I've already covered how you can automatically save Snapchat photos and videos to your Samsung Galaxy Note 2, and how to take screenshots of Snapchats sent to you without the sender knowing, but there's one other thing about Snapchat that could use some softModding. Currently ...more
Do you experience a pang of envy when you scroll through your Facebook news feed, Instagram home, or Twitter timeline and see all your friends doing super-awesome things that you weren't a part of? If you are like most people, then the answer is probably yes. This particular ...more
The Guardians of the Galaxy have to be the most fun superhero team to have at a Halloween party. They dance, they break the rules, and they definitely have the grooviest music. So the Guardians are a great bunch to pick from for your Halloween costume — or even for a themed gr ...more
The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of ...more
The force is strong with this project. Colin Furze is a British YouTuber who is a self-proclaimed "garage inventor and video maker." In a recent collaboration with eBay, Furze created the "ultimate Star Wars project," an 18-feet-tall playhouse version of the AT-ACT from Rogue ...more
Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self. Step 1: Recognize Open Ports First step is recognize open ports i ...more
If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for you ...more
There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet. Besides, that ...more
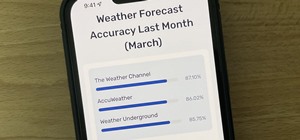
If you've spent most of your life in one geographic location, you're probably pretty familiar with the weather there (unless you're a hermit). If you live in a tropical climate (and haven't done much traveling), maybe you've never even seen snow. Regardless, the idea of a tin ...more
Many recipes call for self-rising flour as a staple ingredient. Oftentimes, we find ourselves passing these recipes by because we don't have it on hand, or because we don't use it enough to actually want to buy it. Don't Miss: Cook Like a Chef: Use Ratios, Not Recipes Lucki ...more
The title pretty much speaks for it's self, basically you'll be putting a smoke bomb inside a candle. Obviously you'll be modifying the candle's appearance but make sure you do at good job at disguising the smoke bomb. Next time someone tries to light the candle, they'll be in ...more
In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent. It's been rulings like these and their call for internationally recognized rights to pr ...more
The new rail system might be a small (Read: BIG) problem for those who like using rail systems. See for your self! Check out BebopVox's video: Video: .
If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional ...more
Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and lon ...more
There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Sn ...more
Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem. ...more
When you're sending sensitive information via email, it's best to do so with end-to-end encryption. Even better, set the email to destroy itself after a set amount of time for a little piece of mind. Sending a self-destructing email message is a cinch in ProtonMail for Androi ...more
While using end-to-end encryption may be enough security for most of your messages in Telegram, you can go a step beyond this by sending messages that disappear after an allotted amount of time. This prevents you from having to manually delete the message at a later time, so y ...more
If you thought the selfie would only ever be used to bombard your feed on Instagram, you were wrong. Dead wrong. JetBlue is looking to take those selfies and use them to check you in for your next flight. In an announcement on Wednesday, the airline said it was partnering wit ...more
Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' k ...more
YouTube announced last October some of the original programming it was producing for its YouTube Red subscription service, and the first four originals went live on Wednesday, February 10th. The first four original series are Lazer Team, A Trip to Unicorn Island, Scare PewDie ...more
There are few things that make me smile more than ice cream… or bread! So why not combine them for double the happiness? We've discussed the art of making ice cream bread before, but not everyone has the time (or, let's face it—the patience) to bake bread in the oven, no matte ...more
While shortcuts to your Camera and third-party apps like Snapchat are great for capturing fleeting moments, it still takes a few seconds to open them and snap a photo. That means you could potentially miss a great shot if you're not quick enough. But now there's a super-fast w ...more
In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new us ...more
One of the most rewarding things about jailbreaking is theming. Unlike Android, iOS doesn't allow you to make small changes to certain aspects like the icons or the lock screen, so jailbreaking facilitates the ability to make some of these desired changes happen. Previously, ...more
If you thought iOS 7 was a drastic change from previous iterations, iOS 8 will certainly continue to rock the boat. From a revamped Control Center to enhanced "Continuity" to ephemeral messaging, Apple's newest mobile operating system will have many of you relearning the "basi ...more
While you may suck at Instagram, it's likely that you manage multiple Instagram accounts, whether strictly for personal use or for managing blog and business pages. Unfortunately, unlike Twitter and a few other social-oriented apps, Instagram does not have a native feature th ...more
Snapchat's self-destructing nature is the perfect way to send funny and potentially embarrassing photos and videos (something Anthony Weiner wishes he knew about). That's why there are currently 150 million Snapchats sent each day. While it may be used for fun, many fail to re ...more
In early 2000, at the age of 19, Noah Kalina began taking a photo of himself with the same facial expression—every single day. Six years and over 2,000 photographs later, Kalina turned his project into a time-lapsed montage on YouTube. In just one day, his video received over ...more
Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app. Since Androi ...more
Forwarding messages is a helpful Telegram feature that makes it easy to share funny and entertaining content with other contacts. However, for the privacy-centric, forwarding poses an issue, as messages of yours that are delivered elsewhere carry a tag back to your account. Lu ...more
WhatsApp comes with a ton of great features that make it the go-to messaging app for millions of people around the world. Among these is the ingeniously simple Read Receipts that let you know your message has been viewed. If you want to read a message without alerting the send ...more
If you're not looking closely, it's easy to mistake last year's Galaxy S8 for the brand new Galaxy S9. Design, build materials, screen size, software — it's all virtually identical, save for a few exceptions. But those minor differences can add up. We made a chart highlightin ...more
SoundCloud is a really interesting alternative to Spotify and Pandora in that it will never really give you the exact mainstream song that you want. If you're looking for new up-and-coming artists that are making some wonderful alternative remixes to mainstream music, then Sou ...more
Soda bottle jello went viral when the popular YouTube channel AwesomeDisneyToys posted video directions for this revolutionary gelatin confection. I just had to try it out to see what the hype is all about. Video: . My takeaway: Yes, it really is as easy and fun as described i ...more
Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1. Today, we will try to build an ftp cracker in ruby: This is going to be a quick one since OTW has already made one in python and we are gonna look upon that to create a simil ...more
I've covered a few multitasking app switchers before, but none of them are as sleek and smooth as the aptly titled Switchr, a new app developed by Mohammad Adib that lets you move from one app to another quickly and smoothly—just like how I switch between my women. Well, not r ...more
With the introduction of Vine and the subsequent Instagram update, abbreviated video sharing has come to the masses, to be experimented with in an unprecedented way. While both video-sharing apps have their own set of restrictions (length, size), it's never suffocating and ac ...more
I want to talk about growing up with burden of acne. I frequently receive comments and private messages about kids being bullied for having acne, this is not right. Everybody is beautiful in their own way and you should never let the haters put you down! Love yourself =) Video ...more
Approximately 380 billion plastic bags are used in the United States every year. That’s more than 1,200 bags per U.S. resident and more than 54 times the number of people who live on the planet. That's why here in Santa Monica, thanks to a city-wide plastic bag ban, you won't ...more
Do you have an excess of empty yogurt containers? Do you also happen to have a green thumb? Put two and two together to make a DIY self-irrigating planter for your next tomato plant, herb garden or whatever green growing thing suits your fancy. Unlike the standard method wher ...more
Heatherwick Studio's London based rolling bridge is an engineering marvel. Lots of fun, and immensely satisfying to watch (via YouTube, assuming you can't see it in person). From Heatherwick Studio: "Rather than a conventional opening bridge mechanism, consisting of asingle ...more
Forget the Segway, you don't even have to stand anymore thanks to Honda's U3-X. This self-balancing unicycle relies on an inclinometer instead of gyroscopes to keep the rider balanced. The personal transporter even allows the user to travel forward, back, left, and right thank ...more
Self proclaimed "Paper Airplane Guy", John Collins, is the master of paper crafted flight. Collins hosts workshops for Corporate America, using the paper airplane as a metaphor for success: "Weaving your corporate message into the stories of how the planes get invented, ties ...more
Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there ...more
Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available ...more
The recent announcement of a $480 million US Army contract awarded to Microsoft over Magic Leap for supplying 100,000 augmented reality headsets shows just a how lucrative the enterprise (and government) sector can be for AR. However, considering sales of total smartphones to ...more
Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But ...more
IFTTT is a fantastic tool that lets you trigger actions on your smartphone that normally require more advanced hacking. With the help of its friendly user interface, turning your phone into a more personal device has never been easier. However, the app has some more intricate ...more
There are two core components to any Tasker automation: A profile and a task. Profiles are basically a set of conditions that must be met before Tasker will do anything. Tasks, on the other hand, are the actions Tasker will perform when your profile's conditions have been met. ...more
New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 milli ...more
Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations. For example, you don't necessarily want to give your real phone number out to strangers when you're buying or selling something on Craigslist, managing an Airbnb listin ...more
When it comes to Android automation apps, Tasker has never had much competition. But considering how difficult it can be for a novice user to get the hang of things, and factoring in Tasker's drab and complicated interface, there's definitely room for another developer to step ...more
Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes. A class is basically an object. It's something that we can make att ...more
Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few brows ...more
When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a so ...more
Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all kno ...more
From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home. However, there's a trick to avoi ...more
So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "bro ...more