How To : Fake your ip address to stay anonymous
This video will show you a few easy steps to remain anonymous on the Internet by replacing your ip address for a fake one.

This video will show you a few easy steps to remain anonymous on the Internet by replacing your ip address for a fake one.
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you ho ...more
Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes. But while Tor is great for desktop users, since they can simply install a Tor browser or plugin, it's a bit more c ...more
The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your iden ...more
There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely s ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This ...more
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online? May be you are an vigilante hacker like me? or You don't want companies logging your Data (Also like me ...more
Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this. Requirements: -Web Browser Firefox or Iceweasel In Google Chrome you will have to add an extension called WebRTC Leak Preven ...more
We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm her ...more
Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in t ...more
Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks ...more
This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of othe ...more
We all know them, and many of us despize them. And some might support them, regardless many have different opinions. NSA: Who Are They? They are people who believe in them having access to everybody and all data that exists in the digital world. (In a nutshell) They work wi ...more
Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay a ...more
When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll. Anonymity can also be important when sending a mess ...more
As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you ca ...more
My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along. Disclaimer: I didnt introduce you this subject in my last post, but I while do that now. First, I want to clarify that t ...more
As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfor ...more
Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn ...more
As you may or may not know, MegaUpload - one of the largest file sharing services has been taken down by the feds. To us - this means no more 1gb free downloads. And we move onto MediaFire and Rapidshare. - But more importantly, this means that our inherent freedom to share f ...more
Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience. You Will Need: * Inquisitiveness * Knowledge ...more
You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images ar ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonym ...more
Here at Null Byte, we try to inform and teach the community on ways to navigate the Internet in that special way, as well as staying safe along the trip. That being said, I need some help from all of you! There is a lot of information to cover and I know we have some smart use ...more
I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an ...more
Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut d ...more
We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web. However, I should ...more
For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself ...more
If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. More amazing community contributions this w ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this. Anonymous - What/Who Are They? A Quick introduction in case someone doesn't know what they are and who they are. Anonymous is an idea. An idea of anybody who w ...more
This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments. First of all, it was pretty disappointing to see that there is nothing on 'Cryptocurrency' on Null Byte, owing to the fact that how convenient, digital, anonymous ...more
You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series: I am continuing this series for those of you whom didnt know I had one of these going. Follow up on this series by searching in the search by Your Re ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the commu ...more
Facebook is where a lot of people get their news. The problem, though? Your Facebook feed gets jumbled with random post times, which isn't useful for keeping up with new stories in real-time. Even if you're not after the news or stories, you might want to see when your Facebo ...more
Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed ove ...more
Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/) Now I know that there is already a foru ...more
With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And whi ...more
If the rumors are right, Microsoft has decided to cancel the second version of the HoloLens, and they will instead move onto version three of their mixed reality headset. In the latest report, Thurrott's Brad Sams states that the expected release date of this new Windows Holog ...more
Part 1: What is Popcorn Time? Part 2: What is a torrent? Part 3: Why am I at risk? Part 4: What is a VPN? Part 5: Are all VPNs the same? Part 6: How do I stay protected? Part 1: What Is Popcorn Time? Popcorn Time is, essentially, a torrent client (look to Part 2 for further ...more
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturall ...more
Imagine that Tinder fornicated with Facebook and had a baby. The product of that union would be the hideous, yet overwhelmingly interesting SocialRadar, an app dedicated to stalkers and stalkees. Video: . Only other SocialRadar accounts can view your profile, but the app relie ...more
When LinkedIn first arrived on the scene, I thought it was a great resource for staying connected and getting in touch with those people in your desired career path. Keyword: Thought. Like most businesses, money and shareholders seem to have taken over the driver's seat, pushi ...more
I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is espe ...more
During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform O ...more
Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep thi ...more
Reports of Zika-related birth defects are coming in at shockingly low rates in Puerto Rico. While that might be something to cheer, one former US government official is saying there could be a nefarious reason for the low numbers. Last July, the Puerto Rico Department of Heal ...more
Most people keep their ungodly sexual desires deep inside, only to be indulged in private on their computers. It makes you wonder... what secrets do your neighbors have? What kind of porn are they watching? And how much and for how long? Thanks to some public (and anonymous) d ...more
In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Mak ...more
Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Intern ...more
A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simpl ...more
Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby. The X divi ...more
So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you. Introduction Part: So this is a serious only about being anonymous on the internet and while hacking. This series will cover: (further steps might be added if I decide ...more
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law. In the United States (Where I live), the government will get involved in almost ...more
From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which e ...more
Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts ...more
 How To:
Export or Import Your Safari Browsing Data Between Browsers on iPhone, iPad, and Mac
How To:
Export or Import Your Safari Browsing Data Between Browsers on iPhone, iPad, and Mac
 How To:
The Complete iOS 18.2 Features Guide — Here's Everything New and Improved for Your iPhone
How To:
The Complete iOS 18.2 Features Guide — Here's Everything New and Improved for Your iPhone
 How To:
Set a Maximum Volume Limit for Your iPhone or iPad's Speakers to Prevent Loud Audio Surprises
How To:
Set a Maximum Volume Limit for Your iPhone or iPad's Speakers to Prevent Loud Audio Surprises
 How To:
13 Ways iOS 18 Improves Your iPhone's Camera App for Even Better Photos and Videos
How To:
13 Ways iOS 18 Improves Your iPhone's Camera App for Even Better Photos and Videos
 How To:
Apple Just Added Sudoku to Apple News — Here's How to Play It on iPhone, iPad, and Mac
How To:
Apple Just Added Sudoku to Apple News — Here's How to Play It on iPhone, iPad, and Mac
 How To:
Unlock the Power of Visual Intelligence on Your iPhone to Translate and Explore the World Around You
How To:
Unlock the Power of Visual Intelligence on Your iPhone to Translate and Explore the World Around You
 How To:
Generate Professional Drawings in Seconds Using Image Wand on iOS 18.2 or iPadOS 18.2
How To:
Generate Professional Drawings in Seconds Using Image Wand on iOS 18.2 or iPadOS 18.2
 How To:
Use Genmoji to Create Custom Emoji That Work Just Like Regular Emoji in Messages, Notes, and More
How To:
Use Genmoji to Create Custom Emoji That Work Just Like Regular Emoji in Messages, Notes, and More
 How To:
Make Typing Text Easier to Read on iPhone, iPad, or Mac with Apple's Hover Typing Tool
How To:
Make Typing Text Easier to Read on iPhone, iPad, or Mac with Apple's Hover Typing Tool
 How To:
Change the Default Web Browser App on Your iPhone to Open Links in Chrome, Firefox, Safari, and More
How To:
Change the Default Web Browser App on Your iPhone to Open Links in Chrome, Firefox, Safari, and More
 How To:
Use Apple Intelligence's Image Playground to Craft Custom Drawings and Animations for Almost Anything You Can Think Of
How To:
Use Apple Intelligence's Image Playground to Craft Custom Drawings and Animations for Almost Anything You Can Think Of
 How To:
Follow the 2024 Election Results in Real Time with Apple News' Live Activity for iPhone, iPad, and Apple Watch
How To:
Follow the 2024 Election Results in Real Time with Apple News' Live Activity for iPhone, iPad, and Apple Watch
 How To:
Experience Music on Your iPhone Like Never Before with Music Haptics, Which Lets You Feel Every Beat
How To:
Experience Music on Your iPhone Like Never Before with Music Haptics, Which Lets You Feel Every Beat
 How To:
Generate Text, Images, and Insights with Apple Intelligence's Built-in ChatGPT Integration
How To:
Generate Text, Images, and Insights with Apple Intelligence's Built-in ChatGPT Integration
 How To:
Remove Unwanted Objects, People, and Distractions in Photos on Your iPhone, iPad, or Mac
How To:
Remove Unwanted Objects, People, and Distractions in Photos on Your iPhone, iPad, or Mac
 How To:
New Menu Lets You Set Default Apps on Your iPhone or iPad for Calling, Messaging, Emailing, Web Browsing, and More
How To:
New Menu Lets You Set Default Apps on Your iPhone or iPad for Calling, Messaging, Emailing, Web Browsing, and More
 How To:
30 Must-Know New Features in iOS 18.1 and iPadOS 18.1 That'll Make You Want to Update
How To:
30 Must-Know New Features in iOS 18.1 and iPadOS 18.1 That'll Make You Want to Update
 How To:
Easily Record Phone Calls on Your iPhone and Get Auto-Generated Transcripts and Summaries
How To:
Easily Record Phone Calls on Your iPhone and Get Auto-Generated Transcripts and Summaries
 How To:
The Complete iOS 18.2 Features Guide — Here's Everything New and Improved for Your iPhone
How To:
The Complete iOS 18.2 Features Guide — Here's Everything New and Improved for Your iPhone
 How To:
See Passwords for Wi-Fi Networks You've Connected Your Android Device To
How To:
See Passwords for Wi-Fi Networks You've Connected Your Android Device To
 How To:
Export or Import Your Safari Browsing Data Between Browsers on iPhone, iPad, and Mac
How To:
Export or Import Your Safari Browsing Data Between Browsers on iPhone, iPad, and Mac
 How To:
Remove Unwanted Objects, People, and Distractions in Photos on Your iPhone, iPad, or Mac
How To:
Remove Unwanted Objects, People, and Distractions in Photos on Your iPhone, iPad, or Mac
 How To:
20 Surprisingly Practical Uses for Apple AirTags
How To:
20 Surprisingly Practical Uses for Apple AirTags
 How To:
Clone Any Android App on Your Samsung Galaxy Phone Without Using Any Third-Party Tools
How To:
Clone Any Android App on Your Samsung Galaxy Phone Without Using Any Third-Party Tools
 How To:
Keep Your Night Vision Sharp with the iPhone's Hidden Red Screen
How To:
Keep Your Night Vision Sharp with the iPhone's Hidden Red Screen
 How To:
Expired or Still Good? The Quickest Way to Test Baking Soda & Baking Powder for Freshness
How To:
Expired or Still Good? The Quickest Way to Test Baking Soda & Baking Powder for Freshness
 How To:
Unroot & Revert Your OnePlus 5 or 5T to 100% Stock
How To:
Unroot & Revert Your OnePlus 5 or 5T to 100% Stock
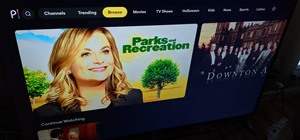 How To:
Does the Picture Look Weird on Your Chromecast with Google TV? Here's a Fix
How To:
Does the Picture Look Weird on Your Chromecast with Google TV? Here's a Fix
 How To:
Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
How To:
Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
 How To:
Make Siri Say Whatever You Want Every Time You Connect Your iPhone to a Charger
How To:
Make Siri Say Whatever You Want Every Time You Connect Your iPhone to a Charger
 How To:
Fold an Origami F-18 Fighter Jet Out of a Dollar Bill
How To:
Fold an Origami F-18 Fighter Jet Out of a Dollar Bill
 How To:
Dial These Secret Codes to See if Someone Is Hijacking Calls & Texts on Your iPhone
How To:
Dial These Secret Codes to See if Someone Is Hijacking Calls & Texts on Your iPhone
 Android Basics:
How to See What Kind of Processor You Have (ARM, ARM64, or x86)
Android Basics:
How to See What Kind of Processor You Have (ARM, ARM64, or x86)
 How To:
100+ Secret Dialer Codes for Your iPhone
How To:
100+ Secret Dialer Codes for Your iPhone
 How To:
The Ultimate Potato Cheat Sheet: Which Potato Goes Best with What?
How To:
The Ultimate Potato Cheat Sheet: Which Potato Goes Best with What?
 How To:
Download and Install iOS 18.3 Beta or iPadOS 18.3 Beta to Try New iPhone or iPad Features First
How To:
Download and Install iOS 18.3 Beta or iPadOS 18.3 Beta to Try New iPhone or iPad Features First
 How To:
Are Your Devices Compatible with iOS 18, iPadOS 18, and macOS 15? Here's the Complete List
How To:
Are Your Devices Compatible with iOS 18, iPadOS 18, and macOS 15? Here's the Complete List
 How To:
Download & Watch the Original Star Wars Trilogy Unaltered
How To:
Download & Watch the Original Star Wars Trilogy Unaltered
 Holiday Project:
Origami Christmas Trees
Holiday Project:
Origami Christmas Trees
 How To:
19 Messenger Tips for Mastering Video Chats & Group Video Calls
How To:
19 Messenger Tips for Mastering Video Chats & Group Video Calls
 How To:
Create and understand the wet sand effect
How To:
Create and understand the wet sand effect
 How To:
Get Willow Smith's Trendsetting "Whip My Hair" Hairstyles
How To:
Get Willow Smith's Trendsetting "Whip My Hair" Hairstyles
 How To:
3 Ways to Unlock Your Samsung Galaxy S8 Faster — Without Using the Fingerprint Scanner
How To:
3 Ways to Unlock Your Samsung Galaxy S8 Faster — Without Using the Fingerprint Scanner
 How To:
16 Harry Potter Spells for Siri That Turn Your iPhone into a Magical Elder Wand
How To:
16 Harry Potter Spells for Siri That Turn Your iPhone into a Magical Elder Wand
 How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
 How To:
Create an Admin User Account Using CMD Prompt (Windows)
How To:
Create an Admin User Account Using CMD Prompt (Windows)
 How To:
Clear Your Frequently Used and Recent Emoji from Your iPhone's Keyboard
How To:
Clear Your Frequently Used and Recent Emoji from Your iPhone's Keyboard
 How To:
Use Odin to Flash Samsung Galaxy Stock Firmware
How To:
Use Odin to Flash Samsung Galaxy Stock Firmware
 How To:
Test Your Samsung Phone by Using Secret Code *#0*#
How To:
Test Your Samsung Phone by Using Secret Code *#0*#
 How To:
19 Harry Potter Spells Your Android Phone Can Cast Using Google Assistant
How To:
19 Harry Potter Spells Your Android Phone Can Cast Using Google Assistant
 How To:
If 'Messages' Consumes Too Much iPhone or iCloud Storage, Don't Delete Your Conversations Just Yet
How To:
If 'Messages' Consumes Too Much iPhone or iCloud Storage, Don't Delete Your Conversations Just Yet
 Modular Origami:
How to Make a Cube, Octahedron & Icosahedron from Sonobe Units
Modular Origami:
How to Make a Cube, Octahedron & Icosahedron from Sonobe Units
 How To:
13 Tips Every Apple Pencil User Needs to Know for iPad
How To:
13 Tips Every Apple Pencil User Needs to Know for iPad
 How To:
Prevent Thieves from Turning On Your iPhone's Airplane Mode, So You Have a Better Chance to Track It Down
How To:
Prevent Thieves from Turning On Your iPhone's Airplane Mode, So You Have a Better Chance to Track It Down
 How To:
The Complete Guide on How to Build a Crystal Radio—Plus How They Work
How To:
The Complete Guide on How to Build a Crystal Radio—Plus How They Work
 How To:
Turn Your Gag Reflex Off with Pressure Points
How To:
Turn Your Gag Reflex Off with Pressure Points