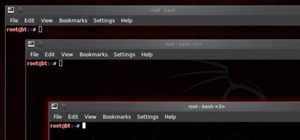
Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudul ...more
Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the c ...more
Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll ...more
The new iPhone X will be released on Friday, Nov. 3, in Apple Stores located in over 55 countries and territories. For those of you who would rather skip the in-stores lines that will start building well before the 8 a.m. local time openings, you can preorder the iPhone X on F ...more
Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information. B ...more
If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground. During Uber's beta bug bounty program, which was conducted over a time period of 10 months with 200 security rese ...more
Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on. Those are just the big ones that get reported in the news. Millions ...more
Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left f ...more
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions. Unfortunately, for Apple developers ...more
Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not. Blackphone wants to change s ...more
When downloading any application on an Android device, you will always be prompted by the following... Whether it's Angry Birds, Shazaam, or Chrome, every application will ask for permissions. If you try and deny these permissions, it won't install, leaving you with no other o ...more
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from eve ...more
Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round. On Friday, the company announced that it has secured $280 million in funding from NTT Docomo, the largest wireless provider in Japan. Video: ...more
The partnership between Magic Leap and leading South Korean wireless carrier SK Telecom took on an added importance earlier this week as the company unveiled the world's first nationwide 5G network. During an event at SK Telecom's headquarters in South Korea, Jung-ho Park, th ...more
Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your el ...more
Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for ...more
Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees f ...more
Google caught a lot of flak for the Pixel 2 XL's POLED display issues, regardless of whether the problems were real or perceived. It's too late to contract another screen manufacturer at this point, but Google is doing the next-best thing: Fixing as many user complaints as pos ...more
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you h ...more
Five Phases of Hacking:- The five phases of Hacking are as follow: Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks The Five Phases of Hacking Reconnaissance:- This is the primary phase where the Hacker tries to collect as much information as possib ...more
Welcome back Hackers\Newbies! Hey guys first of all I would like to explain my absence here in NullByte. I got a little "occupied" with "other things". When I got back, I saw all these HowTo's, articles, Help Questions, I decided, I need to share more of what I have, to you g ...more
Since the days of Friendster and MySpace, social media platforms have taken leaps forward, revolutionizing how we live our lives by changing the way we communicate with others. Not only has social media become a catalyst for major uprisings around the world, but on a personal ...more
If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its ...more
One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters. ...more
Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in t ...more
The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just rel ...more
On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's ...more
Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them ...more
The year is still off to a roaring start, with augmented reality at the center of nearly everything, from enterprise solutions, to entertainment, to safety. In the realm of streaming, the Marvel universe got another dose of augmented reality marketing help thanks to Disney Pl ...more
It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one ste ...more
There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your ...more
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet. So no, there's no such ...more
One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowi ...more
The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere ...more
After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimiz ...more
In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM ...more
Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of ...more
Animoji, short for animated emoji, was a focal point of the iPhone X presentation at the Sept. 12 Apple event. The reactions were split, to be sure, as some considered the attention to this feature on a $1,000+ smartphone to be a bit, well ... too much. As goofy as Animojis ma ...more
Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it. Speaking at the National Governors Association this weekend, Musk covered a lot of ground when ask ...more
The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future. The main idea behind the Observa ...more
It looks like Samsung was thinking about slapping a little nub of a home button on the Galaxy S8 and S8 Plus. This is according to a patent published by the European Trade Mark and Design Network, uncovered by Android Headlines. Despite having a nearly bezel-less display on th ...more
Dreaded are the days when you're working on a masterpiece, then all of a sudden, your Windows computer crashes, loses power, or an app just gets up and quits. Well, now there's an app for that. According to MakeUseOf, with an app called AutoSaver, you can automatically save t ...more
Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week. On Monday, March 20, Vodafone Group PLC announced that they would combine their Indian branch of business with the local competition to create India's biggest wirel ...more
Blue light (like that from our smartphone) tricks the human brain into thinking it's still daytime, even if it's coming from something as small as a screen. So while you're playing around with your new Pixel or Pixel XL after dark, subconscious signals to be awake are preventi ...more
Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind. While 620 Gbps is impressi ...more
In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to ...more
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the ser ...more
Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them. In each ...more
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at ...more
Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps ...more
In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new us ...more
In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent. It's been rulings like these and their call for internationally recognized rights to pr ...more
Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications. Why You Should Update Your Device SSL, which stands for Secure Sockets Laye ...more
Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make m ...more
There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to ...more
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key. Kind of makes you wish you co ...more
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on: Plans for Syria? CNN reports this afternoon th ...more
Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding your stuff. Apple's $29 Bluetooth beacons definitely drew some inspiration from Tile's l ...more
If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your exper ...more
These days, everything is connected. No, really — we mean everything. Your phone, your smart speaker, and even appliances like stoves and refrigerators can be connected and communicate with one another. Welcome to the Internet of Things, the start of our interconnected future. ...more