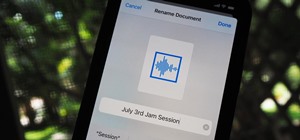
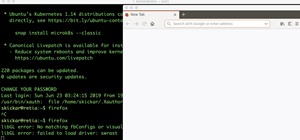
There's an adage that says "Every plan, no matter how great, goes out the window as soon as you're punched in the face." While our lives are (hopefully) not violent, that saying can easily translate to our daily living. That punch in the face can come in various forms, mainly ...more
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use ...more
When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier. There are tons of new ways to interact with ...more
Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful ...more
Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 ...more
Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is ...more
Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the ha ...more
Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy. Many beginners come here looking t ...more
When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier. Now, I'm not saying that learning Terminal c ...more
I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions ...more
Apple prides itself on simplicity, but the company makes downloading video and music files onto your iPad or iPhone an overly complicated process, requiring iTunes and/or iCloud. You can listen to songs sent to you via email, but you can't download them onto your iOS device l ...more
Back in iOS 8, Apple introduced the option to use third-party keyboards on iPhone, and since then, there have been a ton of third-party keyboards available such as Gboard, AudioShot, SwiftKey, Slated, and many more. However, adding and even using these keyboards can be kind of ...more
The autocorrect feature in Apple's default iOS keyboard is anything but perfect. Sometimes it can't autocorrect things on your iPhone to want you want, while other times there's a software bug that just flat out gets it wrong. These autocorrect issues can get even worse thanks ...more
Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Te ...more
Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often ...more
If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull. Now, thanks ...more
Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period. In this tutorial, though, we will be setting up a system to ...more
Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely da ...more
When I see the words "free trial," I know I'm probably going to have to whip out my credit card and enter in the number to "not get charged." Then I end up forgetting about the trial and want to kick myself in the ass when I see my statement at the end of the month. In order ...more
It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes. ...more
There are few apps on my iPhone that I visit on a daily basis, and one of them is Drippler, the discovery and news app that tells you everything you need to know about your device. I've actually been using Drippler on my iPhone since it was released back in March of this year ...more
Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords t ...more
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone ...more
In Minecraft, a large aspect of the game is PVP (Player vs. Player Combat). A hardcore Minecraft fan will remember that back in Beta 1.8, combat was switched up, and it really changed the game around. Here are some tips on what a two-year Minecraft player has to say. Step 1: ...more
In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff. In this guide, written from years of experience with PVP and base creatio ...more
These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals. But when you purchase something ...more
Video: . Optimize your Marketing with a Mobile Website Most companies today have their own website. However, not all of them have a mobile-optimized website. Business owners who do not have a mobile website may have cause to be alarmed. This is because studies say that mobile ...more
Living in Los Angeles has taught me one thing—parking is a luxury. If you are lucky enough to find street parking anywhere near your desired location, do not pass it up thinking you will get an even closer one. It does not exist. Looking for free parking? Get real. You can't e ...more
Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive. End ...more
Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone. The app was removed in mid-2011 (though, it eventually reappeared in early-2013, still available in the iOS App Store today ...more
People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people ar ...more
If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect. The l ...more
There's a way to get instant access to your most-used websites and webpages on your iPhone, and these shortcuts live directly on your Home Screen. Whatever you need fast, frequent, or more convenient access to, whether it's a vital web document or a web app without a native iO ...more
With the release of Object Capture this fall, Apple is giving everyone with a Mac and a camera the means to create their own 3D objects. But what about volumetric video, which currently requires multi-camera rigs like those at Microsoft's Mixed Reality Capture studios? One de ...more
No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from ...more
Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Publ ...more
If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in t ...more
If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been comp ...more
Apple added the option to install custom fonts and use them in different apps on iOS 13. The rollout has been a bit confusing, with Apple announcing partnerships with vendors such as Adobe, but also limiting the feature to work with only certain apps. Nonetheless, you can now ...more
If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and ...more
Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attac ...more
Music streaming services make it difficult to transfer your favorite songs and artists from one service to another and for a valid reason: they don't want you to leave. But when it comes to switching, playlists are a big concern, because who wants to do it all over again? Luck ...more
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tra ...more
For years, there has been a disconnect between the Chrome app on your smartphone and the Chrome browser on your computer. The latter was a powerfully fast browser which could be enhanced with extensions to add new features and functionality, while the former was just a fast br ...more
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and c ...more
Slack recently released a dark mode for its Android and iOS apps, and for the most part, it works great. Super dark gray backgrounds and light gray fonts, which is much easier on the eyes than blinding white backgrounds and black text. But there's one thing that is not affecte ...more
A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hash ...more
Instagram has extensive tools built in for creating and editing posts and Stories, but there could always be more. Third-party apps can help you add photo and video effects for even more visually stimulating content, as well as create announcements, text-based images, and ever ...more
The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years. Now, as the story of the company draws to a close, we finally have some deeper insight into what exactly ...more
Millions depend on Google Maps for directions, and it's easy to see why. The app comes with tons of features like offline navigation, location sharing, and more. Google is far from done, however, and continually improves upon its navigation app to make it even more efficient a ...more
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan wor ...more
The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. T ...more
In a leaked company memo, Snap CEO (and NR30 member) Evan Spiegel has made it clear that the future of the company lies not only augmented reality but also hardware that enables those AR experiences. In other words, Snap is definitely planning on getting into the smartglasses ...more
With the re-emergence of Samsung's Good Lock app, you're once again able to tweak parts of your Galaxy's interface with no root or major modifications required. One add-on in particular even lets you fully customize the Quick Settings panel on your S8, S9, or Note 8 in a full ...more
If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, ...more
Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. ...more
Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered ...more
While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show y ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
With the release of iOS 11, Apple promised to give us person-to-person transactions by way of iMessages. In the iOS 11.2 update, the new Apple Pay Cash system is now ready for you to send money to family and friends right from your iPhone — and there are multiple ways to get i ...more