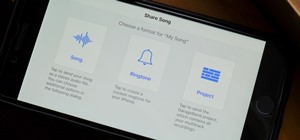
While you can quickly see the edit history of a modified iMessage in the Messages app, there's no way to view an iMessage that somebody in the conversation deleted unless you happened to see it before it disappeared. But that's only true if you didn't implement these security ...more
If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand. New feat ...more
Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpr ...more
How to stop your avatar from walking around when ploughing and seeding in Farm Town Farm Town hacks, cheats, glitches. How to hack Farm Town. Description of the app on Facebook: In the world of Farm Town you and your friends can have a great time! You can play games, design, ...more
Welcome to the Official Jackass 3D Prank Contest Submission Page Think you've got the wit and imagination to be a Jackass? Well, here's your chance. Johnny Knoxville and Jackass 3D crew are hosting the first ever Jackass 3D Prank Contest to celebrate the upcoming release of t ...more
Apple released iOS 12 on Sept. 17, and most of the announced features have been released for the iPhone's latest available operating system. However, some brand new features can be accessed with Apple's latest beta, iOS 12.4. If you want to try out all its new features before ...more
The new iPhone 6 and 6 Plus are supposed to last a lot longer in your pocket with improved battery life, but that doesn't mean that iOS 8 will be that friendly on your older iPhone model. All of those awesome new features could be killing your battery, but with some simple twe ...more
When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick ...more
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out ...more
Apple's Shortcuts app lets you make and use custom icons for any app on your iPhone, but it won't actually replace any icons. If your goal is to change the official icon for the app itself without any redirects, there's a growing list of third-party apps that'll let you do jus ...more
Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and ...more
WhatsApp is a very popular messaging app on the Play Store, but unfortunately, tablet users have been left out of all the fun because WhatsApp only works on smartphones—until now. Tech wiz James Nakata wrote up a short guide over in our forum for porting WhatsApp onto a Nexus ...more
Hidden deep in WhatsApp's emoji database is a middle finger emoji, and there's a really easy way to use it. Much like Spock's "live long and proper" Vulcan salute, this one can be used simply by copying and pasting the emoji from our tweet. Note that the emoji, for now, does n ...more
Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any ...more
Check out this video on how to hack Facebook Farm Town using a cheat engine! This is a Flash game on Facebook by using a program designed to automatically make you beat it. This gives you more coins than you have earned. Watch this video tutorial to learn how to get fast poin ...more
It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more
Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees f ...more
One of the more competitive aspects to chat apps these days is customizability. It seems every messenger wants to offer the largest number of options for users to make the app feel like a truly personal experience. Telegram is no stranger to this customizability, offering tool ...more
Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin ...more
In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts. In the last Hacker Fundamentals, we talked about the OSI model as well as a little on TCP/IP and the protocols that make ...more
Who said you need a smartphone to use Snapchat? A new application in the Mac App Store, appropriately dubbed Snappy, allows you to send and receive Snapchats directly on your computer. Check out the guide below to learn how to go through all of your Snapchat stories, take and ...more
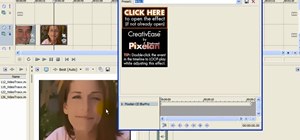
This video tutorial will teach you a simple hack that will allow you to hide a secret message in any digital picture. Who knew a picture could actually be worth a thousand words? Real words, embedded within! For detailed, step-by-step instructions on recreating this hack yours ...more
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier. Back in Android 9, Google added a feature that allowed you to w ...more
Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 2 ...more
I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase. If someone can access your wireless networ ...more
In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks. As web server and OS’s have become hardened and living behind significant perimeter defenses, hackers hav ...more
Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools a ...more
One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a les ...more
Ever accidentally sent an audio message to someone through the Messages app? It happens to me all the time. My finger slips towards the right side of the keyboard and all of a sudden a one-second audio recording is being made and sent. Personally, I don't even send audio messa ...more
Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device. Deleting your messages and pictures manually is a good to protect yourself from aver ...more
Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period. In this tutorial, though, we will be setting up a system to ...more
For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your ...more
By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions. We've spent the last few days getting to know it, and let ...more
Uploading certain pictures to Instagram can be problematic, especially when the dimensions of your picture exceed the dimensions of the square crop that's forced upon you. Why should I be forced to hack up my awesome fisheye picture inside of a lame square? I get the whole squ ...more
It seems that Apple is taking a page from Google's book with their new "Hey, Siri" voice activation feature in iOS 8. This feature mimics the one found in Google Now, the voice-activated intelligent personal assistant available to just about all Android users. Apple's version ...more
PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's comput ...more
In this article, I'll show you how to built a Wireless Transfer of Energy Transmitter. Simply put, this device will send electricity to a florescent light bulb and light it up, from up to three feet. The idea originally (at least, prominently) came from Nikola Tesla (read more ...more
If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the ...more
Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much at ...more
FV Extender for Chrome This is an extension you can download for your the Chrome browser. At this time the extension only accepts and sends back gifts but may do more in the future. See developer's site for more information, and a quick video showing this feature in action. ...more
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is down ...more
If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC a ...more
When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As every ...more
In the revamped Messages app in iOS 10, you can now send animated GIFs from your iPad, iPhone, or iPod touch without a third-party keyboard like Giphy or GIF Keyboard. Best of all, this is not just an iMessage-only feature. We tested it out and were able to send animated GIFs ...more
All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system. As I have mentioned nu ...more
I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends. Everyone who l ...more
Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a ...more
With email, one size does not typically fit all. You have multiple email accounts, each for different purposes and with varying levels of importance, so it only makes sense to customize the way your phone alerts you to each account's incoming emails. Luckily, Outlook allows yo ...more
Cheat Farm Town for unlimited gifts. Farm Town hacks, cheats, glitches. How to hack Farm Town. Description of the app on Facebook: In the world of Farm Town you and your friends can have a great time! You can play games, design, grow and maintain your own farm and even send ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
Your freezer is no one-trick pony. While it does excel at keeping your food fresh for as long as possible, it has a few secret talents it doesn't want you to know about. Like making soda slushies and pyro-friendly smoke mix, as well as reviving dead hard drives. Even better—it ...more
Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highl ...more
Seriously?! That's what a lot of people are saying when they found out that their Xbox One doesn't have a native streaming media player. When a new system is introduced and lacks features that the previous system had, it really pisses people off. The Xbox 360 allowed people to ...more
When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier. Now, I'm not saying that learning Terminal c ...more
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you ...more
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what ex ...more
In late-2017, Instagram rolled out a feature that automatically saves your ephemeral Stories to a private archive. Before that, Stories disappeared into the ether after 24 hours, but not everyone was comfortable losing these precious photos and videos. If you post to Instagram ...more
Bitcoin is a new currency built off "Satoshi Nakamoto's" (alias) 2008 Bitcoin white-paper. Bitcoin provides its users with a way to make peer-to-peer (P2P) transactions without having to use a bank as a mediator. There is no middle man, no corporation backing it, and no one ha ...more
Although the Clock app in iOS has undergone some design changes over the years, you still can't set more than one timer on your iPhone. Oddly enough, Apple's own HomePod speaker added this feature, mimicking the timer on Amazon's popular Echo smart speakers. Fortunately, throu ...more