We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of compani ...more
Instead of wasting time asking where your friends and family are at a given moment, then having them waste time by describing their location, there are several Android apps you can use that will automate this whole process. To top it off, it doesn't have to be about invading p ...more
There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various oth ...more
If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you ...more
Eventually, your voicemail inbox on your iPhone will get full, and you'll have to delete some messages in order to make way for new ones. If all the voicemails you currently have are super important, you're not going to want to delete them before saving them first, of course. ...more
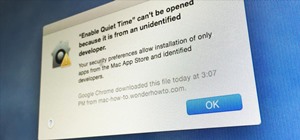
Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to ...more
Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable. For example, you could send the credentials your victim enters to a script that mails you notifying you of new data someone's just entered, or automatically store them in ...more
Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is ...more
It seems like whenever someone sees my phone, they ask me two questions right off the bat; "What phone is that?" and "How did you get your Android to look like that?" The first one is pretty straight-forward, but the second one not-so-much. I've spent countless hours searchin ...more
In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links ...more
Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :) You may have made a malicious apk (android package) before on kali, ...more
Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device. Deleting your messages and pictures manually is a good to protect yourself from aver ...more
Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all kno ...more
hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack. ...more
Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series ...more
Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have ...more
So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate. In all seriousness, switching between mobile ecosystems can be quite the hassle. Even after you've grown accustomed to the new ...more
One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-par ...more
There are many reasons to root Android, but for me, the most important one is to have the Xposed Framework. Xposed gives you access to hundreds of modules, which take away the need to manually modify core system files to add new features and functionality to your Android devic ...more
The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can c ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achi ...more
These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more. But just because there are lots of opti ...more
Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack. Hello, my hacker friends! Today we are going to look at how hackers can take advantage of the system, and repeatedly crash the ...more
Carriers like to distinguish their Android phones from the competition by making small changes to the interface here and there. This practice is so common that Android now has a built-in system for managing these small tweaks. A series of XML files known as CSC (customer soft ...more
Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you ...more
After you have registered to this site,sign in then to start missions. Basic Missions as you see in the pic in the challenges you can choose any missions but i start from basics. after you go to basic missions(it contains 11 missions) you will see this pic. go to basic 1 St ...more
Now that we have our vulnerable server, it's time to start up BeEF. Getting Started Step 1: Running BeEF If you have Kali, BeEf comes pre-installed. You can find it in /usr/share/beef-xss/. Once you're there, type ./beef to execute the program. You will need to know both of ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! As much as I love other SSH bruteforcing tools like Ncrack, Metasploit, THC-Hydra, ... ( Just to mention a few ). I prefer using my own script. The tools ab ...more
Accessing and getting in touch with your favorite contacts has never been easier thanks to the "Friends" feature on the Apple Watch. However, this only applies to users who are running watchOS 2.2.2 and lower. When Apple issued watchOS 3, the "Friends" option was completely re ...more
If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social ...more
Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time. We've been having a lot of fun with all the new Messe ...more
Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels. Welcome back, my excited hackers! Right now I am on vacation in the wonderful city of Tulum, Mexico. I thought it would be a great idea to teach you guys yet another social en ...more
Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter ...more
We've all received those impersonal mass text messages, whether we're getting invited out to a birthday party, graduation celebration, or just a group dinner or outing. Usually when I see those sort of text messages, I delete them, mostly because they're not personal. If some ...more
You can find a plethora of tennis games on the Google Play Store, but if you're a true tennis fan and gaming enthusiast, you should check out Tennis Racketeering by Core Aplikacije. The game lets you use an additional Android device as a racket, giving you Wii-like abilities w ...more
When you send an emoji from your Android device to someone that uses an iPhone, they don't see the same smiley that you do. And while there is a cross-platform standard for emojis, these don't work the same way as unicode-based smilies or dongers, so not every operating system ...more
With the advent of text messaging, our communication habits have changed drastically. Social niceties are still there, but we budget our words a little more since they have to be typed out rather than spoken. After all, SMS stands for "Short Message Service," so this is the na ...more
Location Services, a native feature on iPhones since iOS 6, is used to pinpoint your approximate location using a combination of GPS, Bluetooth, Wi-Fi, and cell tower information. Apple uses this on their smartphones for many useful reasons: so that you can tag locations in In ...more
While shortcuts to your Camera and third-party apps like Snapchat are great for capturing fleeting moments, it still takes a few seconds to open them and snap a photo. That means you could potentially miss a great shot if you're not quick enough. But now there's a super-fast w ...more
Mikoto, from Karen Tsai (aka angelxwind), is a free jailbreak tweak unlike any other. With Mikoto, you can customize features in your favorite iOS apps to an extent that you would've never thought possible. Not only is the tweak elegantly designed, but it also has more settin ...more
Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different appro ...more
In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your i ...more
Android 5.0 has a cool new feature called Priority Mode that allows you to silence your phone's ringer except for when certain people call you. It's something you'd enable right before bedtime, for instance, if you don't want to be disturbed unless it's someone important tryin ...more
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook. ...more
When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their ...more
Apple scrubbed the floor clean of all existing text-bombing apps in the iOS App Store, and even though there were once a ton of these apps in Cydia, the go-to store for jailbroken devices, there few and far between these days. If they do exist, they either cost money or don't ...more
You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis? While there are many apps that need your location in order to func ...more
The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try ...more
Apple's iPhone 6 packs a powerful 4.7-inch Retina HD display with 1334-by-750 resolution, and it's so incredible in person that it almost looks fake. However, as awesome at this display is, it can always be better. As long as you're jailbroken, you can get the same 1920-by-10 ...more
In places like underground bars or national parks, your phone's Internet service is sure to slow down to a very sluggish pace, making it difficult to surf the web. Or worst case, data will be non-existent, leaving you with only low-level network support for calls and SMS text ...more
Silencing my phone always gives me mild anxiety; while my Android is muted, my girlfriend or boss may be trying to reach me with some urgent news or task. On the one hand, I want to enjoy some peace and quiet, but on the other, I don't want to come back to a phone with 100 mis ...more
Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added. That's a very interesting new feature because it allows Kali to be easily booted on Mac too, and every EFI-supported device. First three preview lines gone? As alw ...more
By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions. We've spent the last few days getting to know it, and let ...more
It takes a lot of time, effort, and cash to create a unique Halloween costume that will likely never see the light of day after the 31st. Not to worry: you can do it on the cheap and feel savvy and creative while everybody compliments your ingenuity. Considering how frequentl ...more
Google's Android L developer preview has given Android a more refined look, with developers excited to update their apps with the new Material Design UI. While some apps are slowly getting updated, QKSMS (QK for quick) is a 3rd-party text messaging app that was built with Mate ...more
As messaging and texting have all but replaced the need to actually call someone, emojis have seemingly replaced our need to type out text. With a simple emoji, you can relay emotions like "I don't feel very well" or "I love you" quickly and easily, knowing that the other part ...more
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them. While this automation does make your life a little easier, it ...more
In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones. All rheto ...more
Shortly after the official release of iOS 8, news outlets like BGR, Gizmodo, and Huffington Post were instructing iPhone 4S users to refrain from updating (which were practically regurgitations of an Ars Technica piece). I'm not here to sway you in one direction or the other, ...more