Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with. Wardriving has been around since the '90s and combines GPS data and Wi-Fi signal data to create accurate, in-depth maps of any nearby Wi-Fi networks ...more
It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to interce ...more
It may be intended as a toy, but this gizmo can be hacked for more than just watching a remote-controlled car's video spy cam. This HUD (heads-up display) comes with the Wild Planet Spy Gear Video Car, but it's said that you can purchase the video headset separately. And it's ...more
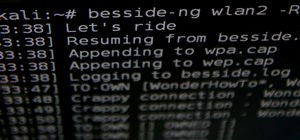
Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting ...more
In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, ...more
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby devi ...more
A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attac ...more
Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?" Capturing these incident ...more
|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcas ...more
When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but als ...more
Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!) In several episodes, Elliot was seen sending ...more
The biggest problem with Netflix (which is hardly a real problem) is the overwhelming amount of content available for streaming. Browsing through profile-specific categories might help narrow down your search on something to watch, but some of those categories come and go with ...more
The new 007 film, Skyfall, comes out this Friday, and dreams of becoming a super-spy have taken over my mind. Only I can't afford any of James Bond's awesome gadgetry or amazing cars—and you probably can't either. But that doesn't mean you can't fake it a little by adding a t ...more
Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning ...more
This video shows you how to set up a mini wireless spy cam. Where you put it is up to you. Who you spy on is up to you. If you're wanting to keep an extra set of eyes on someone, watch and learn. So whether you're looking to put a camera in your bathroom or garage, go for it.
There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Sn ...more
OK master spy, it's time to get your lurk on. If you're going to be spying, you'll need to be able to spy at night. This video will show you how-to make your very own night vision goggles so you can keep up with your mark well after the sun goes down. You'll need a 9V battery, ...more
As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent. ...more
Apps can collect a lot of data. Even if they don't have permission to access your GPS or camera, they can still read other sensors and learn a lot more than you'd think. Your gyroscope could be used as a keylogger. The light sensor could read your visited links. But if you're ...more
If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is wh ...more
The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples ...more
SharePlay is arguably one of the most significant features to hit FaceTime since group calls, and it's still hard to find apps that support shared experiences in FaceTime. Apple does list a few apps, but there is no official index of all the apps with SharePlay integration. Th ...more
Destroy Black Ops Noobs First of all, these tips are great for any consoles that run Black Ops. Whether it be your Sony PS3, Nintendo Wii, XBox 360 or your PC. Internet Connection Before you put the game in to your console, make sure that your internet connection is consist ...more
One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a ...more
Welcome back, my nascent hackers! One of the many reasons I write this blog is to help you keep the Internet free and open. Throughout human history, whenever a government or other powerful entity has wanted to subjugate a people or group, the first thing they do is isolate t ...more
It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no mat ...more
WonderHowTo loves gadgets. We also tend to enjoy getting our hands (just a little bit) dirty. So, naturally, Brando's Wall Hook Coat Hanger Camcorder is the latest gadget to excite. Disguised as a coat hanger, the device is actually a camera triggered by motion detection. And ...more
Need to pass along an important message on paper without having it accidentally discovered by your archenemy? Using very common household products, you can easily whip up an invisible ink recipe and write out your secret message with the solution. All the recipient needs to do ...more
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private cha ...more
MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the com ...more
When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called r ...more
Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it a ...more
Want to bug a room on the cheap? This video how-to demonstrates how to make a simple eavesdropping device using a cell phone with auto-answer support and conventional plug-in type headset. For detailed advice on setting up this expedient spy bugging device, consult this friend ...more
Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a si ...more
You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other co ...more
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information i ...more
If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exac ...more
Certain files contain sensitive data that you don't want being shared with just anybody. Even still, it would be nice to be able to send such a file to a certain confidante without fear of it falling into the wrong hands. The Digify development team had all of this in mind wh ...more
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Duc ...more
A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts f ...more
Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and ho ...more
This tutorial illustrates how a wireless pinhole spy video camera can jam wireless internet or WiFi signals.
Imagine that every time you print a document, it automatically includes a secret code that could be used to identify the printer -- and, potentially, the person who used it. Sounds like something from a spy movie, right? Unfortunately, this scenario isn't fictional. Most colo ...more
Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL ph ...more
Zynga just added another game to their Zynga with Friends series called Scramble with Friends. If you've ever played Boggle, it's basically the same thing, but is dedicated to playing your buddies just like Words with Friends or Hanging with Friends. Chances are you've alread ...more
While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we ha ...more
Night vision goggles are one of the iconic pieces of equipment of the modern military. Getting a real pair is prohibitively expensive, especially if you just want to use it as a prop in your film instead of actually seeing at night. This video features instructions for making ...more
The pumpkin is everyone's favorite cucurbit come Halloween time, and while there are only a few types of Halloween-friendly pumpkins out there, there is definitely no shortage of what you can do with them. You can carve faces into them, perform brain surgery, make them sing, ...more
Since iOS 11, a thumbnail preview appears on your iPhone whenever you take a screenshot. It's useful for access to quick sharing options and editing tools, but you can't disable the preview image. You can wait for it to disappear or swipe it off-screen, but that's as good as i ...more
Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long ...more
The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely. The sheer volume of Windows computers currently in operation around the world ...more
Kip Kay, from Make Magazine, shows you how to take your radio controlled vehicle and turn it into a spy car, by mounting a camera onto it. Follow Kip, as he shows you how to remove the body from your radio controlled car, mount the camera inside the chassis using the triPod mo ...more
I'm sure everyone has heard about Google's changing privacy policy on March 1. It's scattered everywhere, with notification bubbles on Google Search, YouTube, and the rest of their products. Click here to see the new privacy policy that will take effect on March 1, 2012. What ...more
Secretly shoot your voice across the room in stealth mode on a laser beam in this fun and easy project! Make Magazine and Kipkay present this cool spy trick. Build a simple laser communicator that transmits your voice across a room. You need an amplifier, radio, laser pointer, ...more
Your iPhone has a powerful feature that can keep your secrets hidden from other people, and you'll never have to worry about sharing or showing someone something embarrassing or incriminating ever again. No matter who you are, you likely use your iPhone's Photos app a lot sin ...more
You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discove ...more
What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden eme ...more
Staying inside during the coronavirus pandemic isn't easy for most of us. As important as it is to keep away from others, it can be challenging to keep to ourselves day after day. That's why mobile game developers are stepping in to help; many are making their games free for a ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking. Before I begin, I want to re-emphasize to all of y ...more