Recently, Android Police highlighted one of the downfalls of Android 10's new privacy protection: the fact that it broke the ability for apps like Pushbullet to sync your clipboard across devices. While third-party apps can potentially find a way around this, there's no guaran ...more
Sports technology company Form is testing the waters for augmented reality wearables with a product aimed at a very specific user group. On Tuesday, the company unveiled Form Swim Goggles, a $200 pair of goggles outfitted with a see-through display designed to feed activity d ...more
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling ...more
There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to del ...more
EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit ...more
Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is maki ...more
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture. ...more
When you're trying to get fit, friendly competition can go a long way towards keeping you motivated. Samsung Health has a great feature for just that, letting you challenge your friends or even complete strangers to bring some excitement to an otherwise routine workout experie ...more
Snapchat continues to deepen its roster of clients adopting its Shoppable AR Lens, with clothing giant Levi's and Disney becoming the latest brands to try on the e-commerce platform for size. Accessible via a Snapcode posted on Twitter and on display in the Disney Springs Lev ...more
Magic Leap has earned a reputation for overt secrecy, but as it nears the highly-anticipated launch of the Magic Leap One, the company is spilling some of the beans. This week, we get a heaping helping of information on the Lumin OS, as well as a couple of great demos. Meanwh ...more
The long and slow road toward the actual release of the Magic Leap One appears to be accelerating, with a couple of new demonstrations of how the system works revealed in this week's creator's portal updates along with the company's developer documentation. Following the much ...more
A fresh batch of developer info has been revealed on Magic Leap's Creator Portal. On Thursday evening, the normally secretive company gave the general public perhaps the closest look yet at Magic Leap One's Lumin operating system. The screenshots follow on the heels of the pr ...more
Even if your default mobile browser is Google Chrome, you may not want Google to also be your search engine. Maybe you're not impressed with Google's search results all the time, maybe you want a more private search experience, or maybe you just don't want Google's hands over ...more
While TouchWiz as an Android skin isn't a favorite among many, Samsung Internet is a fantastic web browser that S9 owners should be happy to have preinstalled out of the box. But you don't need to buy Samsung's latest flagship to try their browser — Samsung Internet is availab ...more
Augmented reality startup 6D.ai is now accepting applicants for the closed beta of its 6D SDK. While operating in the background on a smartphone, the computer vision platform captures a dense 3D mesh in real time using just the device's camera (such a feat typically requires ...more
With email, one size does not typically fit all. You have multiple email accounts, each for different purposes and with varying levels of importance, so it only makes sense to customize the way your phone alerts you to each account's incoming emails. Luckily, Outlook allows yo ...more
Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add fea ...more
With Google's release of Poly API on Thursday, the search giant has found a way to simplify the workflow for AR creators by enabling the ability to integrate its 3D object search engine Poly directly into an application. While services like Turbosquid and Sketchfab, websites ...more
When you're sending sensitive information via email, it's best to do so with end-to-end encryption. Even better, set the email to destroy itself after a set amount of time for a little piece of mind. Sending a self-destructing email message is a cinch in ProtonMail for Androi ...more
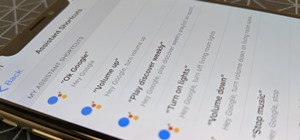
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if ...more
It's never fun when you install an app and then proceed to be bombarded with constant notifications. The SoundCloud app, while great in other regards, tends to have a bit of an issue on this front. So it's only fair that I share with you how to turn off every single one of th ...more
Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you. This is great because u ...more
Before the release of the Galaxy S8, Samsung quietly uploaded one of their core TouchWiz apps to the Google Play Store as a beta. Samsung Internet, as it's called, has been a staple on all Galaxy devices for years now, but you can now try the browser on any Android phone. Aft ...more
If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and ...more
Google Assistant just got a lot more powerful thanks to IFTTT. The automation platform, whose name stands for If This, Then That, connects your favorite online services and smart devices to one another, allowing for a seamless experience with many different gadgets—and Google ...more
These days, when you're setting up an Android device for the first time, you'll be prompted to add extra email accounts directly to the Gmail app. It's really simple, too—just sign in with your work or exchange account, then emails from those accounts will be mixed in with you ...more
The only way to know which Pokémon are in your area in Pokémon GO is the cryptic "nearby" list, which sometimes doesn't work—and also doesn't tell you which direction to head off to hunt that Pokémon you're looking for. Luckily, there's a new app that makes it a lot easier to ...more
There are so many apps out there that it can be hard to decide which ones you should keep on your phone, especially if you're working with limited storage capacity. Sure, you can install and uninstall apps depending on when you need them, but that can be a little tedious. Tha ...more
This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document: Step 1: Creating the Payload For this tutorial, I'll be using a pyth ...more
Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate. The home sc ...more
This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this. Thank You: First thank you for wanting to become a hacker, it is not an easy path. Becoming a hacker, at least in the way that I s ...more
Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, ...more
I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community. What Is DoXing? DoXing is a term we hackers use when gathering information on a target such as a company or more likely an i ...more
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post. Let me introduce myself first ! I am from Greece, I am working as a network engineer and I am into system and network administration but definitely ...more
Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype. What we are going to do today? 1 - get the IP from h ...more
Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this. Requirements: -Web Browser Firefox or Iceweasel In Google Chrome you will have to add an extension called WebRTC Leak Preven ...more
In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic. Now you're faced with the dilemma of how to alert other staff at the school to how creepy he is without letting on that ...more
Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels. "Why would I do that?" One might ask. Good question m ...more
Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and ...more
Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version. You can still locate and launch all of the files and folders you ha ...more
If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well. Please d ...more
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity! Social Eng ...more
Not to be outdone by the announcements of Mac OS X El Capitan and iOS 9, the Apple Watch is also getting a much needed software update. Some of the notable new features we can look forward to on watchOS 2 are Nightstand mode, additional screens for friends, email replies, and ...more
Now that Apple's latest Worldwide Developer's Conference (WWDC) is over, you can sign up for the public beta version of iOS 9 for your iPad or iPhone. For the first time in their history, Apple made a beta version of their mobile OS available to the general public just a few m ...more
Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this t ...more
Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in secur ...more
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedbac ...more
Inspiration for tutorial: Foxtrot's "How to Trap a Tracker" If you have been following my past tutorials, (and it's fine if you haven't,) you would know how much social engineering and doxing I do. During these moments when we are convincing people that we are a different per ...more
The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible ...more
With intelligent grammar check, accurate predictive text, swipe gestures, and plenty of themes, it makes sense that Ginger Keyboard has well over a million downloads on the Google Play Store, making it one of the more popular keyboards available for Android users. GingerSoftw ...more
Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method. Note: This method only works if the website has the vulner ...more
2015 is quickly shaping up to be the year of the cord cutter, with various media companies finally warming up to the concept of offering live streaming content. In the wake of Dish Network announcing a streaming cable service called Sling TV and Sony unveiling a similar platfo ...more
With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other. Pushbullet, ...more
When streaming services like Spotify or Pandora compete for customers, the main differentiating factor is the size of their libraries. While these and comparable services usually run somewhere around $10 per month, a completely free alternative may actually have the most expan ...more
When you've gotta go, you've gotta go. No matter how hard you try and hold your pee (or the dreaded number two), it's going to find a way to leave your body one way or another. That's why it's always good to know where all of the nearest bathrooms are at all times, no matter w ...more
Apple scrubbed the floor clean of all existing text-bombing apps in the iOS App Store, and even though there were once a ton of these apps in Cydia, the go-to store for jailbroken devices, there few and far between these days. If they do exist, they either cost money or don't ...more
Lock screen notifications can sometimes be overwhelming and difficult to manage, especially in the morning when I receive a massive influx of emails, texts, reminders, and social media alerts. At some point it's not even worth scrolling through all of them on your lock screen ...more
Confirmation numbers, grocery lists, addresses, and phone numbers are all things we need to quickly jot down on our phones, but the thing is, they're never extremely easy to access later. You have to figure out which app you wrote them in, meaning lots of needless searching an ...more
You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis? While there are many apps that need your location in order to func ...more
JibJab may not ring the bell, but you've probably seen one of their personalized videos. Using your own images, JibJab will place you first-hand into silly and usually musically-inspired videos that you can view online. Currently in beta, JibJib has made it's way to iOS in the ...more