torch feature, but my Galaxy S4 doesn't have an ...more
One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device. A recent guide on adding softkeys to the GS3 from mod Faisal inspired me to share some information on how to edit build.prop, which is y ...more
It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or ...more
Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali! Okay, it may be a potential skiddie toy, bu ...more
Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to activ ...more
Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, ...more
The Calculator app is probably one of Apple's most-used iPhone apps, yet I always meet people who don't know all the little tricks there are to using it more efficiently. You may know most of them, but there's a chance you don't or at least forget about some of them. What a " ...more
There are at least 24,000 different Android devices, and they all have varying hardware components. This is why many developers publish several unique variants of their apps, which, among other things, helps accommodate all of the different display sizes and resolutions on And ...more
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs. Installing custom ROMs is performed with a special type of software call ...more
While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a fe ...more
While it's easy enough to take a screenshot of an end-to-end encrypted Telegram chat thread using an iPhone, it's an entirely different story on Android phones. Telegram disables screenshots for Secret Chats by default on Android, and not everyone can turn it on. Sometime in ...more
If the Nexus 7 wasn't your first Android tablet, you may have noticed something different with the user interface when compared to other Jelly Bean tablets. You may not know exactly what it is off the top of your head, but it's there. Phone mode. Yep, your Nexus 7 utilizes t ...more
The volume buttons on the side of most Android devices—also known as the volume rocker—make it easy to adjust sound output without having to dig around in any settings menus. But the trouble is, they control notification and ringtone volume by default, and will only adjust med ...more
I've been a Sprint customer for a long time. Normally, Sprint (flagship) phones come with some useful apps, such as Sprint TV, Sprint Zone (for payments, updating PRLs, and account information), and NBA Game Time. In other words, relatively free of bloat. However, our AT&T HT ...more
There's no debating that the Galaxy S8 and S8+ are top contenders for the most beautifully designed handsets of 2017, but the same can't be said for their TouchWiz interface, which has been met with lukewarm reception at best. Changing the UI by flashing a custom ROM has alwa ...more
While LG G3 users have been patiently waiting, developer the cubed and his Codefire team have been diligently working on a successful unlock method for the heavily locked-down bootloader. Now it's finally here, and the unlocking method is extremely easy to do—and it works for ...more
If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's ...more
While Snapchat's latest update brought messaging and video chatting, it also ruined something for us softModders—KeepChat. With KeepChat, we were able to save pictures and videos sent to us without the other person being notified. It was pretty slick, and I was beginning to mi ...more
Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe fro ...more
There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because: The free tables are suitable for almost all uses (I've neve ...more
There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various oth ...more
Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have alread ...more
Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking. Luckily for those o ...more
Google's long awaited 4.3 Jelly Bean update is officially out, only it has not been pushed out to some of our Nexus 7 tablets yet. Although there aren't really any new UI changes, most of Jelly Bean 4.3's magic is under the hood, meaning user's can expect better performance an ...more
Amongst the many rumors emerging about the upcoming Samsung Galaxy S4, one that seems like a fairly sure bet is the inclusion of Google's Photo Sphere feature. Renamed to Samsung Orb, this amazing camera tool that first surfaced at the release of Android 4.2 will be integrate ...more
Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpr ...more
The Galaxy S6 won't hit shelves until later this spring, but that didn't stop the Android community from working its magic and pulling a handful of apps from the device's stock firmware. Several of these apps rely on framework elements that aren't present on current-generation ...more
One of the golden rules to cooking a Thanksgiving turkey is to place it on a roasting rack before it goes into the oven. Missing this step and cooking it directly on the pan will burn the bottom of the bird, resulting in overcooked, dry meat. Don't Miss: Unlock Your Oven's Se ...more
Despite packing some really nice camera specs, the OnePlus 3 and 3T don't take the best pictures. That's because, these days, great software is just as important as great hardware when it comes to image quality. Qualcomm, who made the processors for the OnePlus 3 and 3T, has ...more
When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android ...more
As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer. While smaller carriers like Sprint or T-Mobile are happy to just have t ...more
Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and ...more
App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated. ...more
If you're a rooted user, you've probably heard the term "BusyBox" by now. Many mods require these powerful root commands, but the process of installing BusyBox can be a bit confusing for the uninitiated. To clarify things a bit, BusyBox is both an app and a set of specialized ...more
What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break? But leaving your phone at home or in the office when you go out is absurd, I mean, everyone b ...more
Dark mode is finally rolling out for Gmail on Android. But this is a Google product, so you already know it'll be a while before the server-side update hits most devices. Sideloading the newest APK doesn't work, neither does switching accounts. But if you're rooted, you can en ...more
Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds. These banners are what the ...more
When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher. Recently, Go ...more
WhatsApp is a very popular messaging app on the Play Store, but unfortunately, tablet users have been left out of all the fun because WhatsApp only works on smartphones—until now. Tech wiz James Nakata wrote up a short guide over in our forum for porting WhatsApp onto a Nexus ...more
Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here. It seems like every week there is a new exposé revealing all of the backr ...more
The Galaxy S8 and S8+ come with a set of AKG-tuned earbuds that would cost you $99 by themselves. Unfortunately, the earbuds alone don't automatically translate to superior sound, and they've been met with lukewarm reception. But as it turns out, there's a fairly hidden menu o ...more
Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any ...more
PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers. Because PRLs only operate on CDMA networks, this method only appl ...more
At night, no matter how dim my Android's screen gets, it never seems to be enough—especially when I'm in bed. In fact, in pure darkness, the lowest brightness setting on my Android devices end up giving me a headache that keeps me up for hours. But there are ways to make an A ...more
It happens to everyone: you set a lock screen password in a hurry and cannot remember it the next day. To unlock your device again, you need to reset the password (or PIN, pattern, etc). There are two official methods of doing this. #1. Reset Your Lock Screen (Patterns Only) ...more