What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, ...more
The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely. The sheer volume of Windows computers currently in operation around the world ...more
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us ...more
Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we ...more
Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you ...more
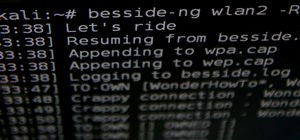
There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture hands ...more
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manuf ...more
The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other device ...more
More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered. Passwords are normally ...more
Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple ap ...more
Yosemite is definitely an improvement over Mavericks, but there are still some painfully obvious and annoying bugs that occur within certain apps. One such example is the elongated "Open" and "Save" dialog boxes, which sometimes stretch all the way down so that the "Open," "S ...more
Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of ...more
If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it. Now, thanks to a tutorial from tihmstar, you can downgrade the op ...more
Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to ...more
The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac ...more
If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning e ...more
This video tutorial demonstrates an easy way to activate MMS on iPhone 3G or 3Gs Firmware 3.1 o. First download the File here. Now Make Sure itunes is closed and not running. On Mac: 1. Close iTunes if it is open 2. Start Terminal (Applications - Utilities) 3. Run the foll ...more
Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools a ...more
This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting ...more
Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, a ...more
Google TV gives the new Chromecast a home screen full of curated content from your various streaming subscriptions, but it's just that — a home screen app. Underneath, Google's new dongle is running Android TV, meaning its home screen is just a launcher that can be installed o ...more
A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer ...more
One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somew ...more
By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions. We've spent the last few days getting to know it, and let ...more
No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly! I hope you had a good Christmas and happy new year! Update1: Added the section "weaponizing your Android" where I talk about apps and fundamental Kali ...more
Thanks to online music services like eMusic and iTunes, compact discs are becoming a far distant memory, turning local music shops around the country into desolate wastelands. The once mighty movie rental store Blockbuster is now bankrupt because of online streaming services l ...more
We all want a faster, more efficient web browsing experience. Some immediately flocked to Google Chrome as soon as it was released, because of its super fast speeds. Others restrained themselves and continued to wait for Microsoft and Mozilla to play catchup. And the time is a ...more
The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat. There is one thing that would make the phone even bet ...more
Apple may have made Mavericks more accessible to Mac users everywhere at the fair price of zero dollars, but unfortunately, they made it trickier to create a bootable install drive of the Mac OS X 10.9 operating system. Don't Miss: How to Create a Bootable Install Drive of 10 ...more
Android 7.1.1 stock images for the Nexus 6P were released last week on December 5, 2016. However, Verizon users seem to have been excluded from the update. Google's factory image page states "All carriers except Verizon" next to version number NMF26F. This doesn't seem fair, e ...more
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's ...more
Up until now, enabling full-time Immersive Mode on an Android device has been a tedious task which required you to run individual ADB commands each time you wanted to toggle it on or off. This was a shame, too, since Immersive Mode helps reclaim lots of screen real estate by a ...more
One of the biggest features to come out with Android O was the addition of a new System UI Tuner submenu that lets you customize the navigation bar at the bottom of your phone's screen. But as it turns out, this same feature can be enabled on devices running Android Nougat, ev ...more
Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly al ...more
The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. Thi ...more
It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually brin ...more
When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a so ...more
Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the ...more
Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scann ...more
A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular. Every goo ...more
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby devi ...more
The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized ...more
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or ...more
If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock ...more
Sometimes, the volume buttons on a MacBook can be pretty annoying. It's too loud, so you turn it down one notch, and now you can't hear your movie at all. It's too low, so you turn it up one notch, and now you can't even hear yourself think. But, there's something a lot of Ma ...more
If you're seeing "damaged" apps on your Mac, you're not alone. A huge digital rights management blunder in Apple's Mac App Store on Wednesday, November 11th has rendered some apps unusable. When opening certain apps, the following message could be displayed: "[App Name]" is d ...more
Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus a ...more
Greetings my fellow hackers. As you may have noticed by my lack of posts, I've been away for a while working on a big project with a team (which won't be finished anytime soon), and I have also been putting together a small side project for Null-Byte that I will be announcing ...more
Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you con ...more
Sharing a laptop's wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topolog ...more
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that ...more
Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new ...more
Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on ...more
Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID ...more
Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't en ...more
Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason. Make sure to check out Part 1 and ...more
Back for the second part, Just to recap in part one, we installed and configured the dhcp server. This will allow us to pass our clients requests out to the internet. This is a very important step in the evil twin attack because if your targets (clients) can't make it out to ...more
Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listenin ...more
In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmles ...more