By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe". Michigan's police department h ...more
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a c ...more
Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive infor ...more
You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony). ...more
Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm ...more
This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project ...more
Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the ta ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly ...more
Self portraits are a wonderful way to give viewers a sense of a photographer's taste and personality. And contrary to popular belief, they do not have to be as cliché as using the reflection of your bathroom mirror. There are plenty of different creative approaches one can tak ...more
I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase. If someone can access your wireless networ ...more
Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites. Luckily ...more
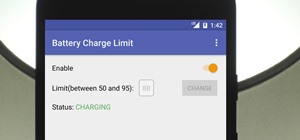
For those who need security on their Android devices, the standard swipe lock screen just isn't enough, so it's necessary to install applications like GOTO and WidgetLocker to enable either pattern, password or PIN protection. This protection is great overall, but when you're ...more
Ever had your car broken into? Or worse, your apartment? Ever been pickpocketed? Handheld electronics—iPods, iPhones, iPads, GPS devices, digital cameras—are easy to snatch, light to carry, and useful to most. And when they're gone, they're gone. Until now. Thanks to develope ...more
If you have any Google applications, like Gmail or Google Calendar, that you want to sync to your new Android enabled mobile phone, it's a simple task to complete. There's nothing hard about it, but if you think you need help, Best Buy has answers. The Best Buy Mobile team exp ...more
As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach. Global Payments is just one of the mid ...more
No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the In ...more
I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonym ...more
You may have already heard of Zazzle, an online service that allows you to print on a variety of goods (tees, mugs, posters, etc.). You can design-it-yourself, or choose from Zazzle's library of available designs. Of late, Zazzle has partnered with Keds to offer something a b ...more
Have an old bike combination lock that you can't remember the code for? If it's a simply four-digit cable lock, you can easily figure out the combination with a quick peck-and-go method. Best of all, this technique doesn't require any tools or special know-how, and let's you r ...more
In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then a ...more
Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says tha ...more
A few weeks ago I wrote about Atomic Web as the best web browser for iOS devices, and while I believe it is a superior option, Atomic Web is not the only alternative web browser you can use on your iOS device. There are three more—Dual Browser, iCabMobile, and iSwifter—that ar ...more
Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared E ...more
Hello everyone and welcome to Part II - The Ultimate Guide: Diagnosing & Fixing Connection Issues. In this tutorial we will discuss more advanced methods that I took in order to fix our home network. I have also attached a link to download the FREE eBook - so feel free to down ...more
WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Hacking, crafting, mining & more… just another ...more
Last week, I started a weekly feature on Scrabble World called Scrabble Challenge, where you can solve a few (hopefully) challenging word puzzles. Normally, these will be on Fridays, but today I have a potentially unsolvable puzzle for you to try and solve, in addition to the ...more
Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as th ...more
We all remember the controversy of SCRABBLE Trickster back in April. SCRABBLE + Mattel + Proper Nouns = BLASPHEMY! Some thought it was just a PR hoax, something to rattle the bones of diehard SCRABBLE players, like myself. Others thought it was an April Fools' Day joke. But ...more
Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But w ...more
Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information y ...more
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not ...more
I love SCRABBLE, but sometimes it's hard to find an opponent who'll play a classic, tournament style game in person. Don't get me wrong—I play on the computer and iPhone all of the time, but it's just not the same as an in-person match. This leads me to stray every now and the ...more
In our media-enriched world, past and present, SCRABBLE has made a name for itself, whether deliberately, subconsciously, or influentially. You may have a read a book that had the popular word game within a chapter, watched a movie that showed your favorite characters bringing ...more
Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user. As most of you know, authentication into secure computer systems ...more
If your facebook account was hacked by someone and you really want it back this tutorial would help you get it back. Step 1: First goto this link. https://www.facebook.com/hacked Click the button "Your account has been Compromised". Then type in your email address, Login nam ...more
Forgot the passwords to your email or your other favorite websites? If you typically store your passwords in Internet Explorer (IE9 or other versions) it can be tricky to get your passwords back -- but this tutorial makes it really easy! Step 1: Watch the Video See the demon ...more
You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down. There are a surprising number of new privacy and security-related issues in iOS 7's default settings, from allowing A ...more
Monday has been a big update day for Apple. Alongside the release of iOS 10.3, iWork has been updated across both iOS and macOS. The biggest change is the ability to unlock password-protected files with Touch ID, either on iPhone and iPad, or on the new MacBook Pro with Touch ...more
Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, t ...more
Whether you want to edit photos, compress files, play games, or DJ your next party, there's a free Mac app that can help you out. But things can get annoying real fast if you download a lot of free apps from the Mac App Store, since you have to type in your Apple ID password e ...more
In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users. On Friday, furniture retailer Houzz, an early adopter of ARKit, revealed details of a data breach that occurred in December 2018. ...more
Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expa ...more
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity! Social Eng ...more
Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 millio ...more
If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal inf ...more
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you h ...more
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not ...more
Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc. You can also use this technique to hack/spoof messengers like Facebook or WhatsApp etc. Step 1: Fire-Up Kali: I hope you know how to hack android and gain access t ...more
In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent. It's been rulings like these and their call for internationally recognized rights to pr ...more
They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Lik ...more
Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software b ...more
SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET. Step 1: Select Your Target! The First Thing You're Going to Want to Do Is Select the Site Login ...more
Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a compute ...more
Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent ...more
In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, ...more
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just ...more