Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the w ...more
Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that tr ...more
The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defund ...more
Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbl ...more
After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared. Hidden within the iOS 11.4.1 update is the new USB Restricted Mode that Apple introduced in the iOS 12 beta which ...more
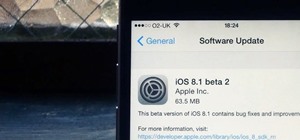
Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more ...more
Welcome back, my budding hackers! One of the keys to being successful as a hacker, pentester, or cyber warrior is the ability to find vulnerabilities or flaws in the target system, which are what we exploit when we hack. We have looked at several ways to do that including var ...more
Here I will show you how to properly dig information on the web that has already been published, you just dont know it. Where Am I Going with This? Well, as many of you might or might not know, many and I mean many people do actually keep info on their profiles that they do ...more
It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?). SSLStrip and the HSTS Chronicles ...more
Prison Architect, the BAFTA winner for the Best Persistent Game in 2016, has finally soft launched on iOS. Originally a PC game, Prison Architect lets you build and maintain a maximum security prison. Comparable to running a small city, the game has you manage an ever-expandin ...more
Fans of rhythm tap games and traditional one-on-one fighters finally have something to bring them closer together. DuelBeats, a fighting game that lets you perform moves by tapping to the beat of a song, has been released as a soft launch for both iOS and Android in New Zealan ...more
Fans of fighting game series such as Street Fighter and Mortal Kombat are in for a treat! Skullgirls has entered the crowded field of the mobile fighting genre and has touched down in the form of a soft launch for iOS devices, which is now available for download in Canada and ...more
Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the sca ...more
One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web. But with this great power, it seems that Spotlight collects your ...more
The Autobots and Decepticons are back as Transformers: Forged to Fight has soft-launched for both iOS and Android. Help Optimus Prime fight corrupted Transformers one on one to save them from their ruthless overlords, and have them join your cause, regardless of which side the ...more
NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receive ...more
Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or ...more
Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the b ...more
Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent ...more
I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still ...more
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment. Using a directional Wi-Fi antenna and Wireshark, we can create a display filter to target any device in range to plot the signal strength on a gra ...more
Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, ...more
You may have heard of Honor of Kings, the multiplayer online battle arena game so popular that it has the potential to do for mobile what League of Legends has done for the PC in the world of competitive online gaming, but you'll soon hear about its western iteration, Strike o ...more
A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA ...more
Opera's web browser for Android, Opera Mini, now comes with integrated ad-blocking technology for a less cluttered browsing experience. More importantly, it decreases the amount of data being loaded, which Opera claims increases webpage loading times by 40 percent. This is in ...more
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target. Thanks to a pair of recon tools coded in Python, it takes just seconds to research how a website or server might be vulnerable. No matter what platform ...more
With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Pyth ...more
In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users. On Friday, furniture retailer Houzz, an early adopter of ARKit, revealed details of a data breach that occurred in December 2018. ...more
Though Google and Apple have released their own software-based toolkits for AR, components suppliers continue to advance their technology to better support AR experiences on the hardware side. The latest example comes from LG Electronics, who have partnered with signal proces ...more
Hi there, nullbytes! I've been recently using NullByte as my only source of learning (almost) and it has proven to be really good to me. I've compiled some of the articles about networking, and ordered them in a way that made sense to me, and I thought about sharing the list ...more
Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configur ...more
Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to in ...more
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manuf ...more
Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis c ...more
Apps can learn a lot about you just by reading information about your smartphone. They can easily track what device model you have, your phone number, and in some cases, your hardware MAC addresses. Many third-party apps will only track your device values for advertising purpo ...more
Talking Tom has long been mesmerizing children of all ages with his ability to repeat words and phrases and encourage touch interactions. Now, the lovable cat and his band of cuddly friends have ventured into the endless runner genre as heroes bent on saving Angela and their c ...more
In an ongoing effort to improve its services and become more accessible to users from all regions, Facebook has released a streamlined version of its social media app. Though the leaner Facebook Lite is only officially available in Turkey for now, there's a simple workaround y ...more
Despite the abundance of sci-fi titles in the iOS App Store, very few of these mobile games ever have the staying power keep us glued for more than a few hours. Enter Space Pioneer, an awesome space exploration game that soft-launched in Canada ahead of a worldwide debut. With ...more
With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-la ...more
One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched ...more
Mobile gamers who grew up on J.K. Rowling's fantasy epic have yet another reason to rejoice, as Jam City's Harry Potter: Hogwart Mystery is slated to touch down on both iOS and Android on April 25. But if you can't bear the wait, there's a little hack you can do to give the ga ...more
Disruptor Beam just soft launched The Walking Dead: March to War in the Philippines. It's not officially available in the US yet, but there are ways to play this take on Robert Kirkham's post-apocalyptic masterpiece regardless of where you live. The Walking Dead: March to War ...more
Prepare yourself for a trip back to the days when a Sega Genesis was your gateway to premium gaming. The mid-nineties classic, Comix Zone, has been soft-launched in the Philippines, and while it's not officially available for gamers in the states, you can install it right now ...more
Based in the DC Universe, Injustice: Gods Among Us was a runaway success on the iOS App Store, generating enough downloads to rival its console-based iteration in terms of popularity. But now, the sequel to this long-running game, Injustice 2, is finally out in the wild, as it ...more
Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is. You want to get rid of him, but you need some proof first. Step 1: Fire Up Kali If yo ...more
Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc. You can also use this technique to hack/spoof messengers like Facebook or WhatsApp etc. Step 1: Fire-Up Kali: I hope you know how to hack android and gain access t ...more
With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun. This is the case with the latest offering from the development team at Privax. Their ap ...more
Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons. We need to keep a close eye on him, so in ...more
The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack usi ...more
Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information. B ...more
There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea. StartHost covers all the bases. With a lifetime subscription, you'll get access to its pre ...more
Augmented reality optics maker WaveOptics has just infused its operations with a fresh round of funding to facilitate its objective of bringing consumer-grade smartglasses at a $600 price point to market in 2019. On Tuesday, the London-based company announced that it has clos ...more
Though not as popular as Super Mario or Zelda, Konami's Contra nevertheless remains as one of the greatest titles that helped put Nintendo on the map. This retro shooter is set to make a comeback, and has been soft-launched in select Asian countries ahead of a worldwide releas ...more
Massive multiplayer shooters like Fortnite have become all the rage, as mobile gamers duke it out in long, protracted battles that can often be as excruciating as they are thrilling. If you're yearning for a more fast-paced shooter on iOS, Nitro Games has you covered, and has ...more
The Power Rangers universe is massive, spanning numerous shows and movies that feature different heroes — from the original dinosaur-themed Mighty Morphin Power Rangers, to Power Rangers Samurai, and so on. To tie it all in, Nexon has soft launched Power Rangers: All Stars in ...more
Marvel's Future Fight gave gamers the ability to brawl through near-countless levels as their favorite superhero. Not to be outdone, DC has soft launched DC Unchained in select Southeast Asian countries in preparation of a worldwide debut. If you're willing to put in a little ...more
Despite numerous reports announcing its stateside arrival, "Final Fantasy Awakening" has yet to show up in the iOS App Store, much to the chagrin of millions of fans in the U.S. Unfortunately, the game seems to be stuck in soft-launch limbo, with no word as to when it'll land ...more
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by thi ...more
Mobile gamers are well aware of this, but zombie shooters have become pretty stagnant and unimaginative in recent years. Too many entries in this genre feature the same cookie-cutter gameplay, but thankfully, Gameloft aims to change this. The company has soft-launched Dead Riv ...more
Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless ...more