Hashtags are one of the most important marketing tools available to you on Instagram. Although, it's hard to know which hashtags are working for you or not. You may think #fun is a good one to use but is it really? Okay, yeah, it's a popular one. But that doesn't mean it's the ...more
Yes, there's a way for you to get translations of foreign language websites on your iPhone using the built-in Safari app. Problem is, it's not super obvious. Actually, you'd never know the option was there if someone didn't tell you. But with a little setup on your part, you c ...more
Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in Marc ...more
As iOS 10 makes its worldwide debut, many users are noticing that the promised iMessage effects feature in Messages is not working properly. Instead of seeing the actual effects, messages will come through like normal, but with text describing the effect they were sent with. O ...more
We haven't had a working jailbreak method since October of last year, and that only worked for about a month until iOS 9.2 came out and shut down the loophole it was using. So all of those cool Cydia tweaks have been out of the question for quite a while now, unless you downgr ...more
When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are lo ...more
Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-d ...more
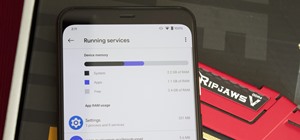
Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it find ...more
Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally. Among the vast ocean of information we need about our target, operating system is de ...more
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online? May be you are an vigilante hacker like me? or You don't want companies logging your Data (Also like me ...more
Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced. In addition to learn ...more
Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photogr ...more
If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streamin ...more
Instead of wasting time asking where your friends and family are at a given moment, then having them waste time by describing their location, there are several Android apps you can use that will automate this whole process. To top it off, it doesn't have to be about invading p ...more
SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET. Step 1: Select Your Target! The First Thing You're Going to Want to Do Is Select the Site Login ...more
Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free. But there's been a lot of confusion about which older versions of Windows will be eligible for the free update, and some unce ...more
Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity. Update: The 4 Best File-Sharing Apps for Android (2018) We've come to a point where ...more
Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time. Don't Miss: 5 Things You Need to Know Before B ...more
If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions. There are a lot of ...more
Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different. In many restaurants, hote ...more
Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side sy ...more
Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System ...more
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing." By utilizing this feature, you are creating a continuity among all of the iOS devices in your family, granting members the ability to share apps, ...more
What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break? But leaving your phone at home or in the office when you go out is absurd, I mean, everyone b ...more
Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works. While the Kindle Store ...more
If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible. A few months ago, Dallas covered six ways to speed ...more
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app ...more
Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the b ...more
Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics. I applaud each of you for your concern, as the last thing I ...more
Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by ...more
Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending ...more
Welcome, my neophyte hackers! The aspiring hacker needs to know a bit of Linux to be successful, and probably most importantly, Linux networking. To fill that knowledge gap, I'm offering this guide on Linux networking basics. I assume that you understand a small amount of net ...more
Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look ...more
When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll. Anonymity can also be important when sending a mess ...more
Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you'r ...more
We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law. Law enforcement officials can seize smartphones and give warrants to Apple, Google, your cellular provider—whoever ...more
When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new ...more
Since iOS 8, it's been possible to use third-party tools such as Bing Translator and Microsoft Translator to translate foreign language webpages in Safari into your primary language. Now, in iOS 14, there's a better way to do it. Before, third-party translation services would ...more
OxygenOS is often described as one of the best skins for Android on the market. It's fast, clean, and has a ton of useful features that appeal to just about everyone. However, it's also faced a significant issue for the longest time — overly aggressive battery optimizations th ...more
Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket ...more
In the wake of Apple and Google pitching augmented reality to schools, McGraw-Hill is stepping up its own augmented reality efforts for education. On Tuesday, the publishing powerhouse announced a partnership with Alchemie, an educational app startup that gamifies learning, t ...more
While The New York Times' augmented reality section has largely been dormant in 2019 (so far), USA Today has continued to crank out AR news stories. On Monday, the news outlet published a feature story about the world's tallest buildings (and the recent lack of new skyscraper ...more
If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a ...more
On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality. In a segment on the new HBO documentary news series from Axios, Cook invited two of the site's journal ...more
With Android Pie beta now available for the Galaxy S9 and S9+, Samsung is well on its way to catching up to major competitors like the Google Pixel 3 in terms of giving its users the latest and greatest software Android has to offer. Of course, Samsung has added its own touche ...more
Space Ape has soft-launched Go Race: Super Karts, giving you a fresh take on mobile racing games by blending in elements found within the classic Mario Kart series and RPGs for some seriously addicting gameplay. And while it's only available in Australia, Netherlands, and Phil ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
Kings of Soccer recently soft launched in the Netherlands and a few other countries, garnering positive reviews from the mobile gamers who've experienced it. With the 2018 FIFA World Cup now in full swing, we wanted to let you in on a little secret: You can play Kings of Socce ...more
Futureplay has soft-launched Battle Bombers Arena, giving mobile gamers a refreshing twist on MOBA by infusing it with simple but addicting gameplay based on the console classic Bomberman. Though only available in select European countries, this game can be played on your iPho ...more
NBA 2K18 has been out for the iPhone for months, but its $7.99 price tag put it out of reach for many mobile gamers. There's light at the end of the tunnel now, as a free-to-play version is in the works as a soft-launch in New Zealand. If you can't bear the wait, you can play ...more
The Android version of Google Chrome only shows a home button on some devices. Unfortunately, this feature isn't available to all Android phones due to several factors. But thanks to a simple workaround, you can now enable this button and set a home page regardless of what dev ...more
Spring training has begun in earnest, and to mark MLB's soft debut, GLU has soft-launched a followup to the smash hit MLB Tap Sports Baseball 2017 in Canada. While MLB Tap Sports Baseball 2018 is still technically unavailable outside of Canada, you can actually play this game ...more
We already know that the connection between virtual and augmented reality is pretty tight, with tools like Unity making porting some apps between the two platforms fairly frictionless. But there are some things currently going in VR that just don't need to come to the world of ...more
The Xposed Framework has an official repository for downloading modules which can be easily accessed by searching the Download section in your Xposed Installer app. But not every module is available on the Xposed repo — in fact, many unique and interesting modules are only hos ...more
Road trips almost always include unforeseen pit stops, which can take you way off track from your destination and end up causing massive delays. But if you rely on Waze for navigation, however, this issue is totally covered. The popular driving app has a nifty feature that le ...more
Disruptor Beam just soft launched The Walking Dead: March to War in the Philippines. It's not officially available in the US yet, but there are ways to play this take on Robert Kirkham's post-apocalyptic masterpiece regardless of where you live. The Walking Dead: March to War ...more
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest brow ...more
While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to deale ...more
With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile bankin ...more
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account? WARNING - geeky stuff ahead! Quit now if sleepy :D You cannot imagine how much of hidden stuff happens when you press your login ...more