Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal. And ...more
Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the or ...more
Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and priv ...more
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tra ...more
We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job ...more
So far in this game, my score card: 0-1 from saving a guy from coyotes. My first ever fail in the game. 0-7 from saving a woman being attacked by coyotes. I don't even try anymore. 0-2 from saving someone hanged by bandits. 1-3 from saving a person being tied and dragged out ...more
Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds. On Wednesday, Niantic began rolling out the new Trainer Battles player versus player fight mode, starting first with players level 40 and a ...more
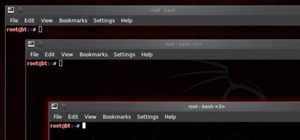
Now that we have our vulnerable server, it's time to start up BeEF. Getting Started Step 1: Running BeEF If you have Kali, BeEf comes pre-installed. You can find it in /usr/share/beef-xss/. Once you're there, type ./beef to execute the program. You will need to know both of ...more
Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading t ...more
We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to se ...more
Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this. Anonymous - What/Who Are They? A Quick introduction in case someone doesn't know what they are and who they are. Anonymous is an idea. An idea of anybody who w ...more
Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being bat ...more
Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators. ...more
Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server! Hello, it's iDwarf again! Last week's redstone trap competition was a HUGE success. We had at least 30 entries! But before we get to showing off the winners ...more
Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering att ...more
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack usi ...more
One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sen ...more
Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you include ...more
Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community. Don't be a script-kid? what do you mean? In pro ...more
We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of compani ...more
A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later. We're going to explore how it works by creating a single line that downloads and runs potentially infinite ...more
When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords. Many compatible adapters have swappable antennas, and there are several different kinds of specialized antennas you can add to a network adapter to ...more
A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network w ...more
Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily act ...more
When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games ...more
When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you ...more
Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn fro ...more
The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your iden ...more
It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something. Our rush to the future is too fast to keep up with. Denying technology is ignorance, isolat ...more
Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible. W ...more
There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help ...more
Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which mu ...more
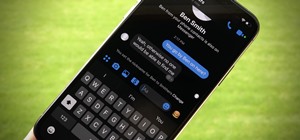
Your iPhone's Messages app has some impressive new features and changes with iOS 17, and you've probably already noticed some of them just by using the updated app. But there are less apparent features, even hidden ones, that have likely eluded you that you're going to want to ...more
On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you nee ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive. ...more
To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's ...more
Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes ...more
As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm su ...more
Super Mario Brothers! No, wait... Super Meat Boy! Yep, that's right. Meat. As in "cube" steak. As in a square piece of beef with eyes and a shitty grin, who just happens to be in love with a band-aid. I have no idea why. And no matter how shocked you are to see your dinner on ...more
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use ...more
New Year's Eve. It will be one hell of a chaotic night. Trust me. The overcrowded streets. Long lines for the urinal. Maxing out your credit card on that shot of Cuervo. You'll be lucky to make it out alive. If you do manage to stave off alcohol poisoning and survive the asc ...more
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning ...more
It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Ela ...more
Fire. It’s everywhere— always has been. From the Ordovician Period where the first fossil record of fire appears to the present day everyday uses of the Holocene. Today, we abundantly create flames (intentionally or unintentionally) in power plants, extractive metallurgy, i ...more
Mechanical locks have been around since ancient Egypt, with the oldest known artifact found in the ruins of Nineveh, an ancient city in Assyria, Mesopotamia, which is just across the Tigris River from what is now Mosul, Iraq. It was a forerunner to our modern-day pin tumbler ...more
If you're having difficulty dispatching any of the Corrupted from 2008's Prince of Persia, this helpful battle guide from IGN might be just what you need. If forewarned is forearmed, this video tutorial will arm you to the teeth with the necessary knowledge to beat each of Ahr ...more
Getting a lightshow from one person at a rave is crazy, enough, but where they really start to get crazy is when people do duo lightshows. In a duo, one person stands over and behind the crouching main person giving the lightshow, complementing their show above them. Watch thi ...more
Everyone talks about Minecraft and Logic Gates all the time and the various uses for red stone, heck, someone even made a fully useable calculator! But using Red Stone takes a special kind of math and logic that some may be confused about. In this video you will learn the basi ...more
This is the set up I use for the straight jacket submission when someone defends the gogoplata. This submission attacks the shoulders depending on how flexible you are. There are a couple of ways to set this up.
You may have come across Chloe Bruce in the past, but we're betting it was on the web, because if it were in person, you probably wouldn't be reading this right now. Because in a blink of an eye, she'd have her foot smashed against your face using her world famous Scorpion Kic ...more
The receiver of the wedgie, would by laying on he ground, preferably face down, with they're underpants securely fastened to some strong cord, at each hip. The cord, would be then tied to the pegs of a BMX bicycle ( if you wished to extreme it up a little you could use a motor ...more
Are your boobs not cutting it anymore? How do you increase your bust size without plastic surgery? There are some tricks and tips to acquiring more cleavage, so watch and learn. Your rack will thank you. So will the guys. Pursebuzz reveals the secret behind maximizing your br ...more