Hi guys. Hope you all had a good Christmas , today i have a tutorial for you. If you brick you device it's not my fault I will show you how to build the new version of NetHunter and install it to your device(must be a supported device,,see the list below) Nexus 4(mako) Nexu ...more
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be. Having your phone stolen used to be the end o ...more
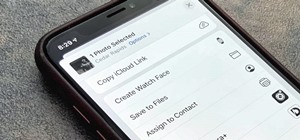
If you haven't noticed yet, there are a lot of new features hiding in your iPhone's Messages app, and some of them are things users have been requesting for a long time. While iMessage is getting a lot of attention by letting us edit and unsend messages, it's only just the sta ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. We're back again for another Pre-release! This time around it's 1.9 Version 4. Notch released version 4 today saying, "...instead of trying to squeeze in another real release, we’r ...more
The new Moto X may not have a lot going for it when it comes to hardware, but there are some pretty cool software features that makes it a tempting device. One of these cool features is its Active Display notifications that appear on the lock screen. This feature gives immedi ...more
What is Internet Download Manager? Internet Download Manager (IDM) is a tool to increase download speeds by up to 10 times, resume and schedule downloads. Have you ever wanted to increase you download speed form 4kps to 80kps? If you answered yes then you need Internet Downlo ...more
When I first started cooking, there were a few steps I always skipped in recipes. I never added zest to anything because it seemed like too much trouble, I rarely separated wet and dry ingredients in baking recipes because I was lazy, and I never let meat rest after it was don ...more
You may know the traditional way to take a screenshot on your iPhone, but it may not be the best action for your needs. There are faster ways to capture an image of your iPhone's screen, methods for capturing overlays and other elements that won't show in regular screenshots, ...more
Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?) There is no better telltale sign of a script-kid ...more
Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feelin ...more
The LG V20 went on sale on September 29, 2016, and is the second flagship phone in the V series to be released by LG. Both the V20 and its predecessor, the V10, have been audio-oriented phones from the start, but the V20 has a much nicer Hi-Fi Quad 32-Bit DAC, which makes the ...more
Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record. OTR does all the right things to make your instant messa ...more
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements. While Safari didn ...more
Before heading out on a hike, or any excursion for that matter, it would be wise to take a map with you just in case you get lost while on your quest. But let's be realistic, few people are going to use a physical map—or even know how to obtain or read one—in this digital age ...more
Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private ...more
When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, tha ...more
Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner. The banner is simply the application advertisi ...more
As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serv ...more
When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a so ...more
Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of t ...more
Seeing that you probably can't go ten minutes without lying (according to this study), you're probably interested in becoming a better liar. The best way to do so is to learn what makes a bad liar, and then do the opposite. 1. Liars Have Revealing Micro Expressions According ...more
Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time th ...more
Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use Voice Control on the Apple iPhone 3G. The iPhone redefines what a mobile ...more
While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stella ...more
Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website... What's Defacing? Website defacement is an attack on a website that changes the visual ...more
For the majority of my math classes in middle and high school, a graphing calculator was a must. While the calculators were very useful to have, they were quite steep in the price column. After losing the TI-83 graphing calculator my parents bought me in high school, I had to ...more
Check out this video from Chemical Reaction Tutorials (CRTutorials). If you love filmmaking, prop making, editing and everything else that goes along with making movies, then you'll want to see what Adam has to say about teleportation. Adam explains how to create a Dragonball ...more
Don't add your plastic cup to the trash bin just yet. The sturdy plastic material of these ubiquitous containers makes them perfect to use as miniature DIY greenhouses for seedlings, smartphone sound amplifiers, Christmas ornament storage, and even packing material. If you ha ...more
If you've used Twitter on your smartphone sometime in the past two weeks, you've probably noticed that tweets from users you don't follow have been popping up on your timeline. In case you're not familiar with this new Twitter feature, check out two screenshots below from my ...more
Remember that magic trick from when you were a kid where the magician colors the drawing without any crayons? Ever wonder how they do that? Check out this tutorial, and you will know their well-kept secret! Use it to impress your friends! You Will Need • Magic coloring book ...more
When life gets boring, you change it up. A little tweak in your schedule goes a long way in making your existence fresh again, and it could be anything from putting on deodorant to seeing a movie with someone you don't know. The more flexible you are in life, the more dynamic ...more
Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or se ...more
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity! Social Eng ...more
A homemade burger is a delicious thing, but it can be hard to load up with all the fixings. Why? Because said burger is usually wider in the middle and thinner around the edges, like so: Chances are that patty will still be delicious, but your lettuce, tomato, et al. are going ...more
Approximately 380 billion plastic bags are used in the United States every year. That’s more than 1,200 bags per U.S. resident and more than 54 times the number of people who live on the planet. That's why here in Santa Monica, thanks to a city-wide plastic bag ban, you won't ...more
You're never going to see a project from me that involves straight pipe. You would have when I was a kid, but after too many years in the construction industry, I need to see a good finish. If the project doesn't look slick, I don't want to say I did it. I have to say right o ...more
This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me. Introduction:Internet has commonly three parts as per my knowledge 1st:surface web,2nd :Darknet and 3rd :Deep web Surface web:We use surface ...more
Thanks to Samsung Experience 9.0 on the Galaxy S8 (AKA TouchWiz Oreo), we know the upcoming Galaxy S9 is going to enjoy some of the new keyboard changes coming to Samsung's iteration of Android 8.0. Those who preorder the device on March 2 or pick it up on March 16 can expect ...more
You can add full iso roms on your PSP to play on the go, for free! This video will demonstrate exactly how to download and enter full free PSP games onto our handheld. Okay this is a tutorial on how to put psp games on your psp. you will need a psp running custom firmware 3.7 ...more
While Siri's integration with the iPhone is becoming increasingly substantial, restrictions with the intelligent personal assistant are apparent when it comes to third-party apps like Google Maps, Netflix, and Spotify (unless your iPhone is jailbroken, of course). As an avid S ...more
Behold, Kent "Toast" French, the Guinness World Record holder for fastest clapping. You might say, fast clapping? What kind of feat is that? Well, just watch. The video below gets pretty intense... Kent can clap 721 times in 60 seconds. That's 12 claps per second.
Easttexas937 shows viewers how to properly use a Ouija board to get the best experience. First you will need a Ouija board and a pointer. If you want to make these two things, you should use lightweight glass and make sure you make the board properly. You have to have an open ...more
Anonymity is very important to many internet users. By having your "e-identity" exposed online, you can be stuck with a number of unwanted issues, such as: Privacy invasion. Internet tracking. Exposure to being hacked. However, what if we wanted to spend money anonymously? T ...more
Your new HTC One M8 has a ton of really cool features, some of which relate to waking the device up. A swipe up to unlock to your last active screen, a swipe down to access the voice dialer, and a double-tap (or knock) to wake the device and bypass the lock screen. But the on ...more
If you're a lucky owner of the iPhone 4, you know that the upgrade to its camera app includes a front-facing camera feature which acts like a video cam on your computer. Apple, of course, intends the front-facing feature to be mainly used for the FaceTime application which ena ...more
With 16 megapixels and optical image stabilization technology, it's safe to say that the Samsung Galaxy S6 is well-equipped to take badass pictures. Packed with additional camera modes, like Panorama, Selective focus, and Virtual shot, there's always a way to capture an image ...more
Well, this is my first article so if it sucks tell me...lol!! Story Time Well, story time....yaaay!!! I wanted to learn buffer overflows and binary exploitation and all those asm crap...lol So I opened up a lotta sites and eventually came across a polytechnic website with p ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
The all new HTC One M8 is the latest Android flagship making the rounds through major carriers hoping to beckon your purchase. Coming in at about $200 for most carriers with a contract, it makes a good case for itself with its advanced features and solid price point—but, there ...more
When Apple released its Downtime feature in iOS 12, it gave us an easy way to control how much time we spend on our iPhones — but it wasn't perfect. When setting Downtime, you' were forced to use the same time schedule for every day of the week, so your weekdays and weekends h ...more
The man in the video says there are three major things to be aware of when obtaining and using a fake ID card. The first thing and most important thing is to actually look at the fake ID before you are buying. A regular ID should have a name, date of birth and a photo. Make su ...more
The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A ...more
Let's face it. Minecraft probably wouldn't exist today if not for LEGOs. They are fundamentally the same; building objects out of blocks. Only Minecraft has expanded on the idea, creating a world where nearly anything can be made. It's probably even more accurate to say that M ...more
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
Thanks to Smart Switch, it's easier than ever now to ditch your iPhone for a brand new Samsung device, like the Galaxy S6 Edge+ or Galaxy Note 5. Alleviating one of our biggest fears when switching over from iOS to Android, Samsung has made transferring data like contacts, me ...more
In this five-part language tutorial, learn how to say simple Haitian Creole phrases & words. Part one goes over simple phrases such as "how are you", "good afternoon" and "good evening". Part two goes over how to say different animal names including cat, chicken, and cow. In p ...more
Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms. Today, Steampunks frequently get accused of subtly o ...more
Popular photo-sharing service Snapchat has released a major update to both its Android and iOS applications today, bringing secretive chat messaging and live video chatting. Video: . Updating Your iPad or iPhone If you have iOS device and still haven't received the latest upd ...more
This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with l ...more