In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts. In the last Hacker Fundamentals, we talked about the OSI model as well as a little on TCP/IP and the protocols that make ...more
In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and m ...more
¬¬Just about every business has a website these days but very few businesses know how to effectively use their websites to get more customers. There are two different things that a business owner needs to do to increase their website traffic: optimize their site so that search ...more
This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Conte ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we' ...more
Circles. They are both the best thing and worst thing about Google+. They're great because they allow you to fine-tune who you're following and who you want to keep in touch with, making it easy to keep your family and friends separate from each other. On the other hand, they ...more
Hangouts are one of the most fun features in Google+. As long as you have a webcam and a microphone, you can "hangout" with up to 10 of your buddies on Google+ and do just about anything. Of course, sometimes it can get kind of awkward when you are hanging out and you don't re ...more
One of the things I consistently notice amongst fellow internet users is that many people don't know how to properly search for stuff. Google may have served you well in the past, but I'm going to share a few little tricks with you to help make your search results even spiffie ...more
Jezebel's back with another Beauty 101 (1, 2, 3), and this time the issue at hand is body odor. Everybody gets a little stinky from time to time (some more than others), but have no fear- there are solutions. Jezebel readers also address problems such as pit stains, excessive ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned ho ...more
Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth i ...more
Google+ is taking over more and more of Google's core properties. This week, we've seen several announcements from Google blogs about new products, new features, new looks, new integrations. If you're like me, you actually want to know where to go for all the latest informatio ...more
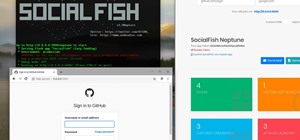
Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame ...more
Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it. I'm sure at one time or another you've heard that hack ...more
Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate h ...more
Games like Minecraft and Braid have proven that there is money to be made in the indie game marketplace, which means more and more designers are following suit, one being Zeboyd Games. The two-man indie design team released two excellent JRPG spoofs on the Xbox Live Indie Game ...more
Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky tw ...more
Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to ...more
ClariTrans is a requester on MTurk (www.mturk.com) they pay very well for transcribing short snippets of audio. Here is how you can transcribe their audio snippets properly to ensure your text will be approved and you will be paid: ClariTrans Transcription Formatting Guide S ...more
While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists sole ...more
Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security profe ...more
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Priv ...more
Although Google+ has solved many of our problems with social networking, it's not perfect, and we all wish they'd be a just a little bit faster with the improvements. In the meantime, you can stave off your hunger with useful Google Chrome extensions that improve upon Google+. ...more
It's really a shame that it is so hard for people to make money on the internet these days. The dot com bubble has receded and scams are plentiful on the web. There are, however, a couple of legitimate ways to make a few extra bucks online, Amazon Mechanical Turk, or MTurk for ...more
On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade vi ...more
STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/ Showing newest posts with label tips-n-trick. Show older posts DEC 07 Computer Backup If you have taken good care of your computer th ...more
The holiday season is here, and if you didn't already pick up a SCRABBLE set during Black Friday or Cyber Monday, then you still have time to buy the perfect gift for your lexical-minded friend. There's sure to be deals out there over the next couple of weeks, you just need to ...more
Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for. ...more
In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then a ...more
Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program. In my fi ...more
Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and ma ...more
Laptops are almost a necessity in today's society. It doesn't help that a laptop that can actually increase your work productivity will put at least a $1,500 dent in your wallet. I'm sure you have searched around to try to find factory direct deals, or (shiver) even looked at ...more
Just how private is your Facebook profile? To some extent, that's up to you. Many Facebook users share and poke their days away, never knowing about the plethora of custom privacy settings that lie just a click away. Facebook's privacy menus can look a little complicated to th ...more
Over the past few months I've written up several helpful How-To guides to help you with various FarmVille related issues. It's about time I put them all in one place so they are easy to find, learn from and share! It has been a pleasure writing for you all and I do hope I have ...more
QI and ZA. QI n pl. -S the vital force that in Chinese thought is inherent in all things ZA n pl. -S a pizza For over a decade, these words have been used in SCRABBLE play, but not in the US or Canada. It wasn't until their addition in the Official SCRABBLE Players Dictionar ...more
How to track an email address. Useful if you meet someone who says they are from somewhere e.g. LA as given in the video and you don't believe them. Go to the Rate a Bull site type in their email address and then hit return or 'find them'. The site will give you options to see ...more
The problem with using only default email as a catchall email account can be summarized in four letters - S P A M. It's a good idea to re-route emails to a default/catchall account. This tutorial shows you how to create a default email address and re-route emails using cPanel. ...more
The whole point of purchasing a smartphone is the access to your e-mail and the Internet, right? Well, check out this tutorial if you are having trouble setting up your e-mail account on your new device. In this video, Dana from Best Buy shows you exactly how to set up your e- ...more
In this video, we learn how to send an email using Yahoo email. First, go to Yahoo and click on "mail". Type in your user name and password. Once you're logged in, click on "Inbox" and click on "Compose". Type in the email address you are sending an email to and fill in the bo ...more
In this how-to video, you will learn how to block Facebook messages going to your email address. First, go and open Google in your web browser. Next, go to the Facebook website. Click on settings and edit your information. Click on the notifications tab. Now, you will be prese ...more
Find a PDF You need a PDF file on your computer to convert, so keep the file path in mind. Visit aXmag Go the aXmag website to submit a PDF. Choose the PDF Click the "Browse" button to choose your PDF file you want to convert. Once chosen, fill out your email address in t ...more
To first get a Skype account you will need to go to Skype and download Skype onto your computer. To download the program click on your operating system and download the proper program. Once it is download you can click on the downloaded file and click on install. It will take ...more
In this how-to video, you will learn how to find the IP address you are using on your computer without using any third party sites. First, go to the start menu and click run. If you are using Vista, go to search in order to the run the file. Next, you should type in cmd.exe in ...more
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 money with Cheat Engine (09/27/09). 1. Log in to your account 2. Go to any shop 3. Open Cheat Engine 5.5, go to Wizard101 4. Put in the am ...more
Wondering how to set up Mozilla Thunderbird? Follow these simple steps: 1. When you first launch Thunderbird you are asked to create a new account. First click Email account and click Next. 2. Complete your name and email address then click Next. 3. Next you are asked for s ...more
Want unlimited Tiki power on Island Paradise? Just use Cheat Engine to hack your way to more power. This is only for 1 use only. Watch this Island Paradise Facebook video to see how to hack unlimited Tiki power in Island Paradise (11/26/09). Use Cheat Engine 5.5. 1. Open Che ...more
Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack Restaurant City: Money cheat (09/30/09). Download Cheat Engine. 1) Open Restaurant City 2) Download and open the X-Force Generator 3) Scan 0000D49 ...more
Download Cheat Engine You can get Cheat Engine here. After downloading, install it on your computer. Log Into Christmas Crunch Log into your Facebook account and go to MindJolt's Christmas Crunch game. Open Cheat Engine / Play Game Open the Cheat Engine and start the game ...more
Dear Jackass Guys well i am John Fears and i am 27 years old and i already met some of you guys but it would be nice to meet the whole cast on the epic event. That is why i am trying out for this contest. you are rock and i have been a fan from the start of your quest for bein ...more
Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most th ...more
It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email ...more
Most packages sent to you via delivery services include a tracking number that allows you to track it from the creation of the shipping label all the way to your doorstep. The U.S. Postal Service includes tracking information with many of its mailing services, but not for firs ...more
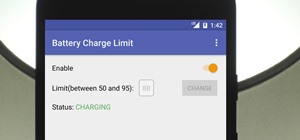
Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion ...more
Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an e ...more
In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new us ...more
What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl. A user with the handle @blanket found out the hard way that Twitter's security is atrocious when his a ...more
Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds. These banners are what the ...more