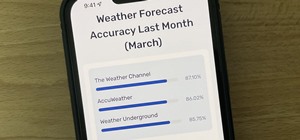
If you have a Mac running Mountain Lion, I'm sorry to tell you that all it takes to crash almost any app on it is eight little characters. This strange bug seems to only affect Mountain Lion and doesn't cause your computer any harm. Apparently, it even crashes the error report ...more
If you are like me and you have a old iPhone and you don't want to buy a new one, you can fake your ios version by fallowing this tutorial. Just to be safe i am not responsible for what you do with this or if you mess up and wreck your phone. Plus ios and iPhone all belong to ...more
Hello again, faithful readers. For today's lesson, we will be learning the correct way to restring and tune an electric guitar. I almost wasn't going to post this because it is so basic. But, as with many basic tasks, there are a lot of people who know how to do it, but can't ...more
Have you ever run across a Facebook post that you don't necessarily want to "Like," but you're not really passionate enough about to bother stringing together a couple words for a comment? Well, you're in luck, as Facebook added five new "Reactions" that let you do more than j ...more
You just bought a new loose-knit sweater, slipped it on, and your ring, earring, smartwatch, or even your fingernail snagged a piece of thread yanking an entire loop loose in the fabric. It's happened to me more times than I can remember, and if you cut that eyesore away you'r ...more
This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article ...more
Learning to make giant bubbles for this video has been the most fun I've had with a project in a long time. It's addicting to try to get them to grow bigger and bigger than the ones before. Since filming this video, my skill has improved tremendously and the bubbles you're abo ...more
Assuming everyone knows of the recent "String of attacks" passed between Obama and Romney, I just want to talk about how useless this entire thing is. I'll try to be as un-biased as possible. Election year is a major phenomenon in any country. The masses pick their candidate ...more
After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vul ...more
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on. Even though people are the weakest form of security, some o ...more
Sometimes it's the little things that make our days better, like finding a dollar in our recently washed jeans or a box of donuts in the lunch room. But your Nexus 7 tablet's lock screen isn't typically one of those things—it's just a lock screen after all. Unless you add cus ...more
Video: . Today I bring you my first Christmas themed video!Here there are some DIY ideas to decorate your room for the holiday season. They are really easy and affordable so I hope you like them! The first one is really really simple and you will need: A glass vase Golden gli ...more
Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified. This attack assumes the Wi-Fi password to the ...more
Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a ...more
Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry. As Microsoft prepares to unleash the sequel to original HoloLens, Meta Company has crashed and burned, as the ...more
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain. I figured, the more tuts the better, as I had trouble learning assembly in the beginning and had to read alot of tutori ...more
After you have registered to this site,sign in then to start missions. Basic Missions as you see in the pic in the challenges you can choose any missions but i start from basics. after you go to basic missions(it contains 11 missions) you will see this pic. go to basic 1 St ...more
A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data ...more
Using fresh herbs can make a huge difference in almost any dish, but they're not always available everywhere. Depending on where you live, you can't always get them during the colder months. Personally, the problem I run into the most is not being able to use fresh herbs befor ...more
Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching f ...more
Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL in ...more
Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code. My code can be found here -> http://pastebin.com/2nYicFPM ***************************** Index: $->Keyword !->Start of code ^->End of code *** ...more
Unless you like boxed wine, your wine bottles are going to either be sealed with a cork or a screw cap, the latter of which should not be frowned upon, especially if it's white wine. However, most wineries still prefer corks over screw caps, and that means you'll need a corksc ...more
Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then. The idea is to write simple scripts ...more
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them. While this automation does make your life a little easier, it ...more
Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short. Ma ...more
From Time Machine to Cartoon 3D Style, Snapchat has strung together a run of viral AR Lenses as consistently as Beyoncé drops hits songs. The latest example is Smile, an AR Lens that, according to a Snap spokesperson, uses a machine-learning algorithm to morph a person's like ...more
Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful prac ...more
Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people ar ...more
Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, sk ...more
Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show. What Is a Buffer Over ...more
Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I s ...more
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exp ...more
An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires. Before you keep reading, know that this project is not geared ...more
When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular p ...more
People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the out ...more
You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discove ...more
There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're conc ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the ...more
While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we ha ...more
The camera situation on the all new HTC One is a little daunting. The M8 has not one, not two, but three camera lenses built in. First, there's the 5 megapixel selfie machine up front, then around back, there's the new Duo Camera with a refined UltraPixel sensor. HTC has done ...more
A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open. So, how would y ...more
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physi ...more
Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than othe ...more
Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to prote ...more
So, the in-person conversations between you and your friends has slowed down to a near halt, thanks to everyone's obsession with texting, Facebook, and over-uploading pics to Instagram—socializing at its best. It could also be that you're just not interesting enough anymore in ...more
You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ign ...more
There is no iPad version of Apple's Calculator app, so you won't find it on your Home Screen, in your App Library, or as a shortcut in the Control Center. But that doesn't mean your iPad doesn't have an official calculator. Before the first iPad in 2010, Apple's development t ...more
Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them ...more