Pulling off the perfect ponytail is easy once you know a few tricks. You Will Need * Hair that hasn’t been washed in 24 hours * Hair creme * A natural-bristle brush * An elastic ponytail holder * A hair dryer or flat iron * Hair spray Step 1: Start with day-old hair The perf ...more
Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to install a short-throw shifter on your car properly. When servicing any automobile, you should always wear appropriate eye-protection as well as ensure your working environment is properly ...more
The video gives a step by step tutorial on how to replace the water pump, all belts and the shaft seals on a Porsche 944 S2. The video has a German soundtrack but English subtitles are available at YouTube. The repair is shown for a S2, but most steps are the same for other mo ...more
Let your Canon EOS 7D do all the hard work. With the AF Point Selection option, the digital SLR camera will do all the focusing for you. It's easy to compose and shoot in just one step. Automatic AF point Selection: • In AI Focus quickly compose off center subjects without lo ...more
In order to prevent accidental CAP LOCKS, you can use a number of new, innovative and free software solutions. With your Windows 7, there are functions available to assist you. First, go to your start menu. Click on Control Panel. Next, select "Clock, Language, and Region". W ...more
Watch this video from This Old House to learn how to put in a storm door. Steps: 1 Use bevel square to establish angle of doorsill. 2 Mark doorsill angle onto the bottom end of the hinge frame. 3 Use hacksaw to cut hinge frame to length. 4 Screw hinge frame to edge of screen ...more
Battery life is a constant problem with cell phones today, and the Droid smartphones running Android software are no exception. If you want to learn how to get the most out of your Droid battery, then check out this helpful video that provides 8 tips on cutting battery-eating ...more
This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration date ...more
Some of you may stick with your iPads, but for those looking for a similar Android version, you finally have a winner. To master your new Motorola XOOM from Verizon Wireless, check out the product support page. There, you'll find interactive walkthroughs for getting started, ...more
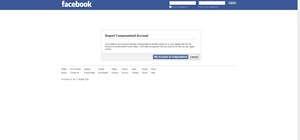
Been hacked once? Twice? Maybe more? You thought abc123 was the only password that is both 6 characters wide and easy to remember? I have some suggestions in store for you. Just read on... An Introduction There are passwords that look tremendously sexy (as opposed to gibberi ...more
Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer. It's called the Cr-48, a black notebook wh ich runs an extraordinary operating system— Google Chrome. ...more
You've had a massive hard disk failure.. ...in your PC or laptop and like a large number of people who think it will never happen to them...you did not have a backup of those 2000+ family pictures, those hundred of important Word documents, those family videos that you downlo ...more
What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense. But surprisingly, this is no easy task in Mac OS X. Snow Leopard does not have an easy one-click option for password protecting files and fold ...more
Illustrator's gradient mesh tool is a powerful one for vector artists... if you know how to use it. This tool can help create beautiful and vivid mesh-based vector portraits, as long as your skills are up to par. If not, try out some of the beginner tutorials on WonderHowTo fo ...more
My girlfriend was going away for a few weeks, but where she was going, there was no easily accessible Internet. She works mostly on the web, so it was imperative that she have a decent Internet connection during her travels. So, tethering her phone was the only real possibilit ...more
Keep your possessions safe from thieves with these tips. You Will Need * Motion detector lights * Locks * A locksmith * A security alarm system * A safety deposit box or home safe * An engraving pen * A trusted neighbor * Bolts or wooden dowels (optional) Step 1: Eliminate bu ...more
In this tutorial, we learn how to make your home safe and secure with tips from Lowe's. You should do a safety check on your house at least once a year. Start with the entryway, making sure you have an insulated wood door in the doorway. Make sure there is a lock and a deadbol ...more
The use of heavy duty resistance bands (also referred to as "Powerlifting Bands") as a strength training aid has become increasingly popular over recent years. The bands are used for accommodating resistance; a technique that involves creating maximal tension throughout a full ...more
Low battery – two words you never want to hear. Banish them with these tips. You Will Need * An iPhone * A computer with internet access * An external battery extender Step 1. Lock iPhone Lock your iPhone down when you’re not using it. Press and hold the Sleep/Wake button ...more
Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things lik ...more
Mike Lively of Northern Kentucky Universtiy demonstrates how to grab a website's resources for reconstruction in Flex using HTTRACK and Wireshark. This tutorial is especially helpful for sites you want to grab that think they are very locked down and secure. All with the free ...more
The Improved Half Blood Knot is basically a half blood knot with a little improvement. To make the knot more secure the end tag is locked in the final step when tying the knot. The Improved Half Blood Knot is a popular knot for attaching hooks, swivels and lures to the the fis ...more
The SportRack bike rack lock kit can be easily added to many of the SportRack model racks. It includes two locks, one that secures the bikes to the rack and another that locks the rack to your trailer hitch. It only takes a minute to install and is dead simple to use, as this ...more
Ron Paul's 2012 campaign has won the majority of Washington's delegates to the Republican National Convention, and a number of other states are expected to follow suit, pointing to a hectic convention in which Mitt Romney's path to the nomination may face a major insurgent opp ...more
My Blackberry TV demonstrates how to protect your Blackberry device with a password. Protecting your Blackberry with a password will help to stop people from accessing your personal information on your device. From the home screen, press the Blackberry menu key. Then, select t ...more
In this video, Richpin demonstrates how to replace the camshaft sensor in a Nissan Altima. The cam sensor is located by the cylinder box. First, remove the electrical connector off of the sensor. Push up on the lock on the bottom of the sensor to pull back and remove the conne ...more
Look at the Main Menu on our screen. If the Icons on the screen do not respond to your commands, it means that the system is corrupted. To fix this problem, hold and press down the Power and Menu button at the same time for about 6-8 seconds or until you see a black and white ...more
Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject. LifeHacker posted a great detailed text guide to accompany the second ...more
This video demonstrates how to secure a laptop. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to secure a laptop, For Dummies. This video offers a number ...more
The Half Blood Knot is similar to the clinch knot. It is same knot with two different names. This instructional video demonstrates a variation called the Locked Half Blood Knot. This variation adds a way to secure the tag end in the final steps of tying the knot. The half bloo ...more
SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and e ...more
Materials Needed! Video: Undo a door's chain lock from outside with string, yarn or shoelaces. Basically all you need is some kind of rope like material. For example, you can use the following: Yarn, Thread, Floss, Ribbon, shoe lace. Just make sure it's about 2 to 3 feet in l ...more
Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds. Protect your email with encryption Did you know that all you have to do to avoid getting spam i ...more
This video by repairs universe shows viewers how to replace the battery in the 2nd Generation iPod Touch. The tools you will need for this project include safe-open pry tools and a small phillips head screwdriver. To begin, remove the screen by releasing several clips that hol ...more
The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new ...more
This wrap is intended to support and stabilize the ankle joint. Supplies needed include a 1 - ½'' – 2'' adhesive tape, pre-wrap, and heel and lace pads. Apply heel and lace pads at high friction areas, including the distal aspect of the Achilles tendon, and the dorsal aspect o ...more
Richpin demonstrates how to remove the inner tie rod end on an automobile. First, get the car up in the air and support it by jack stands. Remove the wheel assembly. Loosen the outer tie rod end next to the steering knuckle. Loosen the jam nut. Then remove the nut that secures ...more
Cute Girl Hairstyles shows you how to create a French braid hairstyle for your hairstyle. Firstly, divide the long hair into two parts with a zig-zag parting on the top of the head. Keep one half of the hair in a ponytail to keep it out of the way. Wet the hair down, and take ...more
Follow this video to learn some basics on how to use a Samsung Galaxy I7500 mobile phone. Switch on the phone by pressing the power key in the bottom right corner. To navigate around the screen press with your finger on the touch screen and swipe to the left or right. If you w ...more
Shampoo and condition your hair. Use a lightweight conditioner that won't weigh it down; try a volumizing formula. Blow dry the roots of your hair with your head upside down, using the cool-shot button every few minutes to lock in some volume. Stop when your hair is damp, but ...more
Worried about your baby or toddler either wrecking or wrecking themselves in your home? Baby proofing time! Make sure your house is safe and secure for your child when they start exploring their turf. You Will Need: • Blankets • A smoke and carbon monoxide detector • Batte ...more
With the growing popularity of cordless power tools, it's extremely easy these days to accumulate a lot of portable tools, and when you add in quality corded tools, such as circular saws, routers, planers and air nailers, you can end up with a pretty hefty investment. These sa ...more
Two locks are used for truck trailers to prevent someone from taking the trailer. Secure a truck trailer by using locks with tips from a custom car repairman in this free auto maintenance video. Part 1 of 17 - How to Connect and load truck trailers. Connect and load truck trai ...more
The seated chest press can be done from any chair with a seat back. This exercise is great for shaping and strengthening the chest muscles. The chest is scientifically named the pectoralis. This muscle is used any time you push a chair up to the table, shut a car door, or push ...more
The use of heavy duty resistance bands (also referred to as "Powerlifting Bands") as a strength training aid has become increasingly popular over recent years. The bands are used for accommodating resistance; a technique that involves creating maximal tension throughout a full ...more
Watch this video from This Old House to learn how to fix a bath sink stopper. Steps: 1 Pull out the old pop-up sink stopper. 2 Use an adjustable wrench to remove the pop-up lever from beneath sink. 3 Loosen the compression nut connecting the trap to the vertical drain pipe. ...more
If you're bound to a wheelchair and living in Orange County, California, then this video is a must-see if you use public transportation. It will show you the steps to boarding an Orange County Transit Authority (OCTA) bus the right way, when in your wheelchair. 1. Arrive at t ...more
Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organiza ...more
In this video from iPT2gGeec we learn how to change the font on the iPhone. Your phone needs to be jailbroken. Open up Cydia and search for Fonts. Select Font Swap. Install and confirm. Once loaded, go back to the home screen. It requires no reboot. You will see the Font Swap ...more
The aerator on your faucet serves a very important function: by adding air bubbles, it helps to fuse the water and give it a softer feel. It also helps reduce the amount of water you use. So if you're faucet's water stream is acting funny (like a drop in pressure), it might be ...more
In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on t ...more
In this video tutorial, viewers learn how to secure a Mac Book Pro. Begin by opening the System Preferences and select Security under Personal. In the General tab, users are able to put on a password when the computer goes to sleep or screen-saver, disable automatic log in and ...more
Time-lapse photography used to require expensive and dedicated equipment, but in today's futuristic world, we now have easy access to universal machines like the iPhone, which are pretty much tricorders. Reel Moments is a time-lapse app for the iPhone from Nexvio. It’s a ‘pic ...more
When the iPad 2 was released earlier this month, as to be expected there was a whole lotta buzz. And for good reason—while the the newest version shares the same price tag as the old, it boasts some significant new features. In case you missed it, here's a quick overview: Bet ...more
Learn how to give your daughter a trim and you’ll save big bucks on trips to the hairdresser. Learn how to give a child a haircut, at home. This is a cost effective tip that will help you save money. You Will Need * Haircutting scissors * An eye-level seat * A video distracti ...more
We've all been there. You wake up early, hungry for breakfast, but not just any breakfast will do. You want bacon and eggs. So, you blindly stumble into your kitchen, underwear-clad, and begin fumbling about with pots and pans. After a few minutes, you fill your pan with delic ...more
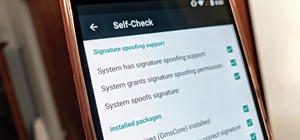
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography. What Is Public K ...more
SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can ...more
Before jumping right into becoming the next James Neely or Moose Peterson, you're going to have get situated with your new digital SLR. No matter if you purchased the Canon EOS 5D Mark II body and lens separately or together, you've got everything you need to get started excep ...more