You can't beat Samsung's hardware, but their software still isn't for everyone. That's the thing, though — software can be replaced. So if you're more a fan of Google's vision for Android, but you can't get enough of Samsung's beautiful screens and build quality, you're just 1 ...more
INTRODUCTION Hello dear null_byters here we go again with our third part of this serie. in this third part of our series I'd like to do a demonstration or continuation on fuzzing, but I think I should leave for later because the next tutorials about fuzzing will require from ...more
Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience. OnePlus offers its O ...more
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago. It's name is Pyxiewps and uses pixiewps, reaver and airodump to retrieve the WPA password in at least 9 secods! (Best case scenario) It takes advantage of the pixie-dust v ...more
Have you ever noticed that some Android gallery apps display every last photo that you have stored on your device? This is particularly annoying when most stock gallery apps don't provide an option for hiding certain folders from your filmstrip view. Then there are music playe ...more
You don't need to be a hardcore audiophile to know that Dolby is pretty much synonymous with rich and immersive sound. While we often associate them with home theater systems, Dolby has brought their surround sound processing to the mobile phone arena with Dolby Digital Plus b ...more
One of the main reasons why the Samsung Galaxy S III has dethroned Apple's iPhone 4S as the best-selling smartphone in the world is due to Android's open-source operating system. The vast spectrum of customization that comes with Android has become one of its focal points, all ...more
Earlier this year, Google rolled out the first developer preview build of Android O. The new version added tons of cool features, but the downside was the fact that you needed to use Fastboot to manually install the update if you wanted to try it out. Thankfully, things just g ...more
When having a large dinner party or family gathering, having a coffee station set up saves the Host/hostess a lot of busy work. Guests like getting their own beverages rather than having to ask for one, and the coffee station is the key solution. Plus, one can serve several ki ...more
Back when 4.1 Jelly Bean came out (boy, how time flies), Android introduced expandable notifications. Depending on the notification, a simple swipe down with your finger could expand it and show extra content, like Delete and Reply buttons for Gmail messages. If you have mult ...more
Over the past several weeks, I’ve had the pleasure of test driving Samsung’s next big thing, the Galaxy S4. After putting the GS4 through its paces, I have a clear picture of what this device is capable of. I’ve covered the features of the device before, and now I’ll tell you ...more
Contrary to what you may think, clearing or swiping away apps in the Recent Apps view on your Android device does not necessarily stop app activity or running tasks—and these running processes can actually be eating away at your battery life. Depending on the app or process, i ...more
Every morning I walk out the door with my headphones plugged in and music blaring. While it's not be the most difficult thing in the world, unlocking my phone and starting my music manually every time feels like a hassle. Pressing play on my headphone's remote will auto-start ...more
The idea of squeezing your phone might have sounded a bit out there when it was new, but it's now a hallmark feature on Pixel devices. As useful as it is for summoning the Google Assistant, however, it certainly would be nice to be able pick and choose what action is triggered ...more
Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves b ...more
Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your ph ...more
OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time- ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
Google recently started testing a new SafetyNet check that might spell trouble for rooted Android devices. It cross-checks your SafetyNet status with Google remote servers, making it impossible to fool by normal means. If Magisk shows you pass SafetyNet and you're still having ...more
I'm a notification minimalist. When I get alerts, I want to deal with them ASAP. If the time is not right and I want to reference the notification later, snoozing was always the best course of action. But in Android 10, Google tucked away snoozing, so here's how to get it back ...more
Some of us root for the villain when you're watching even the sweetest movie, like Disney's Sleeping Beauty. For girls, or boys in drag, that don't want to look like a princess, this how-to video demonstrates a makeup look that evokes Maleficent, the witch from Sleeping Beauty ...more
If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out. Let's say there's a router that we need to know the password for, and we have physica ...more
One of the standout features of the OnePlus 7 Pro is the 90 Hz display. A higher refresh rate means smoother gameplay for all your favorite games, which is precisely what you'd want out of your gaming experience. However, not all games play nicely with these higher refresh rat ...more
Smartphone displays are getting bigger every year, and Samsung devices are at the forefront of that trend. But, from a software standpoint, the icons, buttons, and other on-screen elements seem to stay at the same scale. So while phones are getting bigger, their interfaces are ...more
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest brow ...more
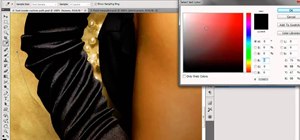
Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even ...more
TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding ...more
Android is all about the fine details. You can make a little tweak here and a little tweak there and completely customize your experience to be exactly how you want it to be. Sure, you don't need to customize LED colors or screen record, but it's nice to know you can. Today, ...more
Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP) and windows's inbuilt Task Scheduler. Meanings... Task Scheduler: It is a program, inbuilt in windows, which allows us to create some tasks and execute them at s ...more
As carriers finalize their variations of the Android 4.4.4 update, we're left with only brief glimpses of what the new "Eye Experience" holds in store for us while we wait. However, thanks to a system dump of an updated European HTC One M8 and some clever hackery by donmarkoni ...more
You will need 2 packs of kanekalon hair extensions, gel, for a firmer hold. You will also need clips to get the hair out of the way and a comb to make straight lines. A lighter is also used, to seal the ends. You first want to separate the air into sections. Put a little bit o ...more
The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere ...more
Does your Samsung Galaxy Note 3 feel slower than it used to? Background processes, cached files, malicious applications, and buggy updates can all lead to a sluggish smartphone. It's just what happens over time. However, with just a few simple adjustments, you can significant ...more
I like being fast at everything (well, almost everything), and I expect no less from my smartphone. So when I'm using an app on my Samsung Galaxy S3 that takes up the full display, I don't want to swipe down twice to get to my notifications—I want to swipe down once. The Slow ...more
As much as I love my Samsung Galaxy S3, I'm always on the lookout for cool features I can borrow from other smartphones. One of the most recent "borrowed" features I've added to my S3 is the Galaxy Note 2's smart rotation feature, which uses the front camera to detect my face- ...more
A great aspect of using Android is having the ability to change and tweak aspects of the user experience to your liking. You can easily change things like home screens, widgets, and icons on your Nexus 7 tablet, but also core system settings if you want, like volume settings. ...more
Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored compute ...more
The Nexus 5 and Nexus 7 (2013 edition) boast beautiful 1080p screens that are capable of displaying images and videos in ultra-sharp high definition. But for some strange reason, the YouTube app only allows for streaming of 720p content on these devices. It's not a limitation ...more
If you enjoy modding your Android device with root utilities, custom ROMs, and Xposed modules, then there's a good chance you've had to factory reset your phone when something went awry. Plus, when you're switching ROMs, it's always recommended that you wipe all data, so us mo ...more
Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new ...more
Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to id ...more
Sense 6 came with a ton of new features for the HTC One, but for some reason, HTC decided to keep one of them hidden to all non-Harman Kardon editions. Music Channel is a music visualizer that can also link into the GraceNote music catalog and display lyrics for any compatibl ...more
When it comes to blocking unwanted calls, your Android device comes stocked with a native blocking feature that allows you to reject certain phone numbers. That being said, the native blocking feature on the Samsung Galaxy Note 3 isn't the prettiest or the smartest, with its n ...more
While the Galaxy Note 3 and Galaxy S4 are enjoying their official KitKat updates, those of us with Note 2s are left to play the waiting game. While we know our devices will eventually see an update to Android 4.4.2 KitKat, it's unclear when an official update for our devices w ...more
In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the ...more
It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find ...more
In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmles ...more
If you're not acquainted with 500px, you should be. One of the more preeminent photography communities out there, 500px takes you through a journey of incredible shots—anything from nature and urban explorations to cities and architecture to the abstract. Whatever your prefere ...more
There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and adv ...more
Buried deep in the code of many Google apps is a set of debugging options. These options, which are designed for developers to help test the way their apps interact with Google's own, are normally hidden from view. Every now and then, new and upcoming features are hidden in h ...more
This video demonstrates a tutorial on how you can volumize your hair using flat iron. It is very easy and quick to straighten your hair; it will take only an additional 2 minutes or so. First thing to do before adding any heat to your hair is a heat protectant which is under ...more
The OnePlus 5 just made its official debut, so we now have all of the juicy details. From the announcement, this device definitely sounds like it's going to be another flagship killer, following in the footsteps of its predecessors. Right off the bat, the OnePlus 5 challenges ...more
It's nice having a dark theme on Android 10 and One UI 2, but setting it on a schedule takes it a step further. Imagine the light theme turning on every morning, and the dark theme taking over after sunset — all automatically. It sounds pretty simple, but it's one of those thi ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! Computer forensics ( Sometimes known as computer forensic science ) is a branch of digital forensic science pertaining to legal evidence found in computers ...more
With the purchase of my latest computer, installing Linux turned into a nightmare from Hell. The graphics drivers are probably the biggest issue that anyone with a newer computer will run into when installing Linux. AMD and NVIDIA are the dominant ones on the market, both of w ...more
The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnera ...more
On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices. If you're one who likes to stay on the cutting edge, this build offers lots ...more
What is a Data Structure? When we think of a "structure" we often think of architecture, but data also often has structure. There are many different types of data structures: arrays, graphs, queues, stacks, and so on. We use these structures in order to be able to effectively ...more
If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh R ...more
When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we'r ...more